I wrote a while back about some of the more exotic architectures for machine learning (ML), especially for neural net (NN) training in the data center but also in some edge applications. In less hairy applications, we’re used to seeing CPU-based NNs at the low end, GPUs most commonly (and most widely known) in data centers as the workhorse… Read More
Author: Bernard Murphy
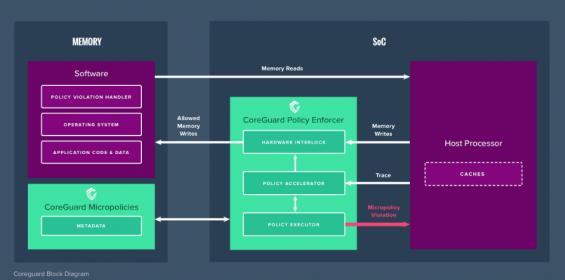
Dover Microsystems Spins New Approach to Security
One of the companies I met at ARM TechCon was Dover Microsystems who offer a product in embedded security. You might ask why we need yet another security solution. Surely we’re overloaded with security options from ARM and many others in the forms of TEEs, secure boots, secure enclaves and so on? Why do we need more? Because defending… Read More
NXP Strengthens Security, Broadens ML Application at the Edge
Security and machine learning (ML) are among the hottest areas in tech, especially for the IoT. The need for higher security is, or should be, blindingly obvious at this point. We struggle to fend off daily attacks even in our mainstream compute and networking environment. How defenseless will we be when we have billions of devices… Read More
Webinar: NVIDIA Talks High Quality Metrics in Power Integrity Signoff
There’s a familiar saying that you can’t improve what you can’t measure. Taking that one step further, the more improvement you want, the more accurately you have to measure. This become pretty important when you’re building huge designs in advanced technologies. Margins are a lot tighter all round and use-cases are massively… Read More
Emulation from In Circuit to In Virtual
At a superficial level, emulation in the hardware design world is just a way to run a simulation faster. The design to be tested runs on the emulator, connected to whatever test mechanisms you desire, and the whole setup can run many orders of magnitude faster than it could if the design was running inside a software simulator. And … Read More
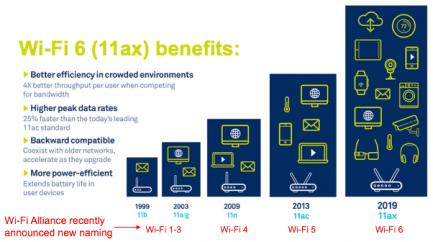
Wi-Fi Standards Simplified
In the world of communications, the industry fairly quickly got a handle on a naming convention for cellular technology generations that us non-communication geeks could understand – 2G, 3G, 4G and now 5G, (though some of us could never quite understand the difference between 4G and LTE, at least as those terms are widely and no … Read More
The Cloud-Edge Debate Replays Inside the Car
I think we’re all familiar with the cloud/edge debate on where intelligence should sit. In the beginning the edge devices were going to be dumb nodes with just enough smarts to ship all their data to the cloud where the real magic would happen – recognizing objects, trends, need for repair, etc. Then we realized that wasn’t the best… Read More
ARM Turns up the Heat in Infrastructure
I don’t know if it was just me but I left TechCon 2017 feeling, well, uninspired. Not that they didn’t put on a good show with lots of announcements, but it felt workman-like. From anyone else it would have been a great show, but this is TechCon. I expect to leave with my mind blown in some manner and it wasn’t. I wondered if the SoftBank … Read More
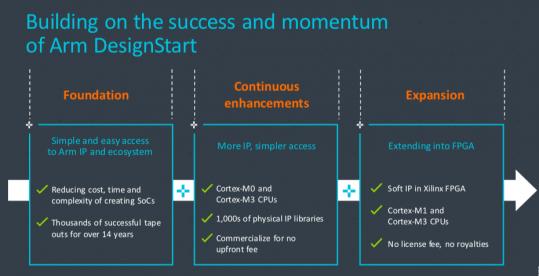
One Less Reason to Delay that Venture
Many of us dream about the wonderful widget we could build that would revolutionize our homes, parking, health, gaming, factories or whatever domain gets our creative juices surging, but how many of us take it the next step? Even when you’re ready to live on your savings, prototypes can be expensive and royalties add to the pain. … Read More
Accellera Tackles IP Security
I recently learned that Accellera has formed an IP security working group. My first reaction was “Great, we really need that!”. My second reaction was “But I have so many questions.” Security in the systems world is still very much a topic in its infancy. I don’t mean to imply that there isn’t good work being done in both software and… Read More
















Advancing Automotive Memory: Development of an 8nm 128Mb Embedded STT-MRAM with Sub-ppm Reliability