Maheen Hamid, a member of the ESD Alliance (a SEMI Technology Community) Governing Council and a member of SEMI’s North America Advisory Board, is an astute business executive. Together with her husband Adnan Hamid, they founded Breker Verification Systems, a company developing test synthesis solutions. She serves today … Read More
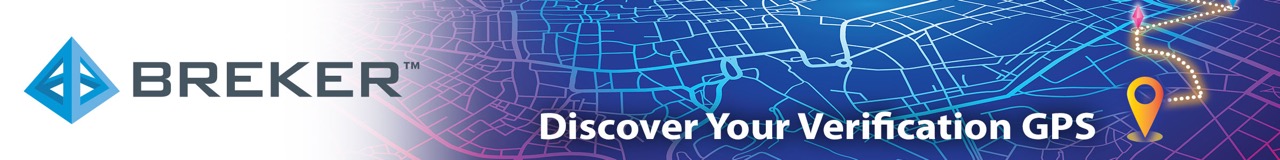
Scaling the RISC-V Verification Stack
The RISC-V open ISA premise was clearly a good bet. It’s taking off everywhere, however verification is still a challenge. As an alternative to Arm, the architecture and functionality from multiple IP providers looks very competitive, but how do RISC-V providers and users ensure the same level of confidence we have in Arm? Arm … Read More
Breker Verification Systems Unleashes the SystemUVM Initiative to Empower UVM Engineering
The much anticipated (virtual) DVCON 2022 is happening this week and functional verification plus UVM is a very hot topic. Functional Verification Engineers using UVM can enjoy a large number of benefits by synthesizing test content for their testbenches. Abstract, easily composable models, coverage-driven content, deep… Read More
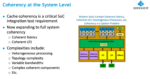
Breker Attacks System Coherency Verification
The great thing about architectural solutions to increasing throughput is that they offer big improvements. Multiple CPUs on a chip with (partially) shared cache hierarchies are now commonplace in server processors for this reason. But that big gain comes with significant added complexity in verifying correct behavior. In… Read More
Podcast EP53: Breker’s New CEO Weighs in on the Company, DAC and the Future of Verification
Dan is joined by Dave Kelf, who was recently appointed CEO of Breker Verification Systems. Dave discusses Breker’s unique approach to verification of complex systems, what its future impact will be and what Breker will be doing at DAC.
The views, thoughts, and opinions expressed in these podcasts belong solely to the
Podcast EP13: The Three Pillars of Verification with Adnan Hamid
Dan goes on a scenic tour of verification with Adnan Hamid, founder and CEO of Breker Verification Systems. We discuss the rather unusual way Adnan got into semiconductors and SoC verification. Adnan then breaks down the verification task into its fundamental parts to reveal what the three pillars of verification are and why … Read More
WEBINAR: Adnan on Challenges in Security Verification
Adnan Hamid, CEO of Breker, has an interesting background. He was born in China to diplomat parents in the Bangladesh embassy. After I’m sure an equally interesting childhood, he got his BSEE/CS at Princeton. Where, like most of us he had to make money on the side, in his case working for a professor in the Psych lab on artificial intelligence… Read More
Breker Tips a Hat to Formal Graphs in PSS Security Verification
It might seem paradoxical that simulation (or equivalent dynamic methods) might be one of the best ways to run security checks. Checking security is a problem where you need to find rare corners that a hacker might exploit. In dynamic verification, no matter how much we test we know we’re not going to cover all corners, so how can it… Read More
Verification, RISC-V and Extensibility
RISC-V is obviously making progress. Independent of licensee signups and new technical offerings, the simple fact that Arm is responding – in fundamental changes to their licensing model and in allowing custom user extensions to the instruction set – is proof enough that they see a real competitive threat from RISC-V.
Which all… Read More
Build More and Better Tests Faster
Breker has been in the system test synthesis game for 12 years, starting long before there was a PSS standard. Which means they probably have this figured out better than most, quite simply because they’ve seen it all and done it all. Breker is heavily involved in and aligned with the standard of course but it shouldn’t be surprising… Read More