On 2021, a British/Polish firm known as Walletmor announced that it had become the first company to sell implantable payment microchips to everyday consumers. While the first microchip was implanted into a human way back in 1998, says the BBC News—so long ago it might as well be the Dark Ages in the world of computing—it is only recently… Read More
Tag: ahmed banfa
Edge Computing Paradigm
Edge computing is a model in which data, processing and applications are concentrated in devices at the network rather than existing almost entirely in the cloud.
Edge Computing is a paradigm that extends Cloud Computing and services to the of the network, similar to Cloud, Edge provides data, compute, storage, and application… Read More
Thick Data vs. Big Data
One of the challenges facing businesses in post-COVID-19 world is the fact that consumer behavior won’t go back to pre-pandemic norms. Consumers will purchase more goods and services online, and increasing numbers of people will work remotely just to mention few major changes . As companies begin to navigate the post-COVID-19… Read More
What is a Data Lake?
“Data Lake” is a massive, easily accessible data repository for storing “big data”. Unlike traditional data warehouses, which are optimized for data analysis by storing only some attributes and dropping data below the level aggregation, a data lake is designed to retain all attributes, especially when you do… Read More
What is Zero Trust Model (ZTM)
The Zero Trust Model of information #security simplifies how #information security is conceptualized by assuming there are no longer “trusted” interfaces, applications, traffic, networks, or users. It takes the old model— “trust but verify”—and inverts it, because recent breaches have proven that when an organization trusts,… Read More
8 Key Tech Trends in a Post-COVID-19 World
COVID-19 has demonstrated the importance of digital readiness, which allows business and people’s life to continue as usual during pandemics. Building the necessary infrastructure to support a digitized world and stay current in the latest technology will be essential for any business or country to remain competitive in a … Read More
Ten Trends of Blockchain in 2020
It’s clear that blockchain will revolutionize operations and processes in many industries and governments agencies if adopted, but its adoption requires time and efforts, in addition blockchain technology will stimulate people to acquire new skills, and traditional business will have to completely reconsider their processes… Read More
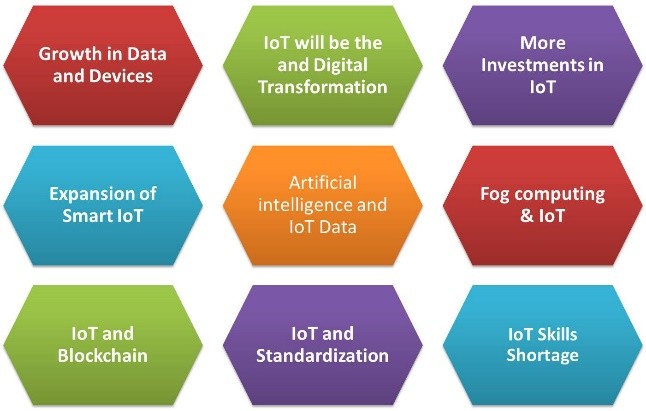
9 IoT Predictions for 2019
By 2020, the Internet of Things (IoT) is predicted to generate an additional $344B in revenues, as well as to drive $177B in cost reductions. IoT and smart devices are already increasing performance metrics of major US-based factories. They are in the hands of employees, covering routine management issues and boosting their productivity… Read More
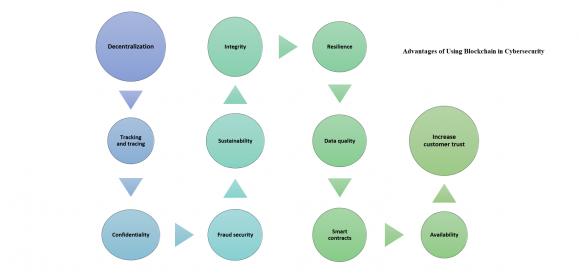
Second Line of Defense for Cybersecurity: Blockchain
In the first part we covered AI as the first line of defense for cybersecurity, the goal was to keep the cyber-criminals at bay, but in case they managed to get-in and infiltrate the network we need to initiate the second line of defense; #Blockchain. With the fact that cybercrime and cyber security attacks hardly seem to be out of the… Read More
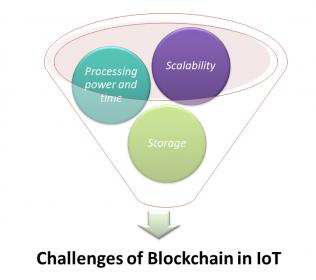
IoT and Blockchain: Challenges and Risks
The Internet of Things (IoT) is an ecosystem of ever-increasing complexity; it’s the next wave of innovation that will humanize every object in our life, and it is the next level of automation for every object we use. IoT is bringing more and more things into the digital fold every day, which will likely make IoT a multi-trillion dollar… Read More