In the previous blog, Cybercriminals Next Targets: Short Term Dangers (part 1 of 2), I outlined how cybercriminals will use the holiday season to victimize unwary consumers and target businesses. They will also dive deeper into leveraging Internet-of-Things (IoT) devices. The longer-term outlook expands their reach to more… Read More
Cybercriminals Next Targets: Short Term Dangers (part 1 of 2)
Knowing what cybercriminals are targeting today is easy. Their attacks are loud, impactful, and have the elegance of a herd of bulls crashing through a glassware shop. The tougher challenge is figuring out where they will take aim tomorrow. Knowing where cyber threats will attack in the future, gives the necessary insights to … Read More
3 Reasons Why is Cybersecurity Losing
Cyber threats are currently outpacing the defenders but it does not need to be the case. Attacks are increasing in number and type, with the overall impacts are becoming greater. Cybersecurity is struggling to keep our digital lives and assets protected from the onslaught of attacks but facing great challenges. By understanding… Read More
Hack This? Making Software a Moving Target
It sometimes seems that the black hats are always one step ahead of the white hats in the never-ending security game. One of the especially invidious ways hackers have found to evade detection is through mutation – changing the code in a virus on each copy, defeating classical signature detection methods and potentially requiring… Read More
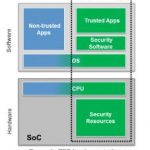
How to Secure a SoC while Keeping Area and Power Competitive?
I have attended LETI conference last June and remember the paper presented by Alain Merle, their security guru. Alain said that smart cards are secured because up to 50% of the Silicon area is dedicated to security. When you design a SoC to address applications like smart metering, NFC payment or embedded SIM, you know in advance … Read More
The New Reality for IoT Security
Recent Distributed Denial of Service (DDoS) attacks are forcing a shift in Internet-of-Things (IoT) security thinking. The dangers are expanding as attackers are taking advantage of billions of IoT devices, conscripting them into their botnet armies for massive DDoS attacks.… Read More
IoT Tech from Iowa
When you see Iowa and IoT in a title, you probably think of agricultural applications and Iowa as a consumer. In fact, they have their own pretty active tech development culture especially around Des Moines. Certainly some of this is focused on agtech, but there are also players in fintech, payment tech, health-tech, business automation,… Read More
Where hackers take their money – Casinos, Cryptocurrency, and Virtual Worlds
Cybercrime is reaching epidemic levels. Some estimates predict global annual cybercrime costs will reach $6 trillion by 2021. This includes the costs of security as well as the losses from thefts and fraud from successful attacks. Criminals are finding themselves in a position of having gained electronic assets but need to transform… Read More
Webinar: Improve Security For IoT Edge Devices With Custom SoCs
The only thing hotter than IoT on SemiWiki.com right now is IoT Security. In 2016 we saw a record amount of reported cyber security breaches with compelling consequences (US Presidential Election) and that trend will continue. The most recent DDoS (distributed denial of service) attacks using botnets on insecure IoT devices … Read More
IoT Worms Could Spread Like Zombies
Security researchers recently created a proof-of-concept attack against Internet connected lightbulbs, causing breached devices to reach out and infect their neighbors. Propagation continues and spreads itself across the community. This hack highlights the insecurity in one of many IoT network protocols.
Researchers… Read More


A Detailed History of Samsung Semiconductor