In today’s digital landscape, data security has become an indispensable feature for any data transfer protocol, including Peripheral Component Interconnect Express (PCIe). With the rising frequency and sophistication of digital attacks, ensuring data integrity, confidentiality, and authenticity during PCIe transport is crucial. To address these concerns, technologies like Security Protocol and Data Models (SPDM) have emerged as key enablers for secure communication. Component Measurement and Authentication (CMA) determines how SPDM is applied to PCIe systems. By employing these frameworks alongside advanced cryptographic techniques, such as elliptic curve cryptography (ECC), PCIe systems can safeguard sensitive data against potential threats. Siemens EDA recently published a whitepaper on this very topic.
CMA and SPDM: Foundations of PCIe Security
CMA and SPDM play a vital role in fortifying PCIe connections. Together, they establish secure sessions, authenticate communication endpoints, and facilitate encrypted data exchanges. SPDM achieves these goals by defining a series of messages that enable secure connections between devices. These messages negotiate protocol versions, advertise device capabilities, and determine supported cryptographic algorithms. Handshake secrets are generated using hash functions such as HMAC and HKDF, which are critical for encrypting and decrypting communication. After the successful exchange of SPDM requests, a secure session is established.
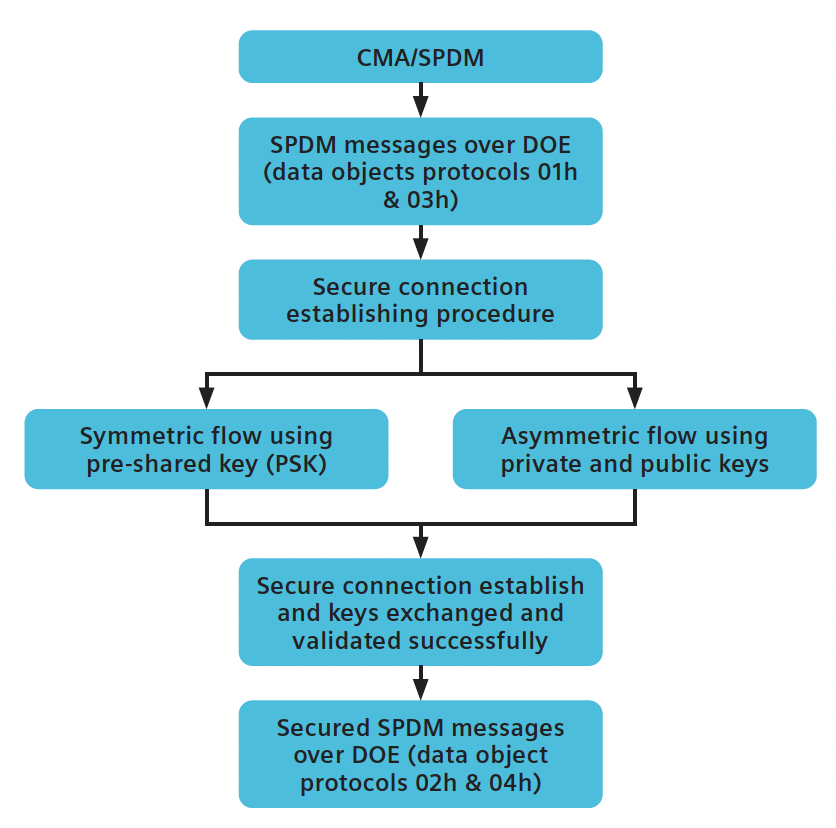
Symmetric vs. Asymmetric SPDM Flows
Symmetric Encryption: This method relies on a Pre-Shared Key (PSK) known to both parties before initiating communication. It is computationally efficient but requires secure key distribution beforehand.
Asymmetric Encryption: Public/private key pairs are used to eliminate the need for pre-shared keys. This approach enables stronger authentication mechanisms, such as digital signatures, ensuring that communication endpoints are verified.
SPDM supports both symmetric and asymmetric encryption flows to establish secure connections. While symmetric encryption is faster and less resource-intensive, asymmetric encryption provides superior security and solves key distribution challenges.
Key Generation and Authentication Techniques
Key generation is an essential part of the SPDM flow, with the Diffie-Hellman Key Exchange (DHE) algorithm playing a central role. The algorithm facilitates secure key exchanges by leveraging shared secrets generated during the handshake process.
Elliptic Curve Cryptography (ECC) enhances the DHE algorithm by performing complex operations on elliptic curves, enabling faster and more secure key generation. Authentication within SPDM is achieved through digital signatures, which validate the origin and integrity of transmitted data. By combining message hashing with encryption using a private key, digital signatures ensure that only authorized entities can participate in communication.
Advantages of Elliptic Curve Cryptography
Elliptic curve cryptography has gained prominence due to its ability to deliver equivalent security to traditional algorithms like RSA while requiring significantly smaller key sizes. This efficiency makes ECC particularly suited for resource-constrained environments like PCIe systems. For example, an ECC 256-bit key provides the same level of security as a 3072-bit RSA key, reducing computational overhead and improving performance. The smaller key sizes also simplify key management and accelerate cryptographic operations, making ECC an attractive choice for modern PCIe security.
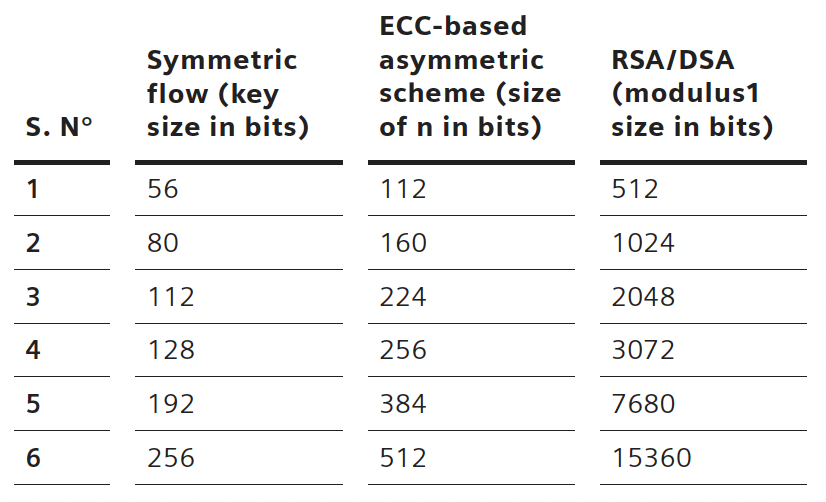
Strengthening Security with ECC Algorithms
Elliptic curve cryptography further strengthens the security of PCIe transport by offering computational advantages over conventional methods. Its reliance on solving complex elliptic curve equations makes it resistant to cryptanalysis while reducing processing requirements. This efficiency allows for faster encryption and decryption, as well as quicker digital signature generation. Additionally, ECC’s smaller key sizes make it easier to maintain and manage cryptographic keys, ensuring seamless integration into PCIe systems.
Verification with Siemens VIP for PCIe
To ensure the successful implementation of CMA/SPDM, Siemens Verification IP (VIP) for PCIe provides a comprehensive framework for design verification. This solution is fully compliant with CMA Revision 1.1 and SPDM Version 1.3.0, offering robust testing capabilities for secure PCIe communication. Siemens VIP supports the generation of SPDM messages required to establish secure connections, along with APIs that enable flexible stimulus generation. Users can modify fields to create diverse test cases, covering both positive and negative scenarios.
Error injection and debugging are additional strengths of Siemens VIP, allowing designers to simulate fault conditions and analyze system behavior. The solution also supports both symmetric and asymmetric encryption flows, enabling a wide range of testing scenarios. Algorithms such as secp256r1 and secp384r1 are supported for Diffie-Hellman key generation, while digital signature algorithms like TPM_ALG_ECDSA_ECC_NIST_P256 ensure robust authentication. Moreover, Siemens VIP accommodates various device configurations, making it adaptable to the diverse capabilities advertised by different PCIe components.
Summary
CMA and SPDM provide a robust framework for PCIe security, enabling encrypted communication and authentication between devices. The integration of advanced cryptographic techniques, such as ECC, enhances these protocols by offering efficient and secure key generation, digital signatures, and encryption. Siemens Verification IP for PCIe ensures compliance with these security standards, offering extensive testing and debugging capabilities. Together, these technologies establish a new benchmark for PCIe transport security, protecting sensitive data against emerging threats in the digital age.
The whitepaper can be accessed here.
Also Read:
Reset Domain Crossing (RDC) Challenges
Electrical Rule Checking in PCB Tools
Innexis Product Suite: Driving Shift Left in IC Design and Systems Development
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.