 Asymmetric attacks, like those in cybersecurity, benefit the aggressor by maintaining the ‘combat initiative’. That is, they determine who is targeted, how, when, and where attacks occur. Defenders are largely relegated to preparing and responding to the attacker’s tempo and actions. This is a huge advantage.
Asymmetric attacks, like those in cybersecurity, benefit the aggressor by maintaining the ‘combat initiative’. That is, they determine who is targeted, how, when, and where attacks occur. Defenders are largely relegated to preparing and responding to the attacker’s tempo and actions. This is a huge advantage.
Awakening Business
The business world is beginning to understand some of the inherent aspects they face. Warren Buffett, the Oracle of Omaha and CEO of Berkshire Hathaway, has stated cyber attacks are the “number one problem with mankind” and explained how attackers are always ahead of defenders and that will continue to be the case.
Not all is lost of course, but we must be cognizant of the attacker’s strengths in order to form a winning defensive strategy. Cybersecurity is not just patching or an exercise in engineering, rather it is a much larger campaign that involves highly motivated, skilled, and resourced adversaries on a battlefield that includes both technology and human behaviors. If you only see cybersecurity as a block-and-tackle function, you have already lost.
Finding Rocks
Some believe it is imperative to spend inordinate amounts of time and resources attempting to find every possible weakness, so the vulnerabilities can be closed. This is a near impossible task that nobody has ever achieved. It is a sinkhole of resources that can consume everything put forward.
The truth about vulnerability scanning strategies it that most are never exploited. Therefore, only a subset actually pose a material threat. Prioritization is key because it is a waste to commit security resources to threats that will never manifest. Just because something is possible, does not mean it will occur.
Consequently, I think the act of trying to find ALL vulnerabilities is a failing strategy, as it will consume far too many resources and still likely result in a compromise. As Fredrick the Great said, “In trying to defend everything he defended nothing”.
But that has not stopped the industry from travelling down this path. For many, it has become a rut of singular focus. The lure is that it seems like familiar territory, similar in nature to other information technology problems, and something which can be explained and partially measured. However, it is a mirage. Appearing just out of reach, it is easy to believe it is attainable. But no matter how far you walk, you never get there. Closing all vulnerabilities to be secure is a mentally satisfying theory, but in practice it is not practical. The emergence of vulnerabilities is tied to complexity and innovation. As long as technology continues to rapidly innovate and become more complex, vulnerabilities will never cease and therefore the process of closing them is never finished. In the end, organizations risk participating in a war of attrition where defenders are consuming vastly more resources than the opposition in a endless cycle of vulnerability discovery.
I would postulate you don’t need to address all vulnerabilities equally. I am not advocating abandoning the search for weaknesses, as there is great value in the exercise, but there should be allowances, prioritization, and permissible tradeoffs! In fact, it must be one part of a greater effort for organizations to manage the cyber risks of their digital ecosystems. It should never be the sole focus of a security group.
Other plans can counter such threats, especially if you are creative and have certain insights…. If you know your enemy, it can suffice to know how they will maneuver. Consider this, a chess player does not need to know all the possible future combinations. Rather, they lay traps, see the board from their opponent’s perspective, and move with insights to how their opponent will likely act. You beat the player, not the chessboard pieces.
The best way to gain an advantage over cyber attackers is to establish a professional, efficient, and comprehensive security capability that will last and adapt to evolving risks. Defenders must minimize the strengths of their opponents while maximizing their own advantages. Strategic planning is as crucial as operational excellence.
5 Recommendations to Build Better Security:
1. Establish clear security goals, measures & metrics, and success criteria. Thinking you will stop every attack is unrealistic. Determine the optimal balance between residual risk, security costs, and productivity/usability of systems
2. Start with a strategic security capability that encompasses a Prediction(of threats, targets, & methods), Prevention (of attacks), Detection (of exploitations), and Response (to rapidly address impacts) in an overlapping and continuous improvement cycle. This reinforces better security over time and positions resources to align with the most important areas as defined by the security goals. Over time each area will improve to support each other and collaboratively contribute to a better overall sustainable risk management posture.
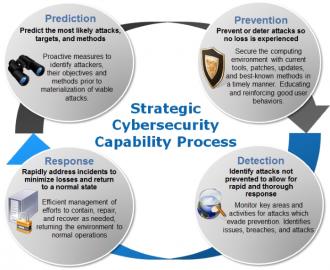
3. Understand your enemy. Threat agents have motivations, objectives, and methods they tend to follow, like water seeking the path of least resistance. The more you align your defenses to these, the more scalable and effective you become. Don’t waste precious resources on areas that don’t affect the likelihood, impact, or threats.
4. Incorporate both technical and behavioral controls. Do not overlook the human element of both the attackers and targets. Social engineering, as an example, is a powerful means to compromise systems, services, and environments, even ones that possess very strong technical defenses.
5. Maintain a vulnerability scanning capability (technical and behavioral) but prioritize the effort to identify and remediate those which pose the greatest risk. That includes most likely avenues to be exploited and ones which can cause unacceptable impacts. Knowing that most vulnerabilities will never be leveraged, this is an opportunity to effectively use resources and reallocate to other efforts where it makes more sense
The Long Game
As organizations approach cybersecurity challenges, they should consider a more balanced, prioritized, and proactive approach to managing cyber risks. They will get farther, faster, with less resources and more focus. This is not a sprint. As long as technology continues to innovate and be implemented, risks will continue evolve.
In the end, strategic warfare outpaces battlefield tactics.
Interested in more? Follow me on your favorite social sites for insights and what is going on in cybersecurity: LinkedIn, Twitter (@Matt_Rosenquist), Information Security Strategy blog, and Steemit
Share this post via:





Moore’s Law Wiki