In a recent marketing campaign, WhatsApp (and by extension, its parent company Meta) mocks the ubiquitous but unsecure messaging vehicle, SMS, saying anyone can read plain texts and mobile users should use some means of secure messaging. Apps like WhatsApp, Messenger, iMessage, and WeChat have each attracted over 1 billion users with the promise of security. But what happens to secure messaging in a post-quantum world? Those numbers make messaging apps a lucrative target for quantum computer cracking.
PQShield cryptography researchers are teaming with other experts worldwide to get ahead of what could be a huge problem for mobile users. In a recently archived webinar, Thomas Prest of PQShield presents his case for applying post-quantum cryptography to secure messaging apps, and it’s a fascinating discussion. He summarizes the challenge this way:
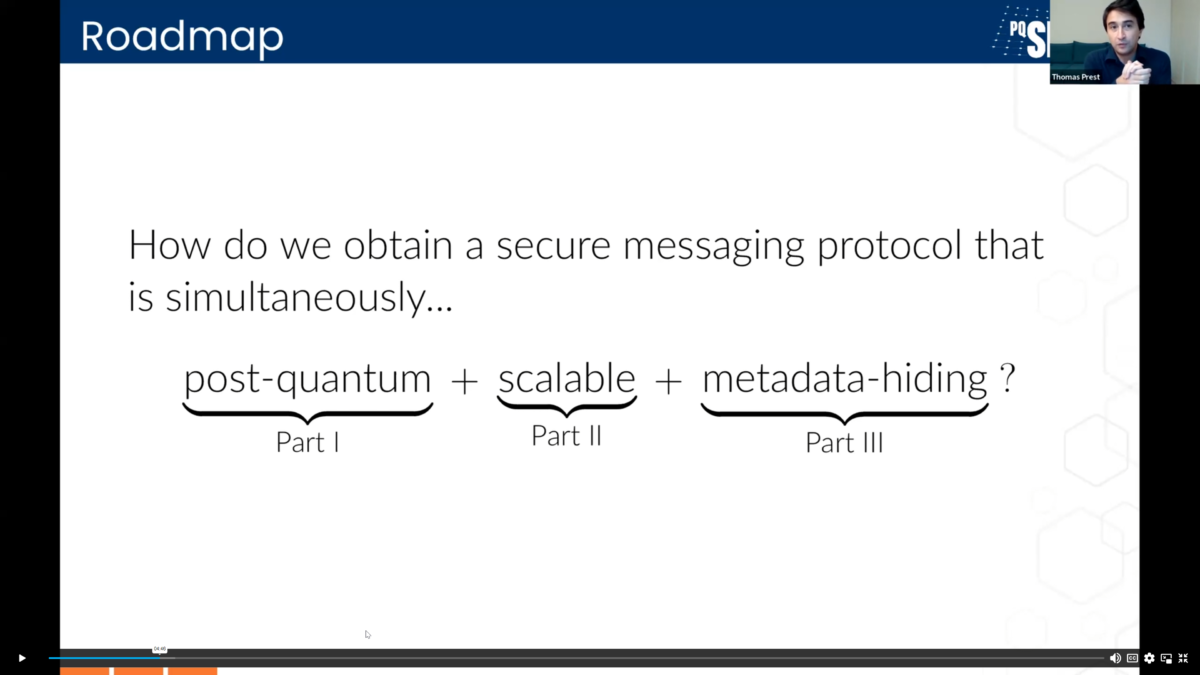
We often see discussion around one of those dimensions, but this is the first time I’ve seen someone take on the bigger picture where a solution must address all three simultaneously. Let’s quickly dive into some key points in each of those three areas.
Messaging crypto has run into interoperability inertia
Interoperability is a prerequisite for messaging apps to work. It gets much more difficult when parties have no specific prior knowledge of each other. Underneath several popular messaging apps is the Signal secure messaging protocol, which has built inertia.
Fun fact #1: the method for securely exchanging cryptographic keys over a public channel dates back to a 1976 paper by Whit Diffie and Martin Hellman, which identified what is now broadly known as Diffie-Hellman key exchange.
Fun fact #2: Signal uses a more recent extension, the triple elliptic-curve Diffie-Hellman (3-DH) handshake, in conjunction with the Double Ratchet algorithm and 256-bit encryption primitives. Signal was first proposed in 2013, grew with several revisions, and was blessed secure by several independent efforts in 2016 and 2017.
Prest describes updating the handshake to PQ X3DH, replacing Diffie-Hellman 3-DH with a post-quantum hardened key encapsulation mechanism (KEM) plus ring signatures on top of the symmetric crypto primitives. Similarly, he wants a KEM-based PQ Double Ratchet update.
Pairwise messaging blows up data requirements
The exponential growth in network traffic between a large cloud of pairwise interconnected points is well understood. Latency gets gnarly when encryption layers on top of every connection, and device complexity must rise to keep pace.
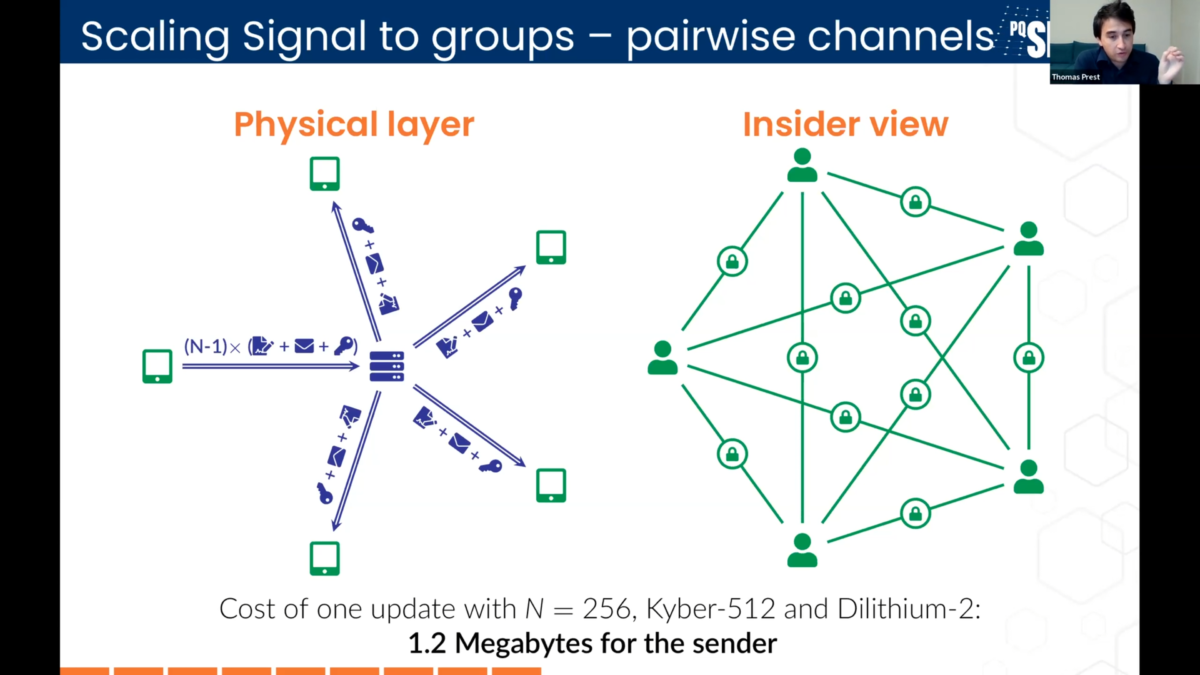
Scalability means rethinking how much mobile data moves in supporting encryption. Prest advocates moving to one channel with a single shared secret key for the whole group, combined with one signature and one private encryption key to authenticate. Compressing ciphertexts then becomes possible, cutting network bandwidth costs.
Metadata is collected all over social networks
While the messages may be secure, sadly, the metadata isn’t. Recent revelations show US law enforcement agencies can strip metadata from monitored social network conversations in real-time. There’s also the server-in-the-middle consideration, with the question of whether a server can be trusted during a conversation and not give up details later.
“Hiding” a device from a server is a logical approach, but if done improperly, a messaging network falls prey to some problems. Encrypting all packages with a key can enable one user to upload garbage to an entire group. Encrypting everything except the signature allows linking a signature back to a sender. Prest illustrates a post-quantum solution where a signature keypair is derived from a key, and group members authenticate anonymously.
Facing the prospect of instant obsolescence
Why should the semiconductor community care about how secure messaging evolves? It’s an excellent example of a use case for post-quantum crypto IP. SoCs and devices in design now may become obsolete instantly at some point soon if they don’t incorporate post-quantum technology. There’s a risk that some algorithms and protocols are still in flux. PQShield is thinking through the landscape and how its IP helps designers stay updated.
This archived webinar on secure messaging in a post-quantum world is a 32-minute presentation, followed by a 13-minute Q&A session where researcher Shuichi Katsumata joins his co-author Prest to elaborate on concepts they published together. Viewers can see the event here; no registration is required.
PQShield WEBINAR: Secure messaging in a post-quantum world
Also Read:
NIST Standardizes PQShield Algorithms for International Post-Quantum Cryptography
Post-quantum cryptography steps on the field
CEO Interviews: Dr Ali El Kaafarani of PQShield
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.