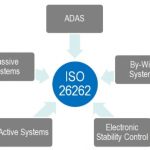
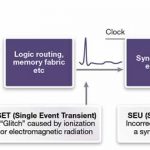
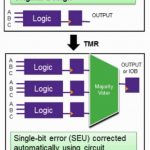
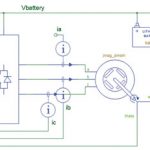
I’ve been an Electrical Engineer and a car driver since 1978, so I’ve always been attracted to how the automotive industry designs cars to be safer for me and everyone else around the globe. According to statistics compiled by the CDCI learned that some 33,700 Americans died by motor vehicle crashes in 2014, which is… Read More
Tag: safety critical
TMR approaches should vary by FPGA type
We’ve introduced the concepts behind triple modular redundancy (TMR) before, using built-in capability in Synopsys Synplify Premier to synthesize TMR circuitry into FPGAs automatically. A recent white paper authored by Angela Sutton revisits the subject… Read More
Speaking about the Internet of Trust on April 21
Five minutes to ruin a reputation built over 20 years, as Warren Buffett put it, holds true in personal relationships. On the Internet of Things, reputations can disappear in five seconds. How do we move from merely intelligent Things to a level where devices have to be Trusted?… Read More
FPGA tools for more predictive needs in critical
“Find bugs earlier.” Every software developer has heard that mantra. In many ways, SoC and FPGA design has become very similar to software development – but in a few crucial ways, it is very different. Those differences raise a new question we should be asking about uncovering defects: earlier than when?… Read More
Chips on the road to deep learning
CES has been morphing into an automotive show for several years now. Chipmakers were pitching control solutions, infotainment solutions, then connectivity solutions. Phone makers pitched device integration. Automotive electronics suppliers pitched MEMS sensors and cameras. Now, with a lot of pieces in place, the story … Read More
3 flavors of TMR for FPGA protection
Back in the microprocessor stone age, government procurement agencies fell in love with the idea of radiation hardened parts that might survive catastrophic events. In those days, before rad-hard versions of PowerPC and SPARC arrived, there were few choices for processors in defense and space programs.
One of the first rad-hard… Read More
To err is runtime; to manage, NoC
Software abstraction is a huge benefit of a network-on-chip (NoC), but with flexibility comes the potential for runtime errors. Improper addresses and illegal commands can generate unexpected behavior. Timeouts can occur on congested paths. Security violations can arise from oblivious or malicious access attempts.
Runtime… Read More
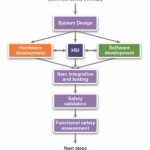
Automotive MCU code fault-busting with vHIL
With electronic and software content in vehicles skyrocketing, and the expectations for flawless operation getting larger, the need for system-level verification continues to grow. Last month, we looked at a Synopsys methodology for virtual hardware in the loop, or vHIL… Read More
Simulating to a fault in automotive and more
We’re putting the finishing touches on Chapter 9 of our upcoming book on ARM processors in mobile, this chapter looking at the evolution of Qualcomm. One of the things that made Qualcomm go was their innovative use of digital simulation. First, simulation proved out the Viterbi decoder (which Viterbi wasn’t convinced had a lot … Read More
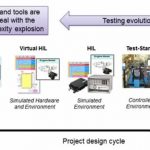
Virtual HIL and the 100M LOC car
Aerospace and defense applications have traditionally leveraged hardware-in-the-loop (HIL) testing to overcome several issues. A big one is how expensive the physical system is. Even breaking down the system into subsystems for test can still be too expensive when fielding more than a couple test stations. Modeling elements… Read More