You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
WP_Term Object
(
[term_id] => 97
[name] => Security
[slug] => security
[term_group] => 0
[term_taxonomy_id] => 97
[taxonomy] => category
[description] =>
[parent] => 0
[count] => 335
[filter] => raw
[cat_ID] => 97
[category_count] => 335
[category_description] =>
[cat_name] => Security
[category_nicename] => security
[category_parent] => 0
[is_post] =>
)
No doubt many who read this article have heard the expression “You can’t get there from here…” It’s most often attributed to New Englanders – primarily residents of Maine – to describe a route to a destination that is so circuitous and complex that one needn’t bother embarking on the journey.
In the context of the business world, the… Read More
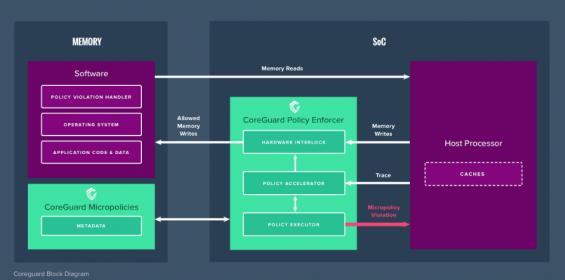
One of the companies I met at ARM TechCon was Dover Microsystems who offer a product in embedded security. You might ask why we need yet another security solution. Surely we’re overloaded with security options from ARM and many others in the forms of TEEs, secure boots, secure enclaves and so on? Why do we need more? Because defending… Read More
Digital technology continues to connect and enrich the lives of people all over the globe and is transforming the tools of everyday life, but there are risks accompanying the tremendous benefits. Entire markets are committed and reliant on digital tools. The entertainment, communications, socialization, and many others sectors… Read More
Security and machine learning (ML) are among the hottest areas in tech, especially for the IoT. The need for higher security is, or should be, blindingly obvious at this point. We struggle to fend off daily attacks even in our mainstream compute and networking environment. How defenseless will we be when we have billions of devices… Read More
Unique device identities are at the core of all computer security systems. Just as important is that each unique identity cannot be copied, because once copied they can be used illegitimately. Unique device IDs are used to ensure that communications are directed to the correct device. And they also provide the ability to encrypt… Read More
I read with interest the US Chamber of Commerce’s assessment of the Made in China (MIC) 2025 plan to transform the world’s most populous nation into an Advanced Manufacturing leader. MIC 2025 covers 10 strategic industries that China identifies as critical to economic growth in the 21[SUP]st[/SUP] century, including next-gen… Read More
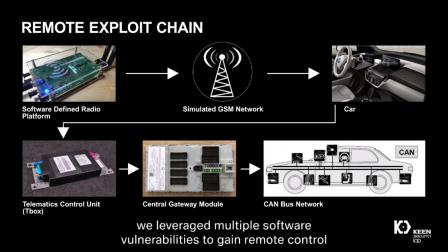
The cybersecurity of automobiles has become an increasingly critical issue in the context of autonomous vehicle development. While creators of autonomous vehicles may have rigorous safety and testing practices, these efforts may be for naught if the system are compromised by ethical or unethical hackers.
Establishing cybersecurity… Read More
I don’t know if it was just me but I left TechCon 2017 feeling, well, uninspired. Not that they didn’t put on a good show with lots of announcements, but it felt workman-like. From anyone else it would have been a great show, but this is TechCon. I expect to leave with my mind blown in some manner and it wasn’t. I wondered if the SoftBank … Read More
ARM TechCon is one of the most influential conferences in the semiconductor ecosystem without a doubt. This year ARM TechCon has moved from the Santa Clara Convention Center to the much larger convention center in San Jose. Last year the conference seemed to be busting at the seams so this move makes complete sense. A little less … Read More
Potential for Hack-Back Legislation. Government officials and experts are weighing in on the concept of ‘hacking back’, the practice of potentially allowing U.S. companies to track down cyber attackers and retaliate.
Former head of the CIA and NSA outlined his thoughts to the Fifth Domain on the Hack Back issue currently being… Read More










Memory Matters: Signals from the 2025 NVM Survey