Post-quantum cryptography (PQC) might be a lower priority for many organizations, with the specter of quantum-based cracking seemingly far off. Government agencies are fully sensitized to the cracking risks and the investments needed to mitigate them and are busy laying 10-year plans for migration to quantum-safe encryption. Why such a bold step, given that experts still can’t say precisely when quantum threats will appear? PQShield has released its first installment of an e-book on PQC and crypto modernization subtitled “Where is your Cryptography?” outlining the timeline taking shape and making the case that private sector companies have more exposure than they may realize and should get moving now.
Ten crypto years is not that much time
Folks who survived the Y2K scramble may recall thinking it was far away and probably not as big a problem as all the hype projected. In retrospect, it ended up being a non-event with almost no catastrophic failures – but only because organizations took it seriously, audited their platforms, vendors, and development efforts, and proactively made fixes ahead of the deadline.
PQC has some of the same vibes, with two exceptions. There is no firm calendar date for when problems will start if not mitigated. Many of today’s platforms have crypto technology deeply embedded, and there are no fixes for quantum threats to public-key algorithms short of PQC redesign. It’s fair to say that if an organization doesn’t explicitly understand where platforms have PQC embedded, all platforms without it must be considered vulnerable. It’s also fair to say that the potential for lasting damage is high if a problem starts before a plan is in place.
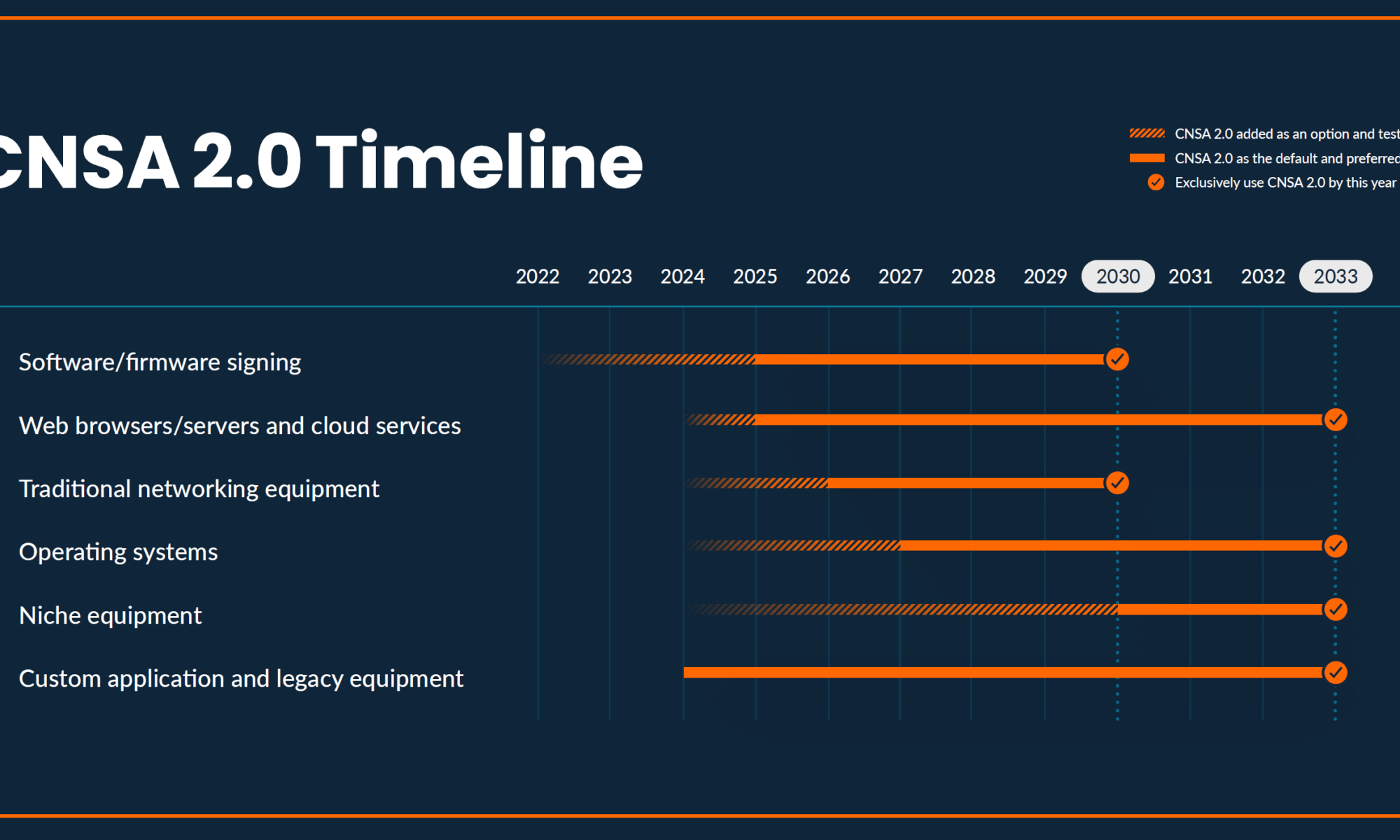
That makes the NSA advisory on the Commercial National Security Algorithm Suite 2.0 (CNSA Suite 2.0) noteworthy. Released in September 2022, it identifies a crypto modernization timeline for six classes of systems with a target of having all systems PQC-enabled by 2033.
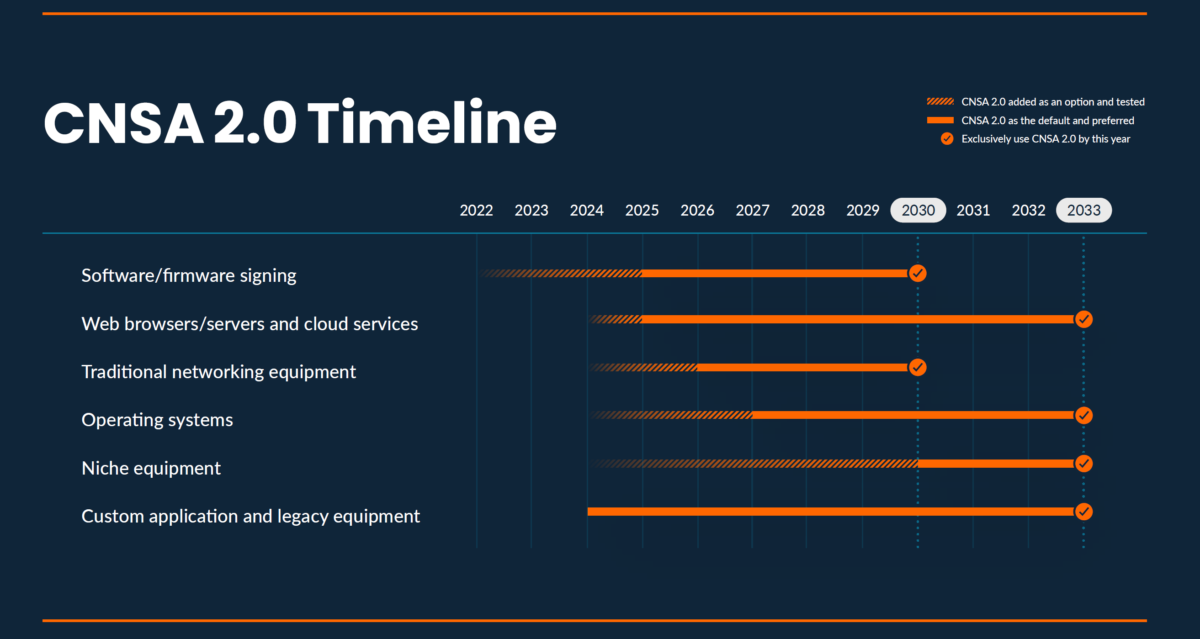
Those earlier milestones for some system classes in the timeline starting in 2025, combined with requiring new full-custom application development to incorporate PQC, shorten the ten-year horizon. PQShield puts it this way in their e-book:
“The message for [public and private sector] organizations is both clear and urgent: the time to start preparing for migration to PQC is now, and that preparation involves assessing and prioritizing an inventory of systems that use cryptography, and are candidates for migration.”
Where to start with crypto modernization
Many veterans who guided organizations through Y2K have retired – but left behind a playbook that teams can use today for crypto modernization. Initial steps involve a risk assessment looking at internally-developed and vendor-supplied systems. Mitigation strategies will vary, with some considerations including how sensitive the data a system handles is, how long that data possibly lives, and if the system is public-facing.
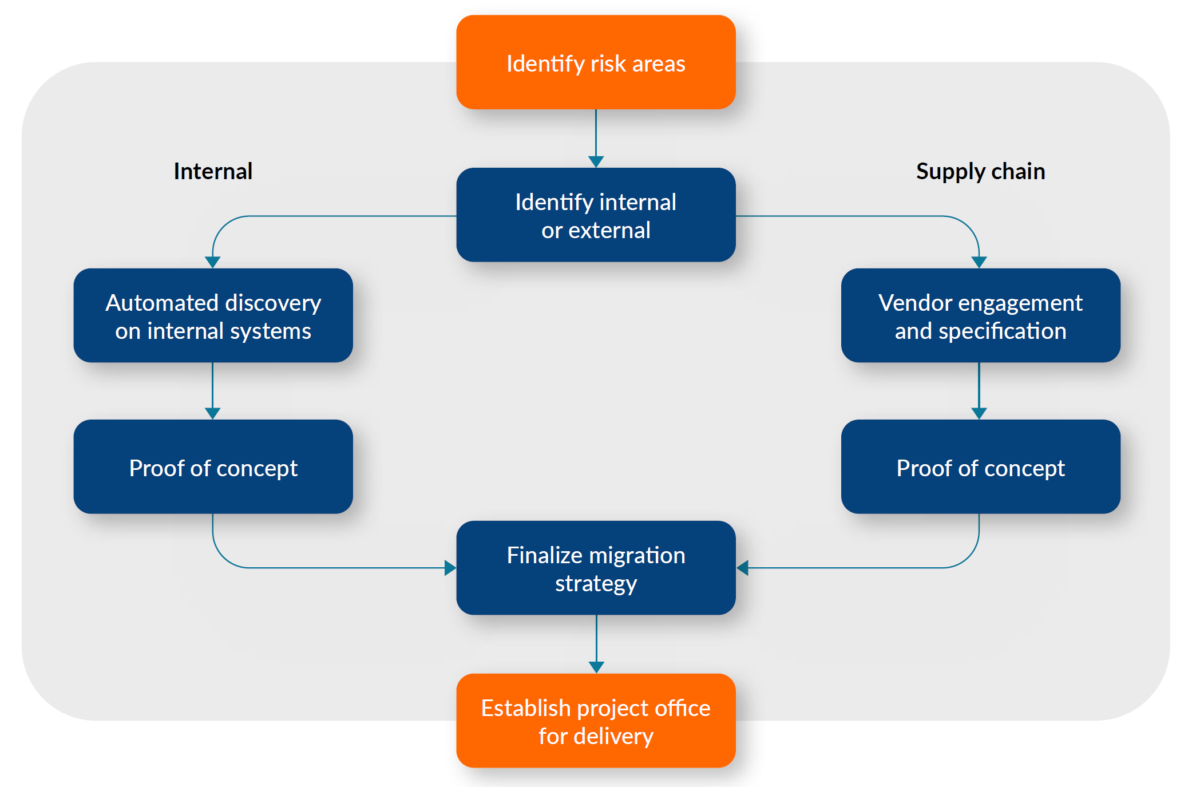
PQShield makes two vital points here. First, it may not be possible, especially for vendor-supplied systems, to make an immediate replacement. Enterprise-class system replacements need careful piloting not to disrupt operations. The good news is for most commercial application and system vendors, PQC will not be a surprise requirement.
The second point is that hybrid solutions may overlap with both PQC and pre-quantum legacy crypto running, with a containment strategy for the legacy systems. This overlap may be the case for infrastructure, where the investment will be enterprise-wide, and the priority may be protecting public-facing platforms with PQC first.
Moving to an industry-specific discussion for PQC
After discussing infrastructure concerns in detail, PQShield devotes about half of this e-book installment to industry-specific considerations for PQC. They outline ten industries – healthcare, pharmaceuticals, financial services, regulatory technology, manufacturing, defense, retail, telecommunications, logistics, and media – highlighting areas needing specific attention. The breadth of the areas discussed shows how many systems we take for granted today use cryptography and will fall vulnerable soon.
Crypto modernization is a complex topic, made more so by the prevalence of crypto features in many vendor-supplied systems organizations don’t directly control. Awareness of timelines in place, along with places to look for vulnerabilities, is a meaningful discussion.
To download a copy of the e-book, please visit the PQShield website:
Cryptography Modernization Part 1: Where is your Cryptography?
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.