The Internet of Things (IoT) is an ecosystem of ever-increasing complexity; it’s the next wave of innovation that will humanize every object in our life, and it is the next level of automation for every object we use. IoT is bringing more and more things into the digital fold every day, which will likely make IoT a multi-trillion dollar industry in the near future. To understand the scale of interest in the internet of things (#IoT) just check how many conferences, articles, and studies conducted about IoT recently, this interest has hit fever pitch point in 2016 as many companies see big opportunity and believe that IoT holds the promise to expand and improve businesses processes and accelerate growth.
However, the rapid evolution of the IoT market has caused an explosion in the number and variety of IoT solutions, which created real challenges as the industry evolves, mainly, the urgent need for a secure IoT model to perform common tasks such as sensing, processing, storage, and communicating. Developing that model will never be an easy task by any stretch of the imagination, there are many hurdles and challenges facing a real secure IoT model.
The biggest challenge facing IoT security is coming from the very architecture of the current IoT ecosystem; it’s all based on a centralized model known as the server/client model. All devices are identified, authenticated and connected through cloud servers that support huge processing and storage capacities. The connection between devices will have to go through the cloud, even if they happen to be a few feet apart. While this model has connected computing devices for decades and will continue to support today IoT networks, it will not be able to respond to the growing needs of the huge IoT ecosystems of tomorrow.
The Blockchain Model
Blockchain is a database that maintains a continuously growing set of data records. It is distributed in nature, meaning that there is no master computer holding the entire chain. Rather, the participating nodes have a copy of the chain. It’s also ever-growing — data records are only added to the chain.
When someone wants to add a transaction to the chain, all the participants in the network will validate it. They do this by applying an algorithm to the transaction to verify its validity. What exactly is understood by “valid” is defined by the Blockchain system and can differ between systems. Then it is up to a majority of the participants to agree that the transaction is valid.
A set of approved transactions is then bundled in a block, which gets sent to all the nodes in the network. They, in turn, validate the new block. Each successive block contains a hash, which is a unique fingerprint, of the previous block.
Principles of Blockchain Technology
Here are five basic principles underlying the technology:
1. Distributed Database
Each party on a blockchain has access to the entire database and its complete history. No single party controls the data or the information. Every party can verify the records of its transaction partners directly, without an intermediary.
2. Peer-to-Peer Transmission
Communication occurs directly between peers instead of through a central node. Each node stores and forwards information to all other nodes.
3. Transparency
Every transaction and its associated value are visible to anyone with access to the system. Each node, or user, on a blockchain has a unique 30-plus-character alphanumeric address that identifies it. Users can choose to remain anonymous or provide proof of their identity to others. Transactions occur between blockchain addresses.
4. Irreversibility of RecordsOnce a transaction is entered in the database and the accounts are updated, the records cannot be altered, because they’re linked to every transaction record that came before them (hence the term “chain”). Various computational algorithms and approaches are deployed to ensure that the recording on the database is permanent, chronologically ordered, and available to all others on the network.
5. Computational Logic
The digital nature of the ledger means that blockchain transactions can be tied to computational logic and in essence programmed. So users can set up algorithms and rules that automatically trigger transactions between nodes.
Public vs. Private Blockchain
Blockchain technology implementation can be public or private with clear differences, for example the benefits offered by a private blockchain are: faster transaction verification and network communication, the ability to fix errors and reverse transactions, and the ability to restrict access and reduce the likelihood of outsider attacks. The operators of a private blockchain may choose to unilaterally deploy changes with which some users disagree. To ensure both the security and the utility of a private blockchain system, operators must consider the recourse available to users who disagree with changes to the system’s rules or are slow to adopt the new rules. While, developers who work to maintain public blockchain systems like bitcoin still rely on individual users to adopt any changes they propose, which serves to ensure that changes are only adopted if they are in the interest of the entire system.
Just as a business will decide which of its systems are better hosted on a more secure private intranet or on the internet, but will likely use both, systems requiring fast transactions, the possibility of transaction reversal, and central control over transaction verification will be better suited for private blockchain, while those that benefit from widespread participation, transparency, and third-party verification will flourish on a public blockchain.
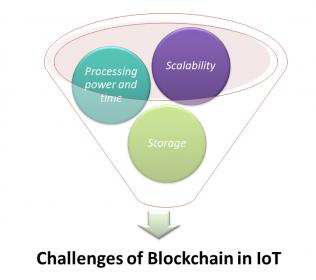
Challenges of Blockchain in IoT
In spite of all its benefits, the Blockchain model is not without its flaws and shortcomings:
Scalabilityissues; relating to the size of Blockchain ledger that might lead to centralization as it’s grown over time and required some kind of record management which is casting a shadow over the future of the Blockchain technology.
Processing power and time; required to perform encryption algorithms for all the objects involved in Blockchain -based IoT ecosystem given the fact that IoT ecosystems are very diverse and comprised of devices that have very different computing capabilities, and not all of them will be capable of running the same encryption algorithms at the desired speed.
Storagewill be a hurdle; Blockchain eliminates the need for a central server to store transactions and device IDs, but the ledger has to be stored on the nodes themselves, and the ledger will increase in size as time passes. That is beyond the capabilities of a wide range of smart devices such as sensors, which have very low storage capacity.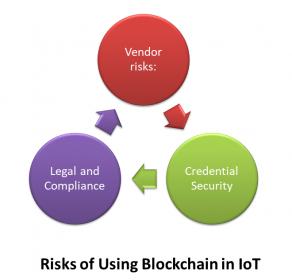
Risks of Using Blockchain in IoT
It goes without saying that any new technology comes with new risks. An organization’s risk management team should analyze, assess and design mitigation plans for risks expected to emerge from implementation of blockchain based frameworks.
Vendor Risks: Practically speaking, most present organizations, looking to deploy blockchain based applications, lack the required technical skills and expertise to design and deploy a blockchain based system and implement smart contracts completely in-house, i.e. without reaching out for vendors of blockchain applications. The value of these applications is only as strong as the credibility of the vendors providing them. Given the fact that the Blockchain-as-a-Service (BaaS) market is still a developing market, a business should meticulously select a vendor that can perfectly sculpture applications that appropriately address the risks that are associated with the blockchain.
Credential Security:Even though the blockchain is known for its high security levels, a blockchain based system is only as secure as the system’s access point. When considering a public blockchain based system, any individual has access to the private key of a given user, which enables him/her to “sign” transactions on the public ledger, will effectively become that user, because most current systems do not provide multi-factor authentication. Also, loss of an account’s private keys can lead to complete loss of funds, or data, controlled by this account; this risk should be thoroughly assessed.
Legal and Compliance:It’s a new territory in all aspects without any legal or compliance precedents to follow, which poses a serious problem for IoT manufacturers and services providers. This challenge alone will scare off many businesses from using Blockchain technology
The Optimum Secure IoT Model
In order for us to achieve that optimal secure model of IoT, security needs to be built-in as the foundation of IoT ecosystem, with rigorous validity checks, authentication, data verification, and all the data needs to be encrypted at all levels, without a solid bottom-top structure we will create more threats with every device added to the IoT. What we need is a secure and safe IoT with privacy protected. That’s a tough trade-off but possible with Blockchain technology if we can overcome its drawbacks.
Ahmed Banafa Named No. 1 Top VoiceTo Follow in Tech by LinkedIn in 2016. Read more articles at IoT Trends by Ahmed Banafa
Share this post via:






CEO Interview with Jerome Paye of TAU Systems