While web browsing I constantly glance for the padlock symbol to indicate that the site is encrypting any of my form data by using the https prefix, which means that an SSL (Secure Sockets Layer) certificate is being used by the web hosting company. I have peace of mind knowing that my credit card information cannot be easily stolen on secure web sites using an SSL certificate. For Ethernet networks there are also several potential security breaches:
- Man-in-the-middle attacks
- Eavesdropping
- Denial of service
- Privilege escalation
The downside risks of data theft are quite high to any organization, and being compliant with data security standards like Health Insurance Portability and Accountability Act of 1996 (HIPAA) in the US and the General Data Protection Regulation (GDPR) are important.
To detect and prevent any unwanted data intrusions a system must have privacy measures like source validation and authentication.
Secure Ethernet Protocol
Thankfully, the IEEE created the Media Access Control Security (MACsec) protocol in 2006 to help secure Ethernet networks. The cryptography used to protect Ethernet traffic in MACsec is Advanced Encryption Standard-Galois/Counter Mode Cryptography (AES-GCM), also used for CXL and PCI Express security. MACsec is applied at Layer 2 of the Open Systems Interconnection (OSI) networking model, enabling data integrity, confidentiality, replay protection and data origin authenticity.
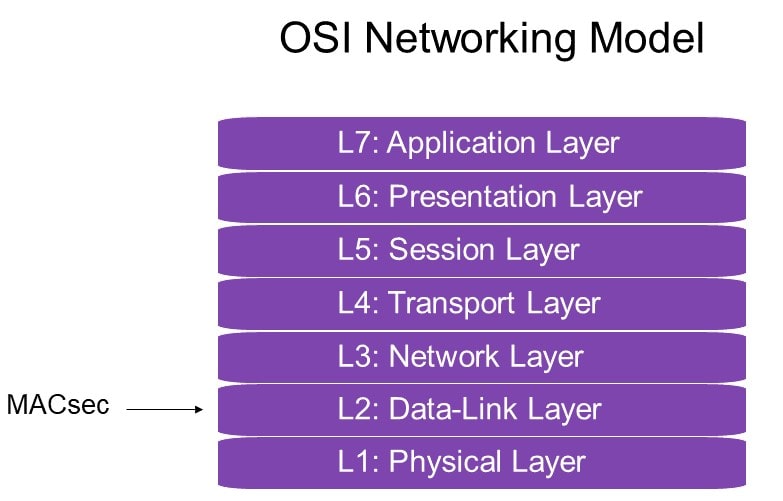
The encrypted connection with MACsec has several authentication steps:
- A Pre-Shared Key (PSK) for mutual peer authentication.
- A secure Connectivity association Key Name (CKN) is exchanged.
- The two endpoints decide which is the key server, and key client.
- The key server sends the Secure Association Key (SAK) to the key client.
- Encrypted data is ready for exchange.
You could take the time to become an expert on MACsec and design your own Ethernet security solution that conforms to the protocol, or consider using Ethernet IP from Synopsys that in addition to controllers and PHYs includes their MACsec Security Modules. Here’s what the Ethernet security IP from Synopsys looks like:
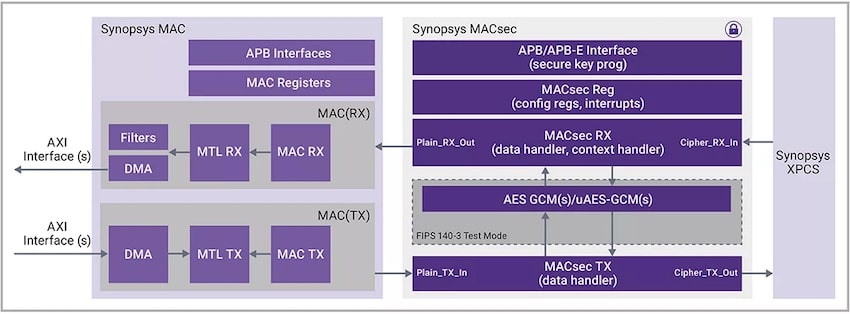
The benefits of using the Synopsys MACsec Security Modules include compliance with the IEEE 802.1AE standard, throughput scalability and configurability to tune solutions for specific applications and use cases with optimal latency, power, performance and area.
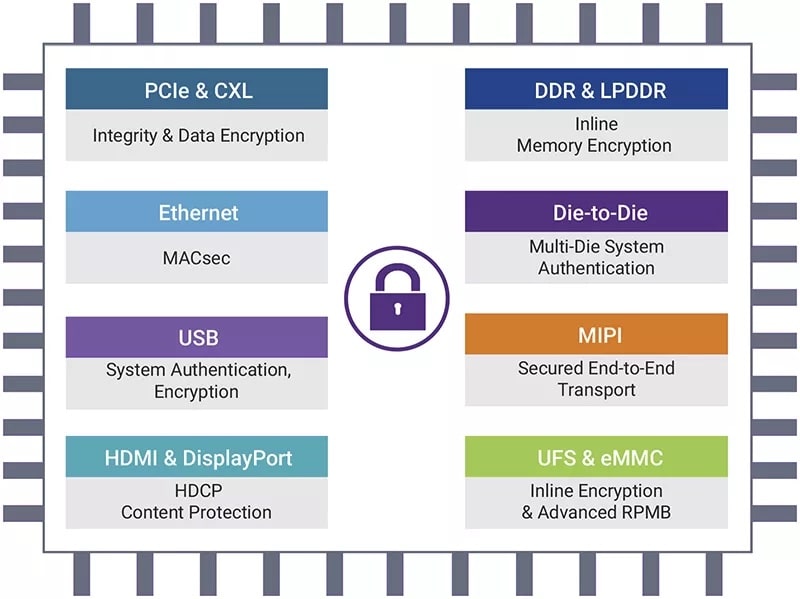
Synopsys not only has secure IP for Ethernet, it also extends into other interfaces: PCIe, CXL, USB, HDMI, DisplayPort, DDR, LPDDR, Die-to-Die, MIPI, UFS and eMMC.
Kalar Rajendiran wrote more about this topic in his January blog on SemiWiki.
Summary
Having a secure Ethernet makes a lot of sense, and with the IEEE protocol MACsec there’s a standard way to ensure that network data is not stolen or compromised. Malicious actors want to steal our web browsing activity and that extends into the realm of Ethernet traffic.
Instead of waiting to have your Ethernet data breached, why not be proactive by adding the MACsec protocol in your SoC implementation. Do the math on the cost of building your own MACsec compliant IP, then compare that to what Synopsys has designed and verified already. The semiconductor IP industry has grown steadily for many years now, and for good reason, IP blocks from a trusted vendor can offer a faster path to market while not requiring your engineering team to become domain experts in something new and unfamiliar.
Related Blogs
- Synopsys Accelerates First-Pass Silicon Success for Banias Labs’ Networking SoC
- Feeding the Growing Hunger for Bandwidth with High-Speed Ethernet
- Multi-Die Systems: The Biggest Disruption in Computing for Years
- How to Efficiently and Effectively Secure SoC Interfaces for Data Protection






Comments
There are no comments yet.
You must register or log in to view/post comments.