You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
The latest reliability report from Consumer Reports which dumped on domestics and rained glory upon Asian imports highlighted a conundrum facing car makers. The more effort car makers put into innovation, the greater the risk of consumer confusion, system failure and lousy reliability scores.
The picture is even worse if one… Read More
ARM TechCon is one of the most influential conferences in the semiconductor ecosystem without a doubt. This year ARM TechCon has moved from the Santa Clara Convention Center to the much larger convention center in San Jose. Last year the conference seemed to be busting at the seams so this move makes complete sense. A little less … Read More
It has taken the U.S. 16 years to enact Data Breach laws in each state. California led the way, with the first, in 2002 to protect its citizens. Last in line was Alabama, which just signed their law in March 2018. There is no overarching consistent data breach law at the federal level. It is all handled independently by each state. This… Read More
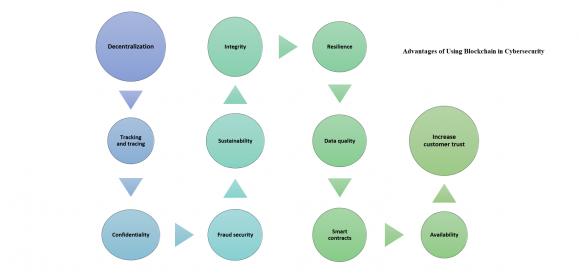
In the first part we covered AI as the first line of defense for cybersecurity, the goal was to keep the cyber-criminals at bay, but in case they managed to get-in and infiltrate the network we need to initiate the second line of defense; #Blockchain. With the fact that cybercrime and cyber security attacks hardly seem to be out of the… Read More
The year 2017 wasn’t a great year for cyber-security; we saw a large number of high-profile cyber attacks; including Uber, Deloitte, Equifax and the now infamous WannaCry ransomware attack, and 2018 started with a bang too with the hackingof Winter Olympics. The frightening truth about increasingly cyber-attacks is … Read More
A recent survey by Varonis of 500 security professionals from the U.S., UK, and France highlights the top three cybersecurity concern for 2018: Data Loss, Data Theft, and Ransomware. Sadly, we are overlooking the bigger problems!
Missed the Target by a Mile
I think we are scrutinizing at the small and known threats, when we should… Read More
One of the biggest misconceptions is thinking cybersecurity is only about technology. When in fact, people and their behaviors, play a prominent role in almost every aspect of protecting digital assets. Without proper consideration for the human element, security strategies are destined to fail miserably.
In this Week’s Video… Read More
Now that the dust has settled with the Softbank acquisition I must say that Arm is truly a different company. There are now a lot of new faces from outside the semiconductor industry, which is a good thing, and a lot less stress from Wall Street which is an even better thing. Simon can now wear whatever he wants without the worry of lowering… Read More
#IoT devices are supposed to function properly in the field for many years without human intervention. Given that we know in advance that each #IoT node is going to be hacked in the future, it is essential that some trusted code be isolated from that hack to restore the #IoT application code to a known good state.… Read More
Boeing will begin testing pilotless jetliners in 2018. Yes, the future of air travel may include planes without pilots. Just computers and calculations to get passengers safely to their destinations. Advances in Artificial Intelligence (AI) is opening up possibilities to make flying safer, more consistent, easier to manage,… Read More