Semiconductor intellectual property (IP) plays a critical role in modern system-on-chip (SoC) designs. That’s not surprising given that modern SoCs are highly complex designs that leverage already proven building blocks such as processors, interfaces, foundational IP, on-chip bus fabrics, security IP, and others. This… Read More
Tag: physical unclonable function
Synopsys SNUG Silicon Valley Conference 2024: Powering Innovation in the Era of Pervasive Intelligence
After the leadership transition at the top, Synopsys had just a little more than two months before the company’s flagship event, the Synopsys User Group (SNUG) conference. The Synopsys user community and entire ecosystem were waiting to hear new CEO Sassine Ghazi’s keynote to learn where the company is going and its strategic … Read More
Quantum Computing and Threats to Secure Communication
There is never a dearth of new terms, discoveries and inventions in the technological world. And sometimes existing terms get reinvigorated. And debates ensue. The debaters argue about the plusses and minuses and make some predictions. Such is the case with “Quantum Computing.” I recently watched and listened to a webinar that… Read More
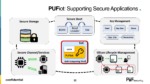
Upcoming Webinar: PUFiot, A NeoPUF-based Secure Co-Processor
Throughout history, people have sought after security as a basic right and expectation within a civilized society. Even as recent as a few centuries ago, things were very simple. Subjects looked to their rulers to provide security for their lives and assets. Assets were mostly hard assets such as jewelry, coins or real estate. … Read More
IoT Collateral Damage – it’s not if, but when
Business history is littered with once-successful companies that couldn’t see the market tsunami that was coming their way until it was too late to do anything but stand up and be walloped by a wave of change that obliterated their businesses.
… Read More
PUF the Magic (IoT) Dragon
Most people are familiar with Biometrics, the measurement of unique physical characteristics, such as fingerprints, and facial features, for the purpose of verifying human identity with a high level of certainty. The iris and even a person’s electrocardiogram (ECG) can be used as a secure biometric identifier.… Read More