RISC-V cores are popping up everywhere. The growth of this open instruction set architecture (ISA) was quite evident at the recent RISC-V summit. You can check out some of the RISC-V buzz on SemiWiki here. While all this is quite exciting and encouraging, there are hurdles to face before true prime-time, ubiquitous application of RISC-V processors are commonplace. A big one is certification. I’m not referring to verification of the design, but rather certification of the RISC-V ISA implementation. Does the processor reliably do what is expected across its broad range of applications? Can we trust these devices?
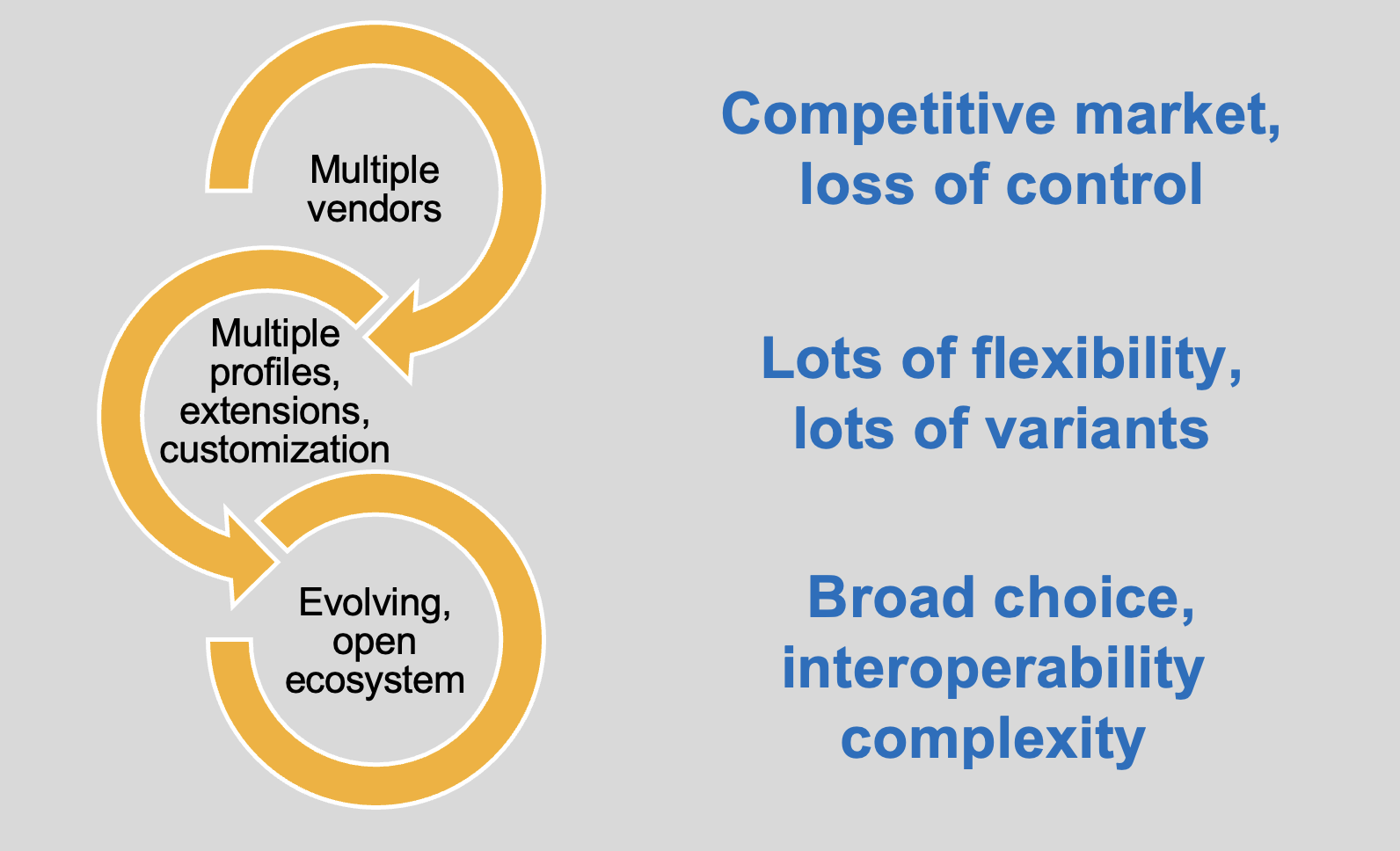
It turns out this is a large and complex problem. The graphic at the top of this post illustrates its breadth. Solving it is critical to allow broad deployment of the RISC-V architecture. I decided to poke around and see what was being done. Breker has “verification” in the company name, so it seemed that would be a good place to start. I contacted my good friend Dave Kelf and I wasn’t disappointed. There is a lot going on here and Breker is indeed in the middle of a lot of it. Let’s see how Breker is helping to solve the RISC-V certification problem.
The CEO Perspective

I’ve known Dave Kelf a long time. He is currently CEO of Breker Verification Systems. Dave explained there are a lot of RISC-V design efforts underway at large companies, startups and advanced research. These programs include open-source projects, commercial programs and universities. He told me Breker alone is being used in 15 RISC-V development programs underway at present.
Dave explained that in the processor world, there are devices from companies such as Arm, Intel and AMD that come with a certification from the vendor. These devices undergo extensive testing. This creates a level of “comfort” that the device will perform as advertised under all conditions. The tests done by these companies can take on the order of 1015 clock cycles to run. That is indeed a mind-boggling statistic.
Dave provided an overview of what is involved in certifying a processor architecture like RISC-V. He explained that it’s important to understand that this task is a lot more complex than certifying a point-to-point communication protocol (think Wi-Fi). It’s also a lot broader than verifying a specific processor design. Before the processor gets that golden stamp of approval, it needs to be checked for all potential use cases, not just the one being used on a particular design.
The architecture of the certification test suite needs to be developed and agreed to by a steering committee that has a sufficiently broad ecosystem perspective. Then the actual tests need to be built and verified. Then comes the task of running the certification suite. Do companies self-certify, or does an independent lab do that work? And finally, how is all this funded?
A complex and daunting set of problems to solve, but this kind of proof of capability is what will be needed to achieve mainstream use across a broad range of applications for RISC-V. The good news is that RISC-V International has taken up the cause. Dave explained that after the RISC-V Summit last year work began. So, this project is about 10 months old. Breker, along with many other members of the RISC-V community is providing support and effort to realize these important goals.
Dave explained that there was a presentation on this work at the recent RISC-V Summit. This presentation filled in a lot more details for me.
The President and CTO Perspective

Adnan Hamid, Executive President and CTO at Breker gave the presentation on RISC-V certification. As mentioned, this effort started after last year’s RISC-V Summit. It is being driven at the RISC-V International Board level. A key part of the RISC-V organization is the technical steering committee (TSC). This is where all the details for components of the RISC-V ecosystem are developed, both hardware and software. A certification steering committee (CSC) has been created that exists at a peer level to the TSC. One way to think about this is that the CSC has the mandate to check the TSC to ensure a coherent path to certification can be developed. The diagram below illustrates the entities involved in the program. The goal is to deliver holistic brand value.
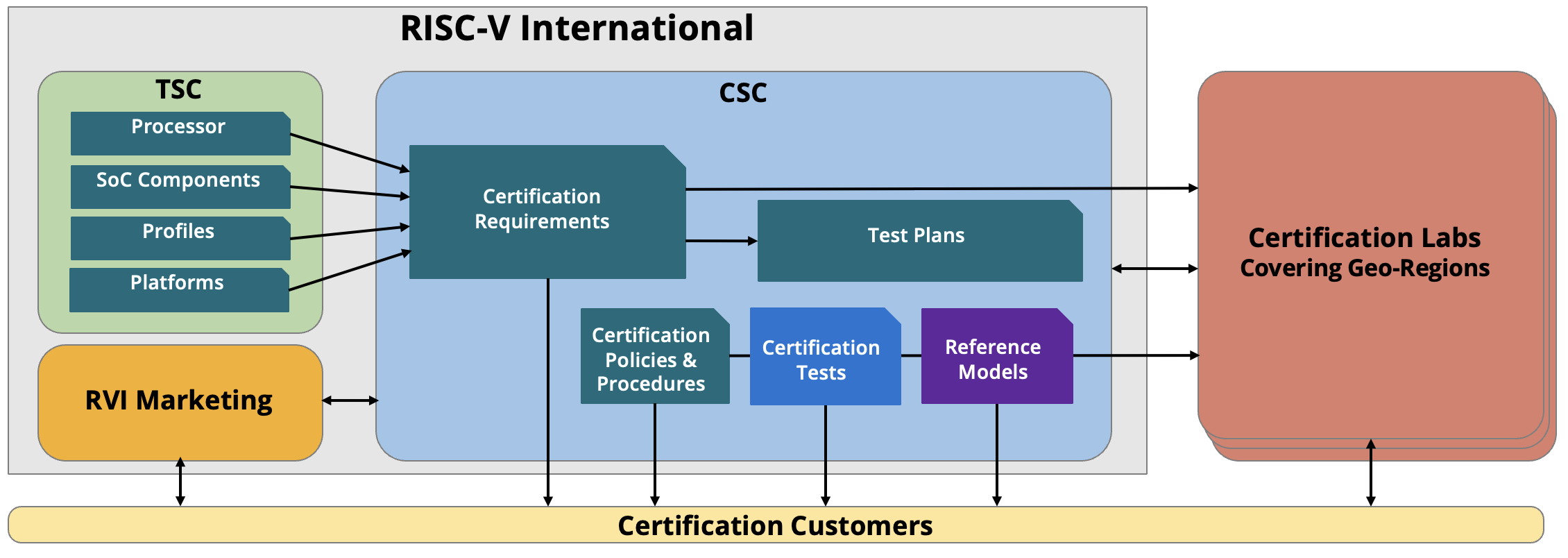
Adnan shared some of the details of the program. Although it is still early days, these are likely to include:
- Allows implementations to ensure compliance with RISC-V standards
- Goal is to provide confidence to the RISC-V ecosystem that it will correctly operate on certified implementations
- Certifies processors, SoC components, and platforms
- Certifies RTL and silicon
- Includes commercial-grade certification materials
- Customers pay to obtain certificate
- Fee based on certification cost
- “RISC-V Compatible” Branding Program
- Certificate must meet customer requirements
- Must be available in a timely fashion
- Must be based on ratified RVI standards
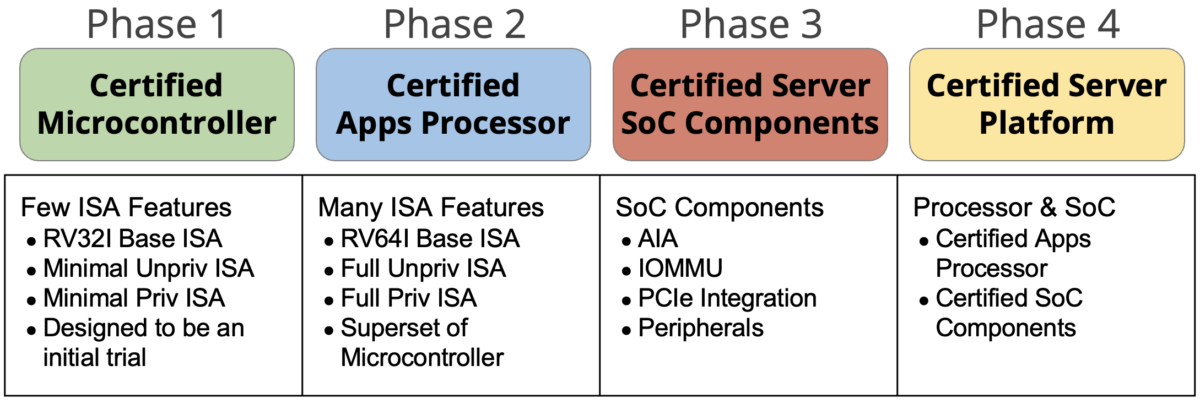
Certification is planned to be done in phases as shown below.
The CSC is taking shape. It currently has the following five working groups:

You can see a recording of the full presentation Adnan gave here.
Dave and Adnan are actively involved in the Customer Survey and Tests & Models groups. There are about 24 companies involved in this effort so far, and that number is growing.
How You Can Help
There is a lot being done on RISC-V certification. And a lot more to do as well. If you’re like most folks in semiconductors today, you are thinking seriously about how the open architecture of RISC-V could help. If you are interested in RISC-V, the certification team wants to hear from you. They need your input which will be used to shape this program. There is a survey underway to better understand your needs.
Let your voice be heard. You can access the survey here. Do it today! And that’s how Breker is helping to solve the RISC-V certification problem.
Also Read:
Breker Brings RISC-V Verification to the Next Level #61DAC
System VIPs are to PSS as Apps are to Formal
Breker Verification Systems at the 2024 Design Automation Conference
Share this post via:




Comments
There are no comments yet.
You must register or log in to view/post comments.