
For decades, One-Time Programmable (OTP) memory has been viewed as a foundational element of hardware security. Because OTP can be written only once and cannot be modified afterward, it has traditionally been trusted to store cryptographic keys, secure boot code, device identity, and configuration data. Permanence was often equated with security. In today’s threat environment, however, that assumption no longer holds. While OTP is extremely effective at preventing modification, it does not inherently prevent extraction. As attackers shift their focus from changing data to reading it, OTP must evolve from a permanent storage mechanism into part of a broader, hardware-rooted secure storage architecture.
Why Hardware-Rooted Secure Storage Matters for OTP IP
OTP excels at protecting integrity: once data is programmed, it cannot be altered. What it does not guarantee on its own is confidentiality. If secrets are stored directly in OTP in plaintext form, a sufficiently capable attacker with physical access may still be able to observe or extract those bits using advanced techniques. This distinction is critical. OTP prevents rewriting, but it does not automatically prevent reading. In modern systems, where physical access is often assumed and attacks routinely target hardware, permanence alone is no longer enough. Hardware-rooted secure storage addresses this gap by ensuring that even if memory contents are accessed, the underlying secrets remain protected and unusable.
What Next-Generation OTP Must Address
As SoCs become more complex, valuable, and widely deployed, next-generation OTP solutions must explicitly address the growing gap between immutability and secrecy. Storing static secrets directly in OTP creates an increasingly attractive target for attackers. Security must instead be device-specific, resilient against physical and invasive attacks, and scalable across large, heterogeneous SoCs. OTP can no longer be treated as “secure by default”; it must be embedded within an architecture that assumes attackers may eventually reach the hardware and still prevents meaningful compromise.
Closing the Security Gap with a Layered Defense Model
The most effective way to protect OTP in modern designs is through a layered defense model that combines multiple hardware-based security mechanisms. In this approach, secrets are not stored directly in OTP. Instead, a hardware-generated, device-unique root key is derived from the intrinsic physical characteristics of the chip itself and is never stored anywhere on the device. Cryptographic engines then use this root key to encrypt and decrypt data stored in OTP, while secure control logic manages access and policy enforcement. As a result, OTP holds only encrypted assets, not usable secrets. Even if an attacker succeeds in reading OTP contents, the data remains unintelligible without the regenerated, chip-specific key. This layered model fundamentally changes the security posture of OTP, transforming it from static memory into a protected vault anchored in silicon.
Building In Security for Scaling, Mission-Critical SoCs
Industries such as AI and high-performance computing, automotive, IoT, and aerospace increasingly deploy SoCs in environments where attacks are assumed and failures can have serious safety, financial, or national-security consequences. These systems demand security that is present from the very first instruction and remains effective throughout the product lifecycle. Hardware-rooted secure storage enables secure boot, prevents device cloning and counterfeiting, binds identity and policy enforcement to individual chips, and locks down debug and configuration pathways after manufacturing. Most importantly, it allows security to scale alongside SoC complexity, ensuring consistent protection across subsystems without relying on software-only assumptions.
Synopsys’ Secure Storage Solution for OTP IP
Synopsys addresses the limitations of traditional OTP with its Secure Storage Solution for OTP IP, which is designed specifically to solve the problem of permanent but readable memory. The solution integrates antifuse-based OTP with Synopsys SRAM Physical Unclonable Function (PUF) technology, an on-chip cryptographic engine, and a secure controller. At power-up, the SRAM PUF regenerates a unique root key derived from the silicon itself. This key is never stored and exists only transiently within the hardware. It is used internally to encrypt and decrypt data stored in OTP, ensuring that secrets are never exposed in plaintext at any point in the system.
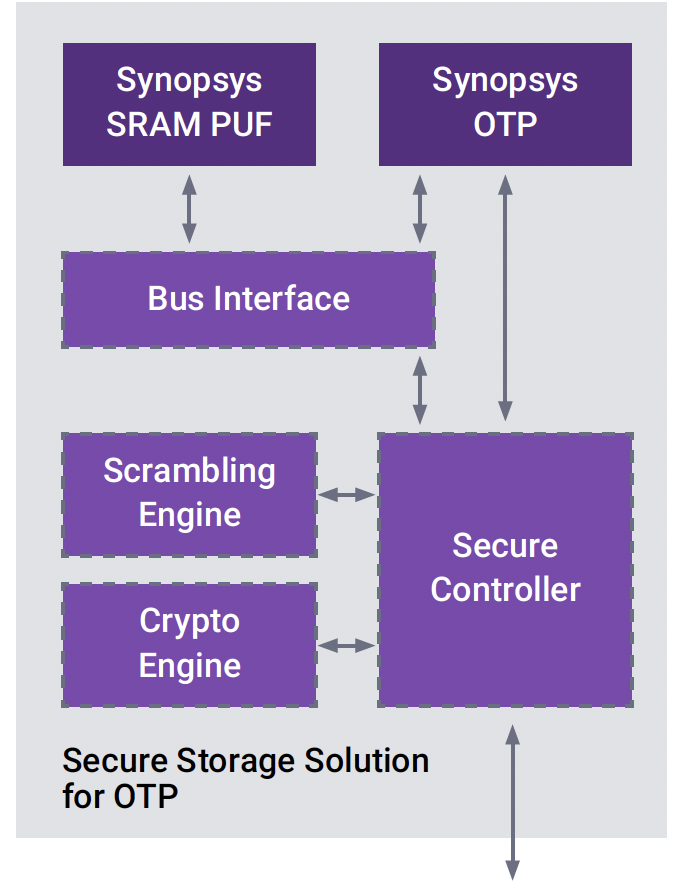
Advantages, Ease of Integration, and Flexible Configuration
Beyond strong security, the Secure Storage Solution for OTP IP is designed for practical deployment in real-world SoCs. Delivered as a pre-integrated subsystem with a standard AMBA APB interface, it minimizes integration effort and risk. Flexible configuration options allow designers to protect OTP alone or extend hardware-rooted protection across the entire chip, depending on system requirements. The solution abstracts cryptographic complexity behind a simple software interface and automatically initializes keys and protections at power-up, reducing provisioning complexity and deployment risk. By eliminating the need for custom security architectures, the solution helps teams accelerate time-to-market while scaling robust, consistent security across product lines.
Summary
OTP remains a critical component of SoC security, but the industry can no longer assume that data which cannot be changed also cannot be compromised. Modern threat models require security that protects confidentiality as well as integrity, even under physical attack. Hardware-rooted secure storage closes this gap by ensuring that secrets are never stored directly and are instead derived from the silicon itself. By combining OTP with device-unique key generation and cryptographic protection, designers can establish a true root of trust that scales with modern SoCs and meets the demands of mission-critical applications. In today’s systems, OTP provides permanence, but hardware-rooted secure storage provides protection. Both are required to build lasting trust in silicon.
To learn more, visit Synopsys’ Secure Storage Solution for OTP IP page.
Also Read:
Curbing Soaring Power Demand Through Foundation IP
TSMC based 3D Chips: Socionext Achieves Two Successful Tape-Outs in Just Seven Months!
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.