 Succeeding at managing cybersecurity risks is tremendously difficult even for seasoned professionals. To make situations worse, poorly suited people are often chosen to lead security organizations, bringing about disastrous results. This has contributed to weaker risk postures for organizations and the rapid turnover in cybersecurity leadership.
Succeeding at managing cybersecurity risks is tremendously difficult even for seasoned professionals. To make situations worse, poorly suited people are often chosen to lead security organizations, bringing about disastrous results. This has contributed to weaker risk postures for organizations and the rapid turnover in cybersecurity leadership.
I am unhappy to report that the industry has a pervasive problem that few want to discuss: a propensity to enlist inexperienced or unsuitable professionals to lead cybersecurity. It is time to change that caustic and enabling behavior by first recognizing the problem.
As an example, recently in the news, there was criticisms for someone appointed with the responsibility to lead the cybersecurity effort for the 2020 Olympics, but had “never used a computer”. How does someone who has never used a computer and has difficulty answering basic questions about USB drives, be tasked with building a cybersecurity program to protect the digital security, privacy, and safety for hundreds of thousands of people?
Downward Spirals
Sadly, I have seen similar situations play-out over and over again across academia, business, and government sectors. Far too often, poorly suited people are appointed such roles and it simply does not make sense. Let’s be clear, most are truly knowledgeable and accomplished in their primary field, but a transition to security is a significantly different domain. Engineering and product management executives focus mostly on static problems where there is a solution and desired end-state. Whereas in cybersecurity, we face a highly dynamic set of threat agents, people who are creative, intelligent, motivated, and dynamic, who will adapt to any solution. There is no permanent fix for cybersecurity as it is an ongoing competition to managing risks between defenders and attackers.
Human nature, overconfidence, and a lack of understanding the challenges begins to shape a counterproductive mindset. It is common for a professional from a different discipline, transplanted and put in charge of cybersecurity, to believe their prior expertise is equally applicable to the new challenges. Somehow, magically, they think they are as proficient and insightful at an adjacent domain as their previous profession. To those experienced in adversarial challenges who have seen this unfold, it is an affront to common sense. It is no surprise that such dangerous situations most often result in momentous failure.
For years, the turnover rate in cybersecurity leadership positions across the industry has been very high, with most Chief Information Security Officers (CISO) only lasting 2 to 4 years. When surveyed, CISO’s cite a lack of executive management support or insufficient budgets were the pervasive motivators. But that is only one side of the story as many CISO’s have been let go.
I have always been curious what C-suites and board had to say. When I ask company leaders about a change in cybersecurity leadership, I often hear that an outgoing CISO was ineffective, could not communicate risks well, and demanded significant budget increases every year yet the organization did not show a commensurate benefit. Events culminated when a severe incident occurred and then the C-suite or board chose to find a new security leader.
With the shortage of CISO’s in the industry, those displaced quickly find another company and continue their ‘training’. This musical-chairs routine does not serve the company or overall industry needs very well and simply transplants problems from one organization to another.
Masters of All
This mistake occurs regularly with technical personnel, probably as cybersecurity is generally characterized as a technology problem by the unacquainted. An accomplished engineer or architect is put in charge of security and now with ‘cybersecurity’ in front of their title they truly believe they are a risk expert. They are not. Being savvy in technology vulnerabilities and exploits is far different than understanding the massive breadth involved in managing risk. Most are unwilling to admit their shortsightedness in the breadth and depth of the challenges and their arrogance simply becomes a hinderance to seeking the needed help to be successful.
Ego can be such a major hindrance when the fear, of being perceived as not understanding a problem or knowing an answer, limits your actions. It is typical for a person in such a quandary to retreat back to familiar areas they know, resulting in defining the problem and solution only in the terms of technology. This ignores the behavioral, adversarial, and process aspects that are crucial to managing risk. With blinders on, they continue to push forward regardless, thus the car wreck begins.
Cybersecurity is more than just a ‘tech’ problem and will never be ‘solved’ with technology alone (two pervasive misconceptions from engineers first joining cybersecurity). They are likely doomed. I have seen this happen countless times and can spot it a mile away. It is like an automobile accident happening in slow motion with an overconfident driver continuing to push forward as metal bends and glass shatters.
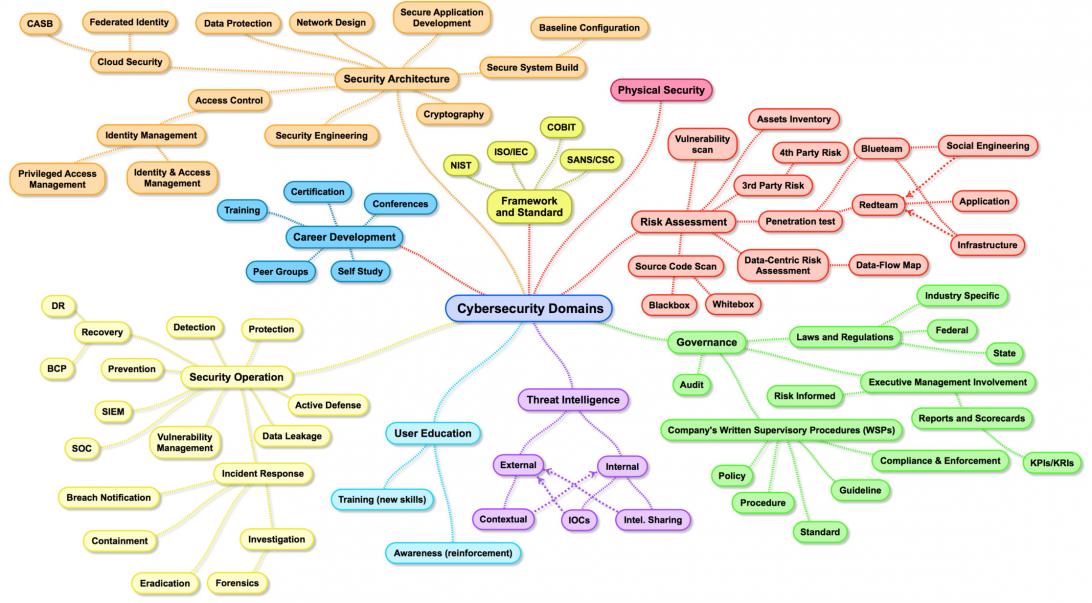
Enlarged Version of Cybersecurity Domains
Part of the issue is that people, who are experts in one field, assume they understand the entire problem set in another adjacent but ambiguous field. It is not until they are in the new role, that they then experience the unforeseen challenges of a different world.
Imagine a hospital. Would you promote the engineer who developed a defibrillation tool to be an emergency room doctor? No. Although tools and technology play a crucial role in medicine, it is not the same as predicting, preventing, detecting, and responding to health risks for patients across their lifespan. The same applies in cybersecurity.
Technology is the battlefield, not the war. Understanding the terrain is important, but must be combined with a keen assessment of your opponents, and the ability to operationally maneuver in advantageous ways.
This is true in other fields as well. Aeronautical engineers aren’t promoted to fighter pilots and textbook publishers aren’t necessarily good grade school principals, so why do organizations make the mistake of a taking a software engineer or business-line product manager and expect them to be successful in leading cybersecurity?
Two Scenarios: Vastly Different Chances for Success
Now, I did say this is a recipe for failure most of the time. There are some, very rare situations, where an insightful but inexperienced person takes a cybersecurity leadership role and succeeds. It is possible. I have only seen it a handful of times and in every case that person was realistic about their knowledge and checked their ego at the door.
Guaranteed Failure:
An engineer, project manager, or business executive is put in charge of cybersecurity. They are confused or intimidated by security practitioners in their organization and respond by immediately surrounding themselves with like-minded, yet similarly security inexperienced people. They add other engineers, marketing, and legal people to their core echelon, inadvertently creating a self-reinforcing ineffective group-think team. Congratulations, an inexperienced leader has just encircled themselves with a cushion of people who don’t have the knowledge to challenge poor directives or independently deliver sustainable success. If you wonder what conversations with them are like, take a look at the Dilbert cartoon, specifically the ‘manager’ character. That is pretty close. Funny from afar, but frustrating up close.
Ineffectual organizations tend to grow fast, spend a lot of money, make hollow promises, tell a story of difficult times that are turning around, but have no real strategic plan, prioritized goals, or clearly defined scope with organizational roles and responsibilities. They seek non-existent cure-all solutions, and their long-term stratagem is to hope nothing bad happens while they battle daily issues. Even worse, the proficient security personnel, that may have been part of the team, will likely leave such a caustic environment for a better employer. That breaks my heart when I see capable people who want to make a difference, driven away. When quality employees begin jumping-ship en-masse, it is a sure warning sign.
The easiest way to detect this situation early on, is to look at their metrics, or lack thereof. If a security organization operates without the benefit of tangible metrics, it is a likely sign they have not defined or are not tracking against goals, roles, objectives, and probably aren’t measuring or tracking risk. What they are doing is responding to issues, self-marketing, rapidly growing the team, consuming significant resources, slowing down the business, and the looking for people to blame when their ineffectiveness becomes apparent. These orgs don’t last. They implode. People quickly leave and executive oversight will soon look past the whitewash to cut budgets, headcount, and eventually replace the leaders.
Potential for Success:
An engineer, project manager, or business executive is put in charge of cybersecurity. They understand they are not a security expert, so they assemble a team who has experience and talent in protecting digital assets, understanding threats, can articulate risks, and are intimate with the technology in use. They build an organization structure that is comprised of operations, engineering, and risk intelligence teams. Then listen and learn. Great leaders bring in the best people and let them excel. They quickly get clarification on the business goals and expectations from executives and customers. They then identify prioritized objectives, define a scope, derive the supporting measurable goals, identify areas in need of immediate attention, and establish the measures & metrics necessary to track progress.
Governance issues are addressed and a strategic process capability is embedded to constantly improve the organizations risk management ability to predict, prevent, detect, and respond to threats. They establish both the tactical plans necessary for immediate survival and day-to-day management, but also define a long-term directional strategy that takes into account the ever-evolving threat landscape, technology changes, and shifting expectations for security, privacy, and safety.
Proficient security workers thrive in such organizations and rarely leave. With a strong plan and capable team in place, leaders can effectively communicate and advocate across the organization. If all of these elements land in place, with the proper support, even an inexperienced security leader can have a chance at success.
Unfortunately, it rarely happens.
Failure is Expensive
Cybersecurity is difficult. It becomes exponentially more problematic when someone who lacks the necessary mentality or skills comes in and makes it profoundly worse. Cleaning up an ineffective legacy security program is painful, expensive, and time consuming. Simultaneously, a poor risk posture opens the door to more attacks and greater impacts until a capable security program is instituted.
We must understand that cybersecurity, like many other highly specialized roles, requires a depth of insight and experience to lead. I will echo Sun Tzu’s “…do what is great while it is small” and recommend putting a good leader in place the first time to build an effective and sustainable cybersecurity organization.
Let’s all break the silence and openly discuss the cycle of poor cybersecurity leadership, for everyone’s benefit.
For more insights on the challenges and required strategic deliverables, read my post Cybersecurity Fails Without Strategy.
Share this post via:






Advancing Automotive Memory: Development of an 8nm 128Mb Embedded STT-MRAM with Sub-ppm Reliability