IPs have an attack surface that indicates how they can be compromised in real world scenarios. Some portions of the attack surfaces are well known, others are discovered during analysis, testing or out in the field. SoCs that use large collections of IPs need a systematic and reliable way to determine the various security vulnerabilities across the hierarchy, even as these vulnerabilities are discovered in heterogeneous environments. Percipient provides a platform for IP analyzers and test teams to convey the security threats detected and for SoC managers to consolidate and measure these threats in a systematic manner, not only for a single SoC, but across all SoC’s in their company.
WEBINAR: Concerned about IP security threats for your SoCs?
What is The IP Security Threat Level In Your SoC?
The average SoC in today’s design environment has more than 100 different IPs. In many cases, the actual count is much higher because IPs are embedded in other IPs due to reuse or flattening of the IP hierarchy. Additionally, these IPs come from many different sources including external vendors, internal – usually far flung – IP teams, and even locally developed content.
As the SoCs are assembled over the course of several months, or even years, these IPs go through various mutations, feature changes, bug fixes, and revisions, all of which have to be incorporated into the chip. In the high pressure, compressed timelines of today’s projects, not every change can be thoroughly verified or exercised. Often seemingly innocuous changes are ignored or left to be “tested later.”
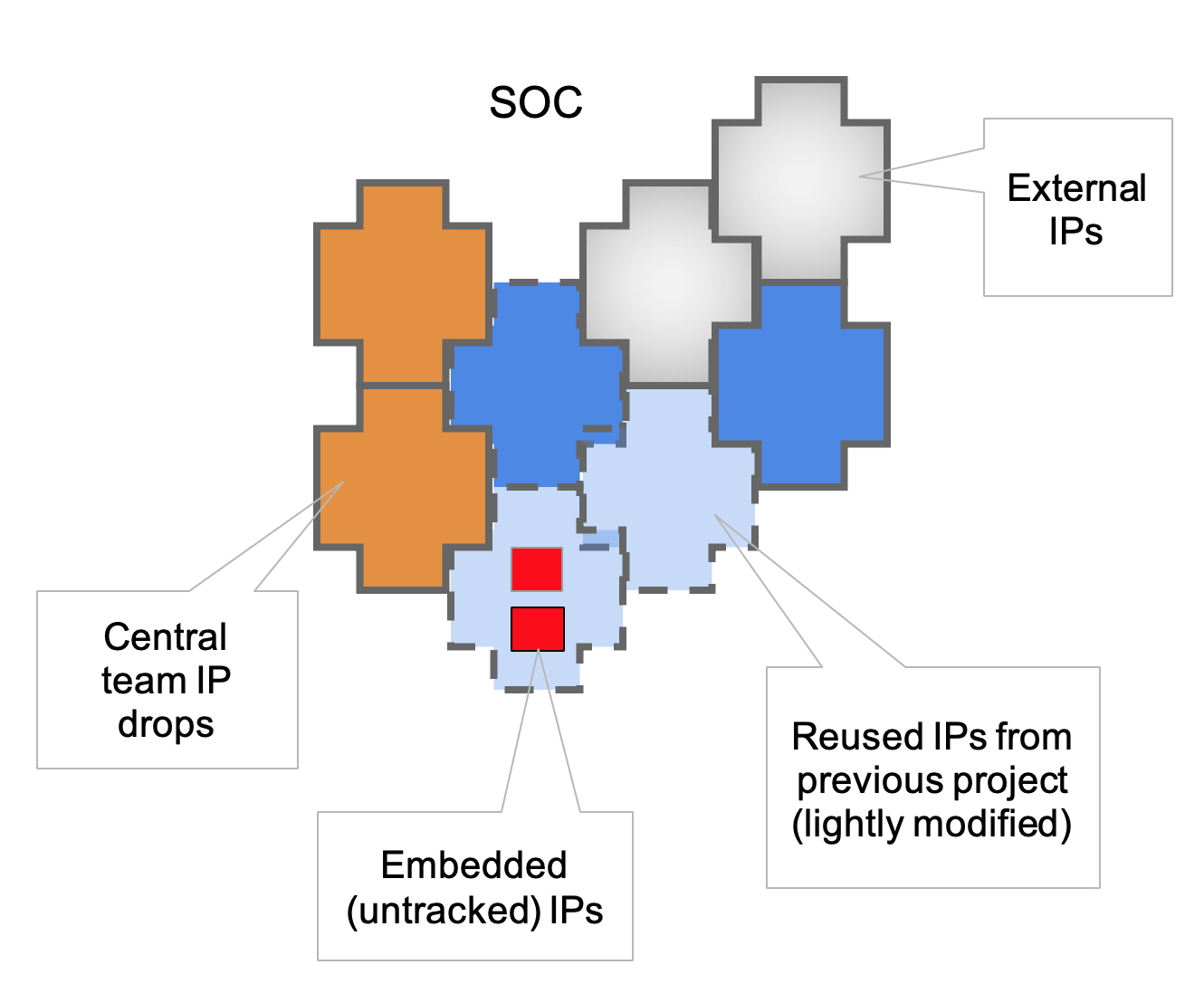
As shown in the figure, the SoC is a patchwork of IPs with various origins, quality levels, and sometimes poorly understood attack surfaces.
This scenario is a security headache for most chip teams, because it leads to four serious problems:
- Inability to pinpoint the exact content of your chip
- Inability to test and guard against all possible scenarios for security attacks on the known content of the chip
- Inability to know if vulnerabilities discovered in contexts outside of the immediate verification impact the SoC or not
- Inability to determine if vulnerabilities discovered in context of one SoC impact other SoCs being developed, or even worse, other SoCs that have been released
This ‘needle-in-a-haystack’ problem keeps getting worse as the cost and the consequences of security breaches become magnified. If your product plays a critical role in self driving cars, remote surgical procedures, high performance AI hardware and a host of other mission critical systems, both the chances of attacks and their impact can be severe.
IPLM To The Rescue
An IPLM system such as Percipient from Methodics is the definitive, single source of truth for all of the IP content in every chip in the enterprise. Percipient is a traceable platform that allows all design information to be connected throughout an enterprise. Using Percipient allows a chip lead to determine exactly which version of which IP was used in the design. It also provides a channel of information through integrations to bug tracking systems like Jira where a vulnerability found in one context – say a lab test or out in the field – can be annotated on the exact versions of impacted IPs.
Each team can now transparently see the exact security impact of using all of these specific IPs in their design as the threats are uncovered and take the right steps to ensure that these are addressed.
These security vulnerabilities, found in the various contexts of the IPs that constitute the system, can also be rolled up at the SoC level into a well understood ‘threat level’ for the SoC that changes dynamically as new threats are detected and existing threats are addressed. SoC owners can also preview how this threat level will be impacted when they incorporate newer versions IPs into their SoC.
About Methodics
Methodics solutions enable high-performance hierarchical analog/mixed signal, digital, software, embedded software, and SOC design collaboration across multi-site and multi-geographic design teams, assuring full traceability of the use and reuse of important design assets for Functional Safety compliance with such standards as ISO26262 and DO-254. With Methodics, traceability is built into the design process – it’s not added on as an after thought.
Advanced IP distribution, cataloging, and workspace management ensure that no matter where designers are located they have full visibility into the IP available to them and can easily access the corresponding data.
And integration of IP Lifecycle Management with industry-standard data management solutions, such as Perforce, Subversion, Git and others makes designs more efficient and predictable, and with higher quality. This approach ensures data is safe, always available, and that the tools can take advantage of the latest advancements from the software configuration management community.
Our highly scalable and industry proven solutions are ideal for large multinational, multisite SoC design teams as well as for small, specialized design teams. www.methodics.com
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.