 Let’s just take it as a given that securing IP design data is critical. It’s rather like saying that it’s a good idea to have security in the Tower of London to stop the crown jewels being stolen. IP blocks are the crown jewels of an SoC company.
Let’s just take it as a given that securing IP design data is critical. It’s rather like saying that it’s a good idea to have security in the Tower of London to stop the crown jewels being stolen. IP blocks are the crown jewels of an SoC company.
Data now must be secured within the collaborative teams that share that data across international boundaries. Adding to the challenge is the fact that most of the current generation of security tools are perimeter-based solutions, focused on preventing outsiders from gaining access to internal company networks, file systems and databases containing sensitive, proprietary data. However, defending organizations from unwitting employee security breaches, compromised accounts, and insider attacks is becoming a growing concern.
Solving the complete IP security problem calls for technologies that protect source data from internal security weaknesses and provide early-warning alerts for risky and anomalous internal behavior. However, security solutions must also take into account the multi-site collaborative nature of today’s design teams.
To successfully protect IP design data from within, companies must look to technologies that support the concepts of both IP/file-level security and data-centric threat detection. This requires two foundational elements:
Firstly, IP-Level and file-level security through an IP management platform such as Methodics ProjectIC that provides IP-level permission assignments and tracking of design data according to IP parent/child relationships, IP branches, levels of hierarchy, and the tracking of who is using which data, where in the design, and in which geographic locations. Once the appropriate permissions are set, the IP management platform will pass this information to the underlying data management system such as Perforce Helix, which then assures the data is secured at repository, branch, directory and even the at an individual file level.
Second, big-data-centric threat detection such as provided by Perforce Helix Threat Detection that offers behavioral analytics and identification of threats and risky behavior performed on Helix SCM repositories.
ProjectIC already has a lot of security features at the project level, smoothly merged into the hierarchy and geographical multi-site aspects of most companies. ProjectIC also works with the underlying design data management tool, such as Helix, to ensure file-level security (so that IP level security cannot be bypassed by simply identifying and copying the underlying files).
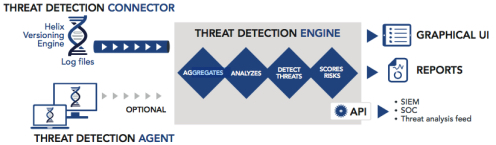
The second critical element in a robust IP security solution is the ability to detect anomalous behavior and threats. This is where Perforce Helix Threat Detection comes in, offering a new approach to threat detection. Helix applies advanced big data behavioral analytics to user activity to detect potential attack events, alert security teams, and quickly generate actionable reports that detail anomalous, high-risk behavior.
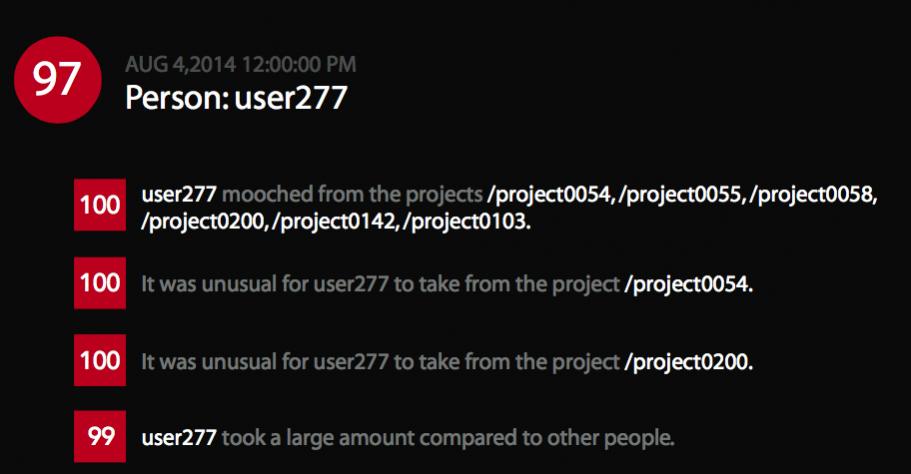
User activity log files are ingested by the Helix Threat Detection Engine that correlates and analyzes: login and logout, project and file access (folder, file, path, etc), amount of data moved or synchronized (get, commit, sync, etc), timestamp and user data. It applies analysis models (e.g., activity, statistical and clustering mathematics) to log data. Once a threat is identified, a non-intrusive threat detection agent (endpoint sensor) can also be deployed to a laptop or desktop to capture all activity on the endpoint: file copies, cut and pastes, screen captures, printing, obfuscations and exfiltration.
The type of threats that this identifies include:
- Compromised, careless, and departing employees who download large amounts of data from sensitive projects
- Insiders who slowly take small amounts of data over a long period of time
- Machines compromised by stealth malware that are siphoning data
- Outside or Advanced Persistent cyber attacks
This approach gives companies a double-walled approach to securing proprietary IP data, at both the IP/file level and also head off potential security breaches of theft, whether the threat is internal or external.
The Methodics white paper Threat Detection: A Proactive Approach to Securing SoC IP Design Data is here.
Share this post via:






Comments
0 Replies to “Threat Detection: How To Keep the Crown Jewels Secure”
You must register or log in to view/post comments.