News of cyberattacks is routine these days in spite of the security mechanisms built into widely used electronics systems. It is not surprising that entities involved with ensuring safe and secure systems are continually working on enhancing encryption/decryptions mechanisms. Recently NIST standardized cryptography algorithms for the post-quantum computing world. PQShield is a company that is at the forefront of post-quantum cryptography and developing solutions to protect systems against quantum cyberattacks. The company announced that NIST has adopted an algorithm PQShield developed as one of several new post-quantum cryptography standards. An additional PQShield developed algorithm is moving to Round 4 of the NIST post-quantum cryptography standardization project.
To understand the significance of NIST’s standardization and PQShield’s announcement, it is important to get an overview of why new standards are needed, what the standardization process entails and how to deploy the new standards in one’s systems. PQShield has published three technical whitepapers that together cover the subject matter in detail. If you are involved in developing chips and software to deliver cybersecurity solutions, these whitepapers would be very informative. Links to download these whitepapers can be found in relevant sections of this blog.
The Threat from Quantum Computers
A quantum computer can perform computations much more efficiently than classical computers that have been common place to date. Maybe twenty years ago, quantum computing appeared far away, but we are now much closer to seeing quantum computers in commercial deployment. While this is great from a computing perspective, quantum computing capabilities can also easily break current security mechanisms.
RSA and ECC cryptosystems that are currently in use for secure data transmissions are easy for quantum computers to solve using Shor’s algorithm. This will open up systems for forgery of digital signatures (Integrity compromise) and decryption of previously encrypted data (Confidentiality compromise) in the future. This latter threat is considered the “Harvest Now, Decrypt Later (HNDL)” attack. Without being discovered, would-be attackers are regularly collecting and storing encrypted data with the expectation of deciphering the stolen data using quantum computers.
Based on history, we know it takes a long time to upgrade to new security standards. For example, the migration from Data Encryption Standard (DES) to Advanced Encryption Standard (AES) has taken decades. To be specific, the National Institute of Standards and Technology (NIST) established the AES standard in 2001. As such, newer security standards have to be established now, to protect against cyber threats from quantum computers.
Post-Quantum Cryptography (PQC)
The best way to mitigate the threat of attacks using quantum computers is to use quantum-safe cryptography. This post-quantum cryptography is being mandated by governments across the world for adoption by businesses who want to do business with these governments. With a likely deadline for adoption within the next three years, businesses will be forced to implement quantum-safe mechanisms quickly. But without a standard for international adoption, interoperability will become a practical roadblock.
For a detailed overview of Post-Quantum Cryptography, download this whitepaper.
The NIST Standardization Process
While a number of standardization efforts are currently underway (in Europe, China, etc.,), the NIST standardization project is the most well documented. The project was announced in 2016 with the goal of standardizing post-quantum signature schemes and key-establishment schemes.
In July 2022, NIST announced that it has selected the following three signature schemes as standards for PQC.
Primary standard: Dilithium
Secondary standard: Falcon
Secondary standard: SPHINCS
The Dilithium and Falcon standards are based on hardness assumptions about structured lattices and the SPHINCS standard is based on hardness assumptions about hash functions. The following Figure shows the process that was followed leading to the selection of the standards for signature schemes.
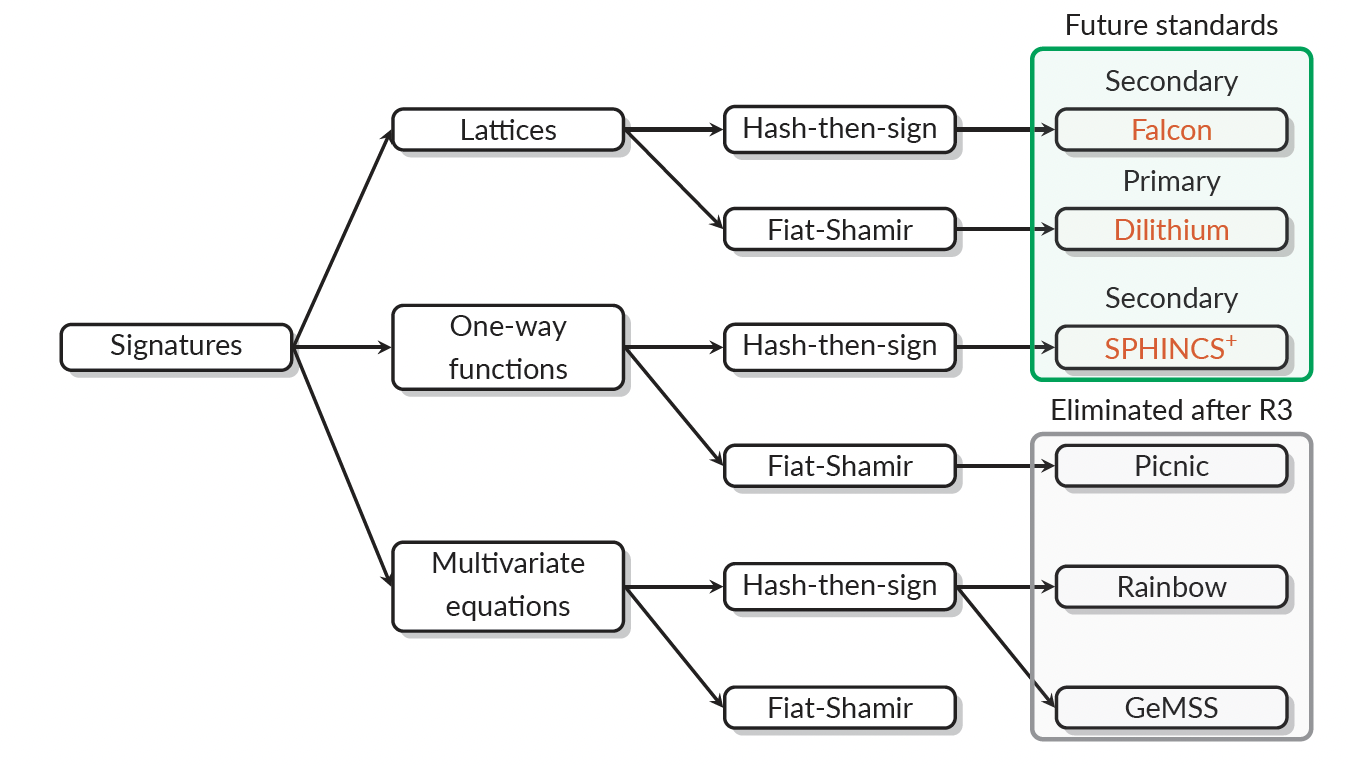
NIST also announced the following regarding key-establishment schemes.
Standardized scheme: Kyber
Back-up for standardization: NTRU (might be standardized if Kyber patent negotiations fail)
Schemes For further study: BIKE, Classic McEliece, HQC and SIKE
The following Figure shows the process that was followed leading to the selection of the standard for the key establishment scheme.
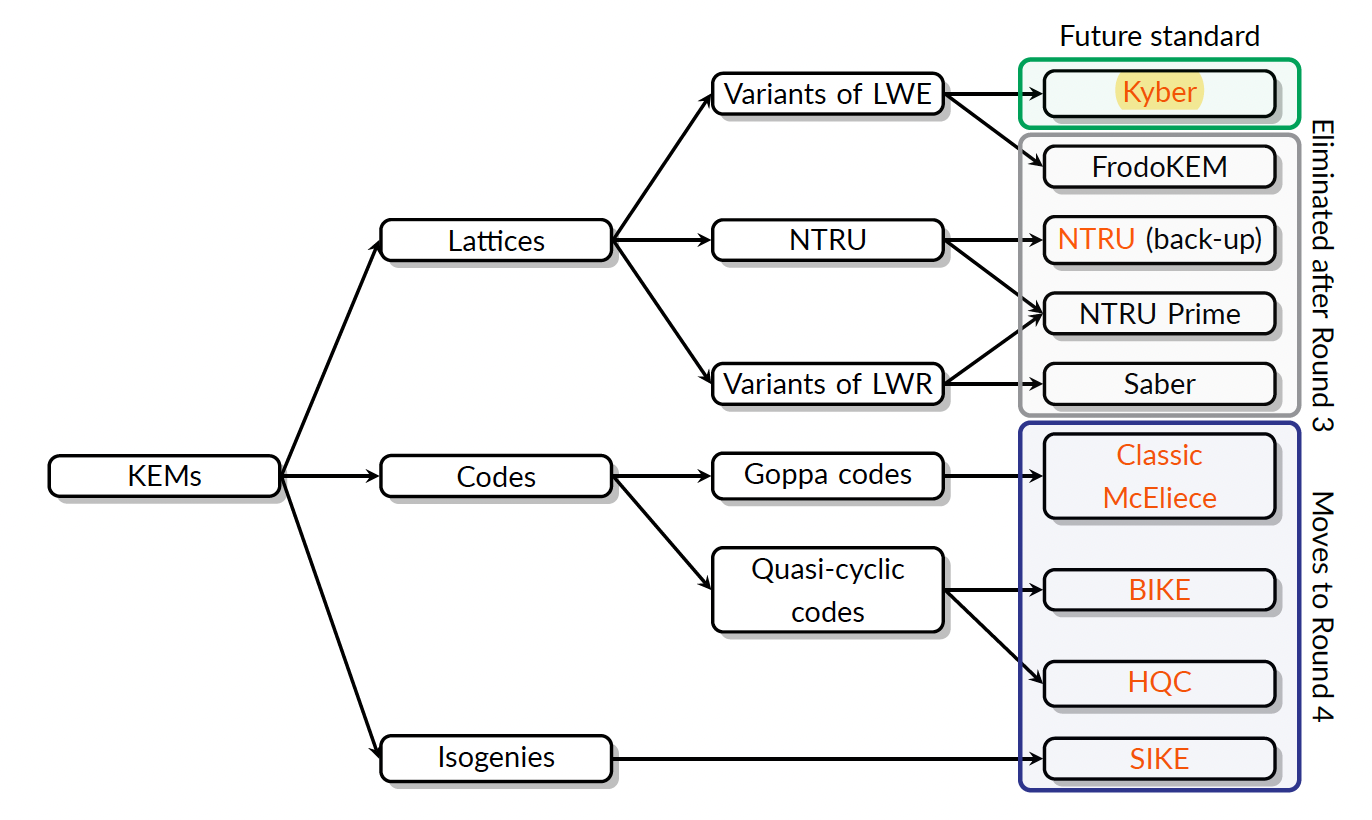
For full details of the various NIST standards addressing PQC, download this whitepaper.
PQShield’s Role in the NIST Standardization Project
PQShield has been heavily involved in the NIST standardization project right from the start, developing and submitting various signature and key-establishment schemes for consideration as standards.
To hear about the NIST PQC standardization journey to date and what is expected going forward, watch our interviews with leading cryptographers Dr. Thomas Prest and Prof. Peter Schwabe.
Prof Peter Schwabe co-authored seven of the PQC schemes that were submitted to NIST, of which three (Kyber, Dilithium and SPHINCS) were established as NIST standards in July 2022. Another scheme (Classic McEliece) is going into Round 4 for consideration to be a standard.
Dr. Thomas Prest co-authored the compact and efficient Falcon signature scheme. Falcon was selected in July 2022 as a NIST standard for PQC signature schemes.
PQShield’s press announcement regarding the recently announced NIST standards for PQC can be accessed here.
Roadmap to PQC
As we start the transition phase to PQC, NIST has allowed for Federal Information Processing Standards (FIPS) certified solutions to be used in combination with one or more PQC schemes. This accommodation allows for the adoption of quantum-resistant schemes while still keeping the solutions FIPS certified. PQShield’s whitepaper titled “NIST PQC Standards are here – How can you keep ahead” offers a clear roadmap to follow when implementing PQC in one’s systems.
Summary
Being involved in the development and standardization process of PQC algorithms, PQShield has the advantage of developing solutions ahead of the final result. PQShield is an algorithm-agnostic vendor, offering size optimized and side-channel resistant implementations capable of utilizing all relevant NIST PQC finalists in hardware and software. It could support companies in their transition to quantum-readiness from legacy encryption schemes to the latest standards based solutions. Given the short deadline on post-quantum cryptography adoption mandate, it may be in the best interest of companies to explore PQShield’s solutions for implementation.
For more details about PQShield and its offerings, visit PQShield’s website.
Also Read:
WEBINAR: Secure messaging in a post-quantum world
Post-quantum cryptography steps on the field
CEO Interviews: Dr Ali El Kaafarani of PQShield
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.