The intricacies of analog IP circuit design have always required special consideration during physical layout. The need for optimum device and/or cell matching on critical circuit topologies necessitates unique layout styles. The complex lithographic design rules of current FinFET process nodes impose additional restrictions… Read More
VC Apps Tutorial at DVCon 2016
We might wish that all our design automation needs could be handled by pre-packaged vendor tool features available at the push of a button, but that never was and never will be the case. In the language of crass commercialism, there may be no broad market for those features, even though you consider that analysis absolutely essential.… Read More
Is Smart Bluetooth de facto standard for IoT Wearable, Beacons, Fitness and Health ?
Synopsys launch BTLE PHY IP, qualified by the Bluetooth Special Interest Group (SIG) and meeting compliance with the Bluetooth® Smart v4.2 specification. The company has built a partnership with Mindtree to provide a complete solution, integrating Synopsys’ Bluetooth Smart PHY IP and Mindtree’s production-proven BlueLitE… Read More
Verdi Update and NVIDIA on Verification Compiler
Synopsys hosted a lunch session on Thursday of DVCon. Michael Sanie of Synopsys opened the session, with a look back at the last DVCon where he had talked about Verification Compiler (VC) and extending the platform to Verification Continuum, which adds emulation and FPGA-based prototyping (HAPS – there was a very cool HAPS demo… Read More
Ajoy – History, Perspectives and Crossing the Chasm
EDAC hosted an event at DVCon this week where Jim Hogan interviewed Ajoy Bose (CEO of Atrenta prior to its acquisition by Synopsys). The nominal purpose was to talk about turning a venture into a valuable enterprise. This was covered but, in Jim’s way, it was really a more wide-ranging and personal interview. This is an abstract of… Read More
Synopsys at DVCon 2016
It’s that time of year again – DVCon starts on Monday Feb 29[SUP]th[/SUP] and as always should be a packed event. Synopsys plans a big showing, in the exhibit hall, in a sponsored lunch, at tutorials and in papers. Time to get your conference shoes on and go check them out – I plan to be there all week.
One of the most obvious things you will… Read More
Synopsys’ New Circuit Simulation Environment Improves Productivity — for Free
When technology advances, complexities increase and data size becomes unmanageable. Fresh thinking and a new environment for automation are needed to provide the required increase in productivity. Specifically in case of circuit simulation of advanced-node analog designs, where precision is paramount and a large number… Read More
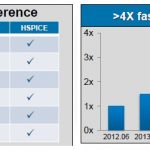
HSPICE – 35 and looking good!
A maturetool. A legacytool. A tool that’s a little long in the tooth. We have all used these terms to refer to an EDA product that has not been able to keep up with technical challenges of model complexity, performance, or new features required by current SoC and system design requirements.… Read More
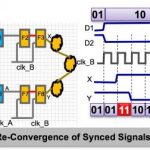
Domain Crossing Verification Needs Continue to Grow
Clock domain crossing (CDC) analysis has been around for many years, initially as special checks in verification or static timing analysis, but it fairly quickly diverged into specialized tools focused just on this problem. CDC checks are important because (a) you can lose data or even lock up at, or downstream of a poorly-handled… Read More
True Random Number Generation
Random numbers are central to modern security systems. The humble password, perhaps the least profound application, is encrypted and verified against using SHA or MD algorithms with a random number salt. You probably remember a college class on how to generate pseudo-random numbers algorithmically, some very sophisticated.… Read More