In the 1990’s, designing for performance was the main challenge and the marketing message for Intel processors was limited to the core frequency. Then designers had to optimize power consumption to target mobile phones/smartphone and build power efficient SoC, low power but high performance devices. Now in 2015 the semi industry realizes that security is becoming a very strong requirement almost mandatory to support emerging systems expected to equip every house, car, factory or body. If you think that security is optional, just remember that tomorrow’ electronic systems will have to be built to support a changing world, just take Paris attacks as an example of today’ reality …
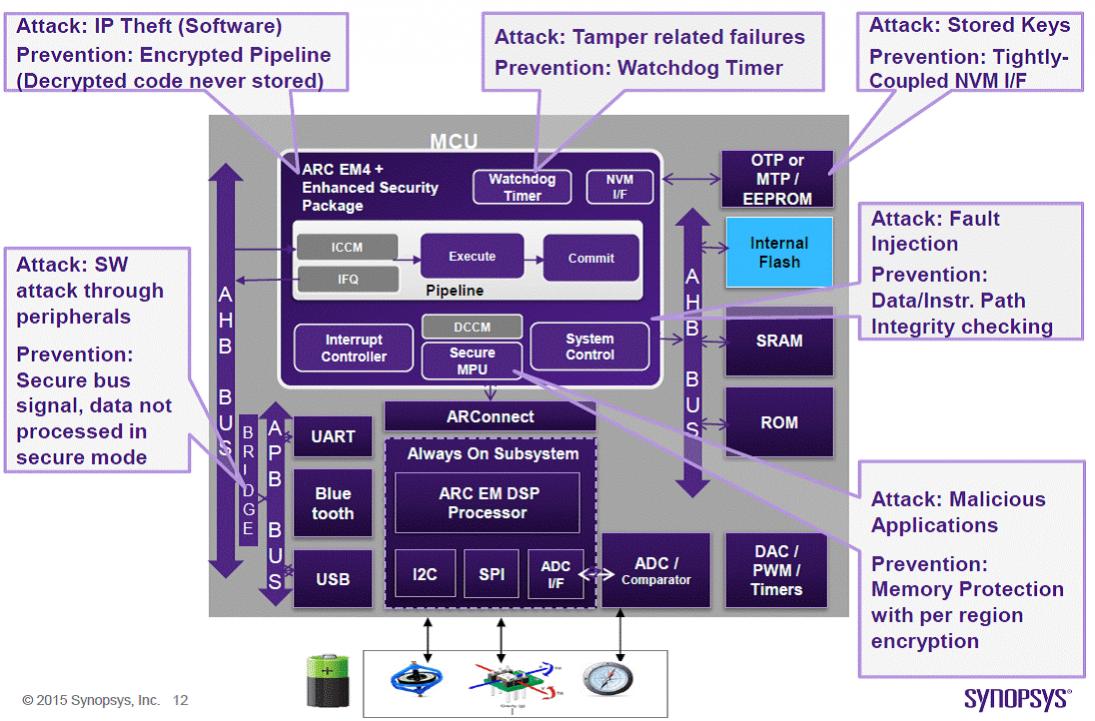
The above graphic, picturing a typical IoT Edge Device controller part, is showing attacks coming from different forefronts: software IP thefts, Tamper related failures, stored keys theft, Fault injection, Malicious applications, attacks from peripherals…
Sourcing an IP like the ARC-EM processor core from Synopsys will offer a strong advantage, as the IP vendor also provides a complete security package, ARC-EM Enhanced Security Package. This new ARC EM option enables designers to create an isolated, secure environment that protects their systems and software from attacks and to implement the various pieces and IP in a consistent environment.
At high level, the designer can select security processors and modules, cryptographic cores like symmetric/hash cryptographic engines, platform security (to build secure boot and cryptography middleware) and content protection supporting HDCP2.2 and DTCP IP for DRM schemes.
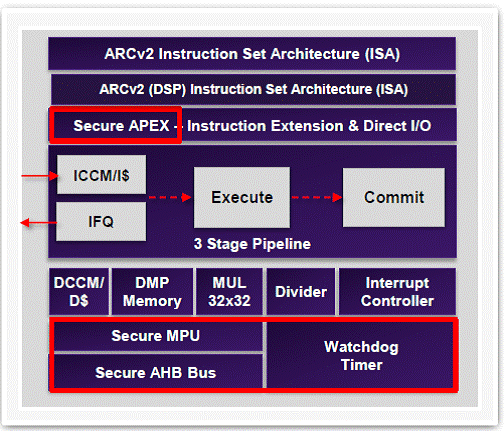
At first, we notice that ARC-EM Enhanced Security Package is merged with the selected ARC-EM processor implemented to support the functional application, eliminating dedicated security processor. This single processor architecture, available for ARC EM4 and EM5-D, reduces area and power consumption as there is no more need for additional security processor.
The designer can define a secure, isolated area of the processor to guarantee code and data protection for confidentiality and integrity (the secure APEX red box in the block diagram), enabling a Trusted Execution Environment. Moreover, in-line instruction and data encryption, address scrambling and data integrity checks provide protection from system attacks and IP theft.
The memory is protected by using secure MPU (see the bottom left red box) based on privilege levels supporting multiple privilege levels. Accesses to secure peripherals and system resources are restricted by using secure APEX or system bus signaling (secure AHB Bus red box). In secure mode, the Trusted Execution Environment can’t be accessed from the peripherals.
ARC EM CPU pipeline has been designed to be tamper resistant as there is no store in the 3-stages pipeline. The CPU can detect tampering and software attacks, thanks to integrated watchdog timer detecting system failures and enable counter measures.
In fact, ARC-EM Enhanced Security Package interleaves protected processor pipeline registers and in-line instruction and data encryption ensure decrypted instructions are never stored or accessible, protecting algorithms from reverse engineering without impact to the timing of instructions. Sourcing both the processor IP and the security package to the same provider is the key for maximum protection allowing optimized implementation, reducing area and power consumption.
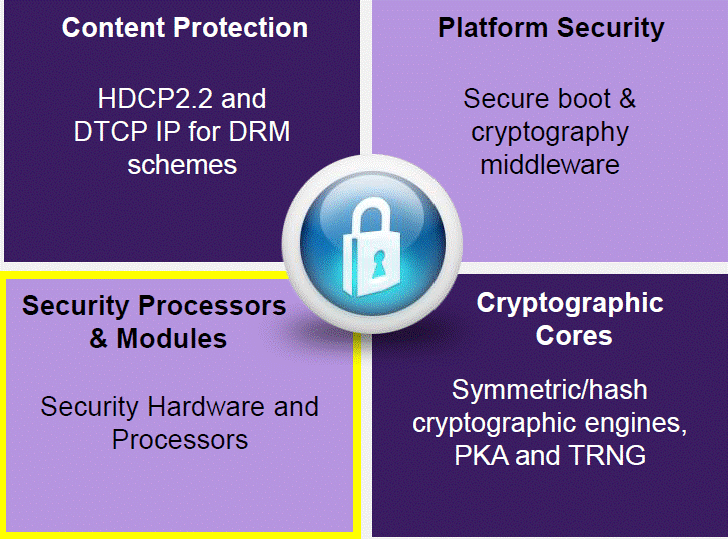
The Enhanced Security Package with SecureShield is a part of Synopsys’ comprehensive portfolio of security IP solutions, which also includes the CryptoPack option for ARC EM processors as well as the DesignWare Security IP solutions, which comprise a range of cryptography cores and software, protocol accelerators, root of trust, platform security and content protection IP. On top of the above described security hardware features, Synopsys provides content protection, platform security and cryptographic cores. The designer will benefit from common crypto algorithms such as AES, 3DES, ECC, SHA-256 or RSA.
The ARC EM Family is supported by a robust ecosystem of software and hardware development tools, including the ARC EM Starter Kit for early software development, MetaWare Development Toolkit that generates highly efficient code ideal for deeply embedded applications, ARC simulators including nSIM and xCAM, and the ARChitect core configuration tool.
Synopsys’ embARC Open Software Platform gives all ARC EM software developers online access to a comprehensive suite of free and open-source software that eases the development of code for IoT and other embedded applications.
Such an integrated solution where security is implemented within the CPU architecture by the IP core provider allows building a secured system more coherent than when the designer has to insert security into an existing architecture or more power efficient than with a dual CPU solution, when adding a dedicated security processor. The combination of security features and energy savings is especially important for IoT and mobile applications, including wearable and smart home devices.
From Eric Esteve from IPNEST
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.