The year 2017 wasn’t a great year for cyber-security; we saw a large number of high-profile cyber attacks; including Uber, Deloitte, Equifax and the now infamous WannaCry ransomware attack, and 2018 started with a bang too with the hackingof Winter Olympics. The frightening truth about increasingly cyber-attacks is … Read More
A Development Lifecycle Approach to Security Verification
We have become accustomed to the idea that safety expectations can’t be narrowed down to one thing you do in design. They pervade all aspects of design from overall process through analysis, redundancies in design, fault analytics and mitigation for faults and on-board monitors for reliability among other requirements and techniques.… Read More
Securing embedded SIMs
If you have a phone, you probably know it has a SIM card, for most of us the anchor that ties us into a 2/3-year plan with one network provider, unless you have an unlocked phone. Even then, you have to mess around swapping SIM cards if you travel overseas. Wouldn’t it be nice if the SIM was embedded and could be switched though an app or an… Read More
Data Security – Why It Might Matter to Design and EDA
According to the Economist, “The world’s most valuable resource is no longer oil, but data”. Is this the case?Data is the by-product ofmany aspects of recent technology dynamics and is becoming the currency of today’s digital economy. All categories in Gartner’s Top10 Strategic Technology Trends for 2018 (Figure… Read More
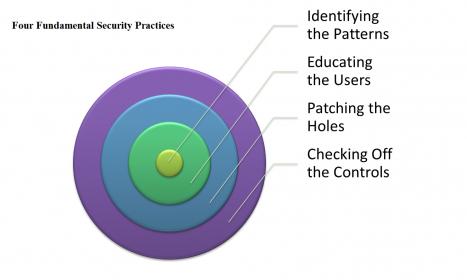
How many engineers does it take to get an IoT security certificate?
Spoiler alert, the answer is none!
Let me take you back to the beginning to explain that answer.
For the sake of this discussion, I will reduce a complex IoT solution to three fundamental blocks:
- IoT node
- IoT Gateway
- IoT Server
The IoT node is a sensor that converts analog, physical world context into digital data. The node has to have… Read More
Achieving ISO 26262 Certification with ASIL Ready IP
According with McKinsey, “analysts predict revenue growth for advanced driver assistance systems (ADAS) to be up to 29 percent, giving the segment one of the highest growth rates in the automotive and related industries.” Design cycle in automotive segment is much longer than in segments like mobile, PC or consumer. If you expect… Read More
Cryptocurrency is the New Target for Cybercriminals
As predicted, the rise of cryptocurrency valuation has captured the attention of cybercriminals. New hacks, thefts, misuse, and fraud schemes are on the rise. Where there is value, there will be a proportional risk of theft.Criminals always pursue and exploit systems where they can achieve personal financial gain. It is the … Read More
Lipstick on the Digital Pig
I have a lot of friends in the real estate industry, and two of the most common sales tactics are to create “curb appeal,” and to “stage” the interior of the residence being sold. Curb appeal, of course, refers to making the home looks as appealing as possible upon first impression. Update the landscaping. Add flowers. Make sure the… Read More
Synopsys White Paper on IoT Security – Introduces DesignWare Root-of-Trust Module
As the internet of things (IoT) continues its climb to a trillion devices, there has been many articles and books written on the need for securing those devices. With all the IoT gear that I seem to be picking up as Christmas presents, I feel like I’m doing my part to help the market get there, but I have to say, I sure hope the SoC designers… Read More
Top Cybersecurity Concerns Are WRONG
A recent survey by Varonis of 500 security professionals from the U.S., UK, and France highlights the top three cybersecurity concern for 2018: Data Loss, Data Theft, and Ransomware. Sadly, we are overlooking the bigger problems!
Missed the Target by a Mile
I think we are scrutinizing at the small and known threats, when we should… Read More









A Detailed History of Samsung Semiconductor