It used to be that automotive theft and crime was perpetrated with a crowbar. Now with increased electronics content, car designer and owners need to worry about electronic threats. Anywhere there is a communication link or a processor, there are potential threats to the security of the car. The range of these threats covers everything from privacy, safety, malicious intent, damage or even vehicle theft. Automotive suppliers are taking these threats seriously and designing their products with security in mind up front.
On the privacy front, hackers could listen in as you speak inside your car, or they could track your location. Every automated system could be tampered with from door locks, to safety critical systems such as airbags and crash avoidance. Hacked motor and automotive control systems could be harmed by improper commands.
Cars are coming with more and more data connections to the outside world, ones that could be exploited by hackers or malicious actors. The question is, what can be done to minimize security vulnerabilities in connected cars? Synopsys has a technical bulletin that discusses the fundamental problem and ways to deal with it. The paper written by Mike Borza, Principle IP Security Technologist at Synopsys, is titled “Minimizing Security Vulnerabilities in Connected Cars Starts with Silicon”.
They posit that by 2023 there will be over 70 million connected cars on the road. Each one of them will have multiple connections that could be used to compromise their security. This can range from USB, SD, AUX connections to WiFi, Bluetooth, and embedded modem devices. With new smart car functionality, comes increasing pathways in and out of the vehicle. Prevention of these threats requires a ground up approach starting at the SOC level to ensure security.
Two significant types of breaches are installation of hacked software and intercepted or falsified communications. Synopsys asserts that the best way to protect software integrity is to build security into the silicon that it is running on. Using Hardware Root of Trust can enable the creation of a Trusted Execution Environment (TEE). Synopsys’ approach is to provide SOC developers an IP Hardware Security Module (HSM) that offers an isolated secure processing enclave that serves as the center of chip security.
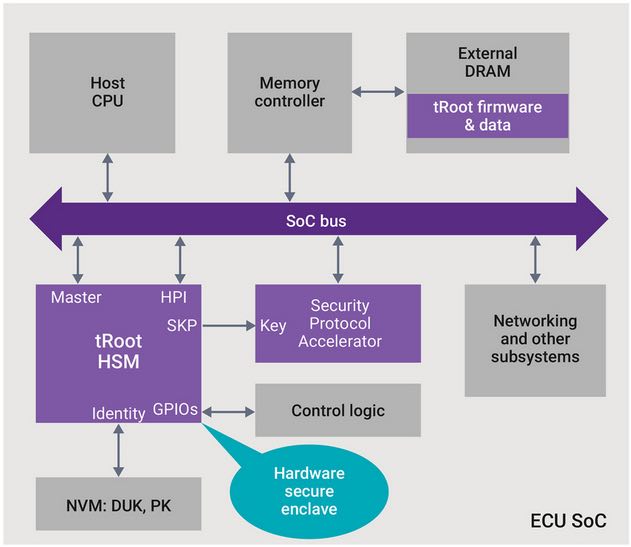
The HSM contains a set of secure services to enable unique chip identification, encryption and application code validation. At startup, the HSM is the first unit that begins operating, it can then validate its own code and then ensure that any application code run on other processors in the system have not been tampered with. Once the SOC is up and running the HSM can provide encryption API’s that make possible secure and authorized communication within and outside of the vehicle.
Synopsys calls its hardware security module tRoot HSM. It offers complete IP for implementing a TEE and also is supported by software libraries and development tools that enable SOC designers to build a complete hardware/software solution and also perform debug and ensure post production test.
The Synopsys Technical Bulletin delves into the details of how tRoot HSM IP can contribute to making SOCs targeted for automotive use as secure as possible. One key take-away is that it’s important to have a complete system that includes all the components, from hardware IP to software, to ensure robust security.
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.