 As the internet of things (IoT) continues its climb to a trillion devices, there has been many articles and books written on the need for securing those devices. With all the IoT gear that I seem to be picking up as Christmas presents, I feel like I’m doing my part to help the market get there, but I have to say, I sure hope the SoC designers that created those devices have been reading and listening to the need for IoT security.
As the internet of things (IoT) continues its climb to a trillion devices, there has been many articles and books written on the need for securing those devices. With all the IoT gear that I seem to be picking up as Christmas presents, I feel like I’m doing my part to help the market get there, but I have to say, I sure hope the SoC designers that created those devices have been reading and listening to the need for IoT security.
And, it does indeed seem that more companies are paying attention to the need for integrated security in their IoT devices. It all starts with something called Root-of-Trust (RoT) and now one of the bigger IP players in the industry, Synopsys, has written a white paper on RoT and is backing it up by introducing a new DesignWare module targeted at providing IoT security IP for SoC devices. The new module is called ‘tRoot H5 Hardware Secure Module’. More on that is a second, but first let’s do a quick review of what we mean by RoT.
As a quick reminder of why we need to secure our IoT devices, one only need remember back to late 2016 when researchers were able to demonstrate how hackers could possibly put people into harm’s way by remotely accessing a Tesla Model S car’s control system. The researchers were able to access and control the engine, braking system, sunroof, door locks, trunk, side-view mirrors and more. They did this by hacking into the car’s infotainment and WiFi connections which then got them access to the car’s controller area network (CAN) bus. The good news is that these were benevolent researchers who then worked with Tesla to close the security holes. But what if it had been someone more nefarious? Enough said.
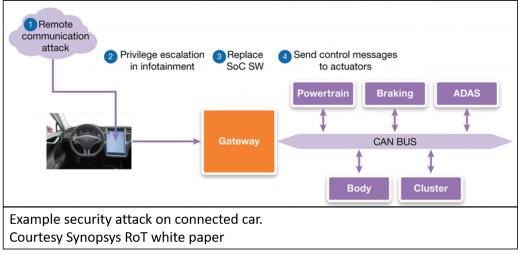
One way to combat this type of hacking is to use what is known as a hardware Root-of-Trust (RoT). RoT is a set of functions that is explicitly trusted by the SoC’s operating system. These functions are used to ensure secure communications between an IoT device and the outside world using encryption and secure keyed handshaking. Additionally, RoT functions can also monitor the SoC’s memory, registers, and internal bus structures to ensure that data that does make it into the device has not been tampered with.
RoT functions can be implemented in software but most SoC designers are now turning to dedicated hardware accelerators to implement their RoT. Hardware cryptographic accelerators run very fast while taking the load off the SoC’s CPU(s), thus saving power and conserving device runtime memory. Additionally, security hardware can also be linked into the rest of the SoC architecture to monitor the SoC as it is running.
Per a recently released Synopsys white paper, RoT functions are typically made up of multiple hardware units. One function would be to ensure that a SoC’s boot up sequence is secure, usually by using a dedicated ROM that can only be accessed by the RoT module. Another unit takes care of True Random Number Generation (TRNG). TRNG ensure that ephemeral data used for secure connections is not easily predictable. The more random the better. Yet another unit may be a secure real-time clock (RTC) that is used to manage time-based security policies.
The important part about RoT is that it must offer strong protection for all operational phases of the SoC, such as power off, power up, run time operations and communications with external entities. Secure monitoring during power up is a must but as mentioned, many teams are now looking to integrate security into all phases of the SoC including runtime operation. Some applications require proper authentication of certificates during runtime. That means that hardware RoT modules are needed to handle common cryptographic functions such as generation of RSA signatures and ECDSA.
Key management is done inside the hardware Root of Trust module. Only indirect access to these keys is allowed and managed by the RoT application layer. Assuming the privilege levels are correct, any importing of keys must be authenticated, and any exporting of keys must be wrapped to ensure continued protection of the secret material. An example of common key management applications would be a hardware secure module (HSM) using a public key cryptography standard (PKCS)#11 interface application to manage the policies, permissions, and handling of keys.
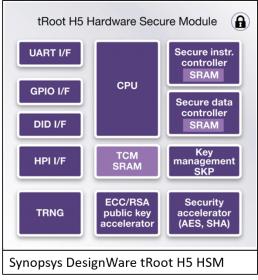 So, what is Synopsys doing in this space? They recently released a DesignWare Module called tRoot H5 Hardware Secure Module. The module is a RoT HSM that enables connected devices to securely and uniquely identify and authenticate themselves to create secure channels for remote device management. The tRoot module is designed to protect devices when they are powered down, at boot time and at runtime. The DesignWare HSM handles secure communications management with other devices and has logic blocks for a Secure Instruction Controller and a Secure Data Controller. These latter two blocks can be used to build further security into the rest of the SoC.
So, what is Synopsys doing in this space? They recently released a DesignWare Module called tRoot H5 Hardware Secure Module. The module is a RoT HSM that enables connected devices to securely and uniquely identify and authenticate themselves to create secure channels for remote device management. The tRoot module is designed to protect devices when they are powered down, at boot time and at runtime. The DesignWare HSM handles secure communications management with other devices and has logic blocks for a Secure Instruction Controller and a Secure Data Controller. These latter two blocks can be used to build further security into the rest of the SoC.
A block diagram for the tRoot HSM module is shown. Being DesignWare, the module can be synthesized and mapped to any standard process technology used for IoT SoCs. The module is highly scalable and flexible as it uses software running on the HSM CPU to define the security features that are to be supported by the SoC. The tRoot module also offers Key Management which uses the PKCS#11 interface to help manage both static and ephemeral keys and can also be used to manage secure in-field firmware updates for the IoT device.
To summarize, making IoT devices secure all starts with a hardware Root-of-Trust. More companies are addressing this space with dedicated RoT IP and Synopsys is now in the mix with their new DesignWare tRoot H5 HSM with Root-of-Trust.
You can learn more about Synopsys offerings in this space by visiting their DesignWare Security IP web page, viewing their webinars and downloading their “Understanding Root-of-Trust” white paper.
See Also:
Understanding Hardware Root of Trust
DesignWare Security IP web page
Webinar: Building Security into Your SoC with Hardware Secure Modules






Comments
There are no comments yet.
You must register or log in to view/post comments.