Together with our R&D partner CEA-Leti, we recently completed an environmental initiative in which we analyzed the environmental impact of Weebit’s Resistive Random-Access Memory (ReRAM / RRAM) technology compared to Magnetoresistive Random Access Memory (MRAM) – another emerging non-volatile memory (NVM) technology.… Read More
Semiconductor Intellectual Property
Model-Based Design Courses for Students
Amid the tumult of SoC design advances and accompanying verification and implementation demands, it can be easy to forget that all this activity is preceded by architecture design. At the architecture stage the usual SoC verification infrastructure is far too cumbersome for quick turnaround modeling. Such platforms also tend… Read More
Counter-Measures for Voltage Side-Channel Attacks
Nearly every week I read in the popular press another story of a major company being hacked: Twitter, Slack, LastPass, GitHub, Uber, Medibank, Microsoft, American Airlines. What is less reported, yet still important are hardware-oriented hacking attempts at the board-level to target a specific chip, using voltage Side-Channel… Read More
Taming Physical Closure Below 16nm
Atiq Raza, well known in the semiconductor industry, has observed that “there will be no simple chips below 16nm”. By which he meant that only complex and therefore high value SoCs justify the costs of deep submicron design. Getting to closure on PPA goals is getting harder for such designs, especially now at 7nm and 5nm. Place and… Read More
Podcast EP141: The Role of Synopsys High-Speed SerDes for Future Ethernet Applications
Dan is joined by Priyank Shukla, Staff Product Manager for the Synopsys High Speed SerDes IP portfolio. He has broad experience in analog, mixed-signal design with strong focus on high performance compute, mobile and automotive SoCs and he has a US patent on low power RTC design.
Dan explores the use of high-speed SerDes with Priyank.… Read More
All-In-One Edge Surveillance Gains Traction
Like it or not, the surveillance market is growing, at a CAGR approaching 10%. Big brother concerns sometimes cloud the picture but overlook the much larger practical yet less hype-worthy applications for surveillance. Home and industrial security, enhanced traffic flow management, monitoring for fire and other fast-growing… Read More
CEO Interview: Stephen Fairbanks of Certus Semiconductor
Trained as a semiconductor Analog and RF Circuit Designer, Stephen Fairbanks has been designing and developing process-specific I/O and ESD libraries for 24 years. His foundational training began while attending Brigham Young University designing highspeed 32 GSPS data acquisition systems and RF interfaces for a time-of-flight… Read More
Alphawave IP is now Alphawave Semi for a very good reason!
The semiconductor ecosystem has been full of interesting twists of late and Alphawave has been a company to watch since the very beginning. Alphawave came out of stealth mode in early 2019 as the world’s first IP company focused on multi-standard connectivity (SerDes) IP solutions. The importance of SerDes had been understated… Read More
Arteris IP Acquires Semifore!
The semiconductor ecosystem consolidation continues with an interesting acquisition of an EDA company by an IP company. Having worked with both Arteris and Semifore over the past few years I can tell you by personal experience that this is one of those 1+1=3 types of acquisitions, absolutely.
How to Efficiently and Effectively Secure SoC Interfaces for Data Protection
Before the advent of the digitized society and computer chips, things that needed protection were mostly hard assets such as jewelry, coins, real estate, etc. Administering security was simple and depended on strong guards who provided security through physical means. Then came the safety box services offered by financial … Read More


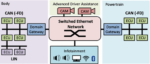
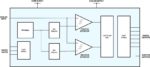




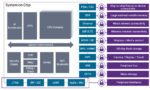
An AI-Native Architecture That Eliminates GPU Inefficiencies