One-time programmable (OTP) non-volatile memory has been around for a long time. Compared to other non-volatile memory technologies OTP has a smaller footprint and does not require additional manufacturing steps, making it a popular choice to store items such as boot code and encryption keys. While this sounds simple, the growth… Read More
Tag: ecc
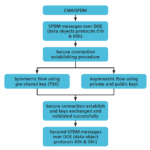
Averting Hacks of PCIe® Transport using CMA/SPDM and Advanced Cryptographic Techniques
In today’s digital landscape, data security has become an indispensable feature for any data transfer protocol, including Peripheral Component Interconnect Express (PCIe). With the rising frequency and sophistication of digital attacks, ensuring data integrity, confidentiality, and authenticity during PCIe transport… Read More
Automotive Designs Have No Room for Error!
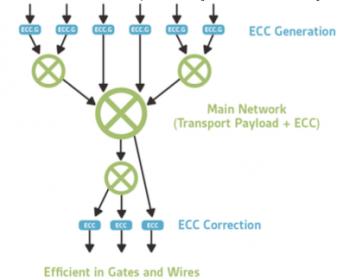
Automotive designs demand a high level of fault tolerance, and one of the methods to achieve this is to use error correcting codes (ECC). This Wikipedia page ECC Memory gives a flavor, though that article concentrates on memory and we are interested in wider applications using a form of forward error correction. This technique … Read More
NIST Standardizes PQShield Algorithms for International Post-Quantum Cryptography
News of cyberattacks is routine these days in spite of the security mechanisms built into widely used electronics systems. It is not surprising that entities involved with ensuring safe and secure systems are continually working on enhancing encryption/decryptions mechanisms. Recently NIST standardized cryptography algorithms… Read More
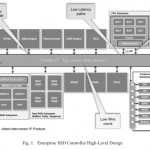
Safety Methods Meet Enterprise SSDs
The use of safety-centric logic design techniques for automotive applications is now widely appreciated, but did you know that similar methods are gaining traction in the design of enterprise-level SSD controllers? In the never-ending optimization of datacenters, a lot attention is being paid to smart storage, offloading… Read More
Supporting ASIL-D Through Your Network on Chip
The ISO 26262 standard defines four Automotive Safety Integrity Levels (ASILs), from A to D, technically measures of risk rather than safety mechanisms, of which ASIL-D is the highest. ASIL-D represents a failure potentially causing severe or fatal injury in a reasonably common situation over which the driver has little control.… Read More
Safety in the Interconnect
Safety is a big deal these days, not only in automotive applications, but also in critical infrastructure and industrial applications (the power grid, nuclear reactors and spacecraft, to name just a few compelling examples). We generally understand that functional blocks like CPUs and GPUs have to be safe, but what about the … Read More
Concluding Inconclusives
Formal methods are a vital complement to other tools in the verification arsenal, but they’re not without challenges. One of the more daunting is the “inconclusive” result – that case where the tool seems to be telling you that it simply gave up trying to figure out if a particular assertion is true or false. Compounding the problem,… Read More
A Functional Safety Primer for FPGA – and the Rest of Us
Once in a while I come across a vendor-developed webinar which is so generally useful it deserves to be shared beyond the confines of sponsored sites. I don’t consider this spamming – if you choose you can ignore the vendor-specific part of the webinar and still derive significant value from the rest. In this instance, the topic is… Read More
Why using new DDR4 allow designing incredibly more efficient Server/Storage applications?
The old one-size-fits-all approach doesn’t work anymore for DDR4 memory controller IP, especially when addressing the enterprise segments, or application like servers, storage and networking. For mobile or high end consumer segments, we can easily identify two key factors: price (memory amount or controller footprint) … Read More