Synopsys hosted a tutorial on the last day of DVCon USA 2022 on design/system dependability. Which here they interpret as security, functional safety, and reliability analysis. The tutorial included talks from DARPA, AMD, Arm Research and Synopsys. DARPA and AMD talked about general directions and needs, Arm talked about their PACE reliability analysis technique and Synopsys shared details on solutions they already have and aligning standards in safety and security.
DARPA on practical strategies for security in silicon
Serge Leef (PM DARPA) provided insight into the DARPA focus on scalable defense mechanisms in electronics, particularly trading off cost versus security. They’re targeting not the big semis or consumer electronics guys but rather mid-sized semis and defense companies, who are most interested in getting help. The ultimate goal in the project that Serge oversees is automatic synthesis of secure silicon (AISS). No-one ever accused DARPA of thinking small.
Synopsys, Northrop Grumman, Arm and others have been selected to drive this effort. A security engine, developed in a different part of the program will be integrated together with commercial IP and security aware tools. In a phased approach to full automation, initially systems will be composed around these various IP. A second phase optimization will be configured within a platform-based architecture. In the final phase they aim to be able to specify a cost function around power, area, speed and security (PASS). Allowing system teams to dial in the tradeoff they want.
As I said, an ambitious goal, but this is the organization that gave us the Internet after all 😀.
AMD on functional safety
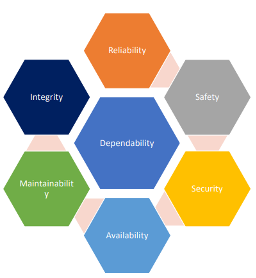
Bala Chavali is an RAS architect at AMD (RAS is reliability, availability and serviceability/ maintainability). Her main thesis in this talk was the challenge in meeting objectives across multiple dependability goals, each with their own standards and expectations. She breaks these down into reliability, safety, security, availability and maintainability.
In part the challenges arise from disconnected standards, lifecycle requirements and required compliance work products across these multiple objectives. In part challenges come from lack of enough standards on IP suppliers, particularly around safety, security, and traceability.
Bala underscored the importance of unifying these objectives as much as possible to minimize duplicated effort. She sees value in aligning common standards efforts, for example in defining a generic dependability development lifecycle. This should leverage a wholistic analysis data set. Also a common data exchange language across applications (automotive, industrial, avionics, and across the system design hierarchy). Bala mentioned the Accellera functional safety working group (on which she serves) as one organization working towards this goal, also IEEE P2581 as another with a similar objective.
Arm Research on PACE reliability analysis
Reiley Jeyapaul, Senior Research engineer at Arm Research, talked about using formal tools for reliability estimation on a Cortex-R52 using their proof-driven architecturally correct execution (PACE) methodology. Their objective is to estimate the fraction of their design which is vulnerable to soft errors (random failures) to produce an architecture vulnerability factor (AVF). They suggest this as a model to derate the estimated FIT rate. This factor is needed since not all naïve vulnerabilities are real (if an error does not propagate), or may in some cases be only conditionally vulnerable. Arm will license PACE models to partners for their use in system vulnerability assessments.
Reiley provides detail on their formal technique and how they validated this method against exhaustive fault injection (EFI). Models are a little pessimistic, but not as pessimistic as the naïve model, and run dramatically faster than EFI. Sounds like a valuable capability for SoC designers.
Synopsys on automation for safety and security
Meirav Nitzan, director of functional safety and security solutions at Synopsys, closed the tutorial. She summed up capabilities offered by Synopsys for safety and security, in tools and IP and across both software and hardware design. I’m not going to attempt to summarize that long list. I think their selection for the DARPA AISS program is endorsement enough. I will call out a few points that I found interesting to my predominantly hardware audience.
We all know tools and IP suites in this area. To this they add SW test libraries for safety and software security analysis for 3rd part SW running on HW. They also provide virtual prototyping for developing secure SW. They use fault simulation for FMEDA analyses of course. I also found it interesting that they support fault modeling for malicious attacks, also sample fault simulation in emulation. Which I would guess would be valuable in testing vulnerability to probing attacks.
Meirav wrapped by reiterating the work IEEE P2581 is doing; to align security and safety requirements, a worthy goal for all of us. Learn more about Synopsys’ solutions for mission-critical silicon and software development HERE.
Also read:
Synopsys Announces FlexEDA for the Cloud!
Use Existing High Speed Interfaces for Silicon Test
Getting to Faster Closure through AI/ML, DVCon Keynote
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.