A recent SemiWiki post covered the topic of protecting high-speed interfaces in data centers using security IP. That post was based on a presentation made by Dana Neustadter at IP-Soc Silicon Valley 2022 conference. Dana’s talk was an overview of various interfaces and Synopsys’ security IP for protecting those interfaces. … Read More
Tag: encryption
I Have Seen the Future – Cornami’s TruStream Computational Fabric Changes Computing
Here is another installment regarding presentations at the Linley Fall Processor Conference. Every now and again, you see a presentation at an event like this that shakes you up. Sometimes in a good way, sometimes not so much. I attended the Cornami presentation on its new TruStream computational fabric and I was definitely shaken… Read More
Having Your Digital Cake and Eating It Too
Anybody who’s ever read the iconic MAD magazine would be familiar with the wordless Spy vs Spy cartoon. First published in January, 1961, it features two agents involved in stereotypical and comical espionage activities. One is dressed in white, and the other in black, but they are otherwise identical. A parody of the political… Read More
Car Vandals Eschew Crowbars
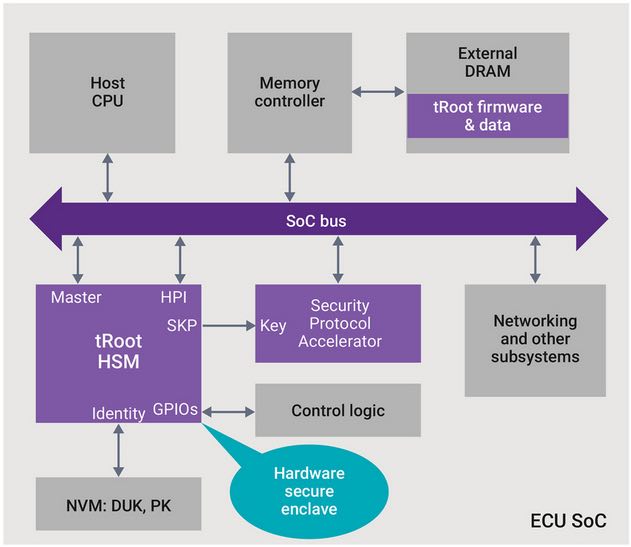
It used to be that automotive theft and crime was perpetrated with a crowbar. Now with increased electronics content, car designer and owners need to worry about electronic threats. Anywhere there is a communication link or a processor, there are potential threats to the security of the car. The range of these threats covers everything… Read More
Security and RISC-V
One of the challenges in the RISC-V bid for world domination may be security. That may seem like a silly statement, given that security weaknesses are invariably a function of implementation and RISC-V doesn’t define implementation, only the instruction-set architecture (ISA). But bear with me. RISC-V success depends heavily… Read More
You Can’t Get There From Here
No doubt many who read this article have heard the expression “You can’t get there from here…” It’s most often attributed to New Englanders – primarily residents of Maine – to describe a route to a destination that is so circuitous and complex that one needn’t bother embarking on the journey.
In the context of the business world, the… Read More
Restoring Digital Trust – Can China Lead the Way?
I read with interest the US Chamber of Commerce’s assessment of the Made in China (MIC) 2025 plan to transform the world’s most populous nation into an Advanced Manufacturing leader. MIC 2025 covers 10 strategic industries that China identifies as critical to economic growth in the 21[SUP]st[/SUP] century, including next-gen… Read More
Timing Channel Attacks are Your Problem Too
You’ve heard about Meltdown and Spectre and you know they’re really bad security bugs (in different ways). If you’ve dug deeper, you know that these problems are related to the speculative execution common in modern processors, and if you dug deeper still you may have learned that underlying both problems are exploits called timing… Read More
Is This the Death Knell for PKI? I think so…
It was 1976 when distinguished scholars Whitfield Diffie and Martin Hellman published the first practical method of establishing a shared secret-key over an authenticated communications channel without using a prior shared secret. The Diffie-Hellman methodology became known as Public Key Infrastructure or PKI.
That was… Read More
Securing embedded SIMs
If you have a phone, you probably know it has a SIM card, for most of us the anchor that ties us into a 2/3-year plan with one network provider, unless you have an unlocked phone. Even then, you have to mess around swapping SIM cards if you travel overseas. Wouldn’t it be nice if the SIM was embedded and could be switched though an app or an… Read More