As RISC-V adoption accelerates across the semiconductor industry, so do the concerns about hardware security vulnerabilities that arise from its open and highly customizable nature. From hardware to firmware and operating systems, every layer of a system-on-chip (SoC) design must be scrutinized for security risks. Unlike software, hardware is extremely difficult to patch after deployment—making early vulnerability detection critical. The rapidly growing number of hardware CVEs (Common Vulnerabilities and Exposures) reported by NIST underscores the seriousness and increasing sophistication of hardware-based threats.
At the core of these vulnerabilities are underlying weaknesses—the root causes that leave a system exposed. A weakness, as defined by MITRE, is a design flaw or condition that could potentially be exploited. These are cataloged in the Common Weakness Enumeration (CWE) database, while actual vulnerabilities (exploitable instances of those weaknesses) are tracked in the CVE database.
At Andes RISC-V CON last week, Will Cummings, senior security applications engineer from Cycuity, gave a talk on enhancing RISC-V CPU security.
MITRE CWE Framework for Hardware
MITRE’s CWE is a well-established, open framework in software and a growing presence in hardware. It now includes 108 hardware-specific CWEs across 13 categories, providing a structured and actionable way to identify, prevent, and verify fixes for known hardware design weaknesses. Categories include areas such as general logic design, memory/storage, cryptography, and transient execution, among others.
Why CWEs Matter for RISC-V
RISC-V and CWE share a foundational philosophy of security through openness. RISC-V, developed collaboratively as an open standard, aligns with Auguste Kerckhoffs’ principle: a system should remain secure even if everything about it is public. Similarly, CWE is an open, community-maintained repository that promotes transparency and standardization in security classification. This shared ethos makes CWE a natural fit for securing RISC-V designs.
Security analysis of typical RISC-V processor IPs shows that roughly 65% of all 108 hardware CWEs are applicable. In some categories—like core logic, memory, cryptography, and debug/test—over 70% of CWEs are relevant. This makes CWE a powerful tool for prioritizing and addressing security concerns in RISC-V development.
New Microarchitectural CWEs for Transient Execution
In early 2024, MITRE introduced new CWEs targeting microarchitectural weaknesses, developed with contributions from Arm, AMD, Cycuity, Intel, and Riscure. These CWEs address vulnerabilities associated with transient execution attacks, which have gained prominence because of exploits like Spectre and Meltdown:
CWE-1421: Shared Microarchitectural State — Core to most transient execution attacks
CWE-1422: Stale Data Forwarding — Enables forwarding of data to a shared resource
CWE-1423: Integrity of Predictors — Focuses on corrupted branch predictors
These weaknesses fall under CWE-1420: Exposure of Sensitive Information during Transient Execution, which is itself part of the broader hardware design category under CWE-1194.
A Structured Approach to Security: From Weakness to Verification
The proposed CWE-based framework maps weaknesses to specific security protection requirements, which then support yet more specific security properties. These in turn yield evidence from simulation, emulation, or formal methods. This structure helps ensure that every security requirement is grounded in a recognized weakness and backed by verifiable proof.
Cycuity’s Role: Scalable, Architecture-Agnostic Security Verification
Cycuity plays a vital role in this process by offering early-stage security verification for hardware design. Its flagship product, Radix, uses information flow analysis to track how secure assets (e.g., encryption keys) move through hardware, firmware, and across boundaries between secure and non-secure domains. It simulates how attackers might exploit design flaws such as improper access control or leakage via shared microarchitectural resources, enabling early detection—before the chip is even built.
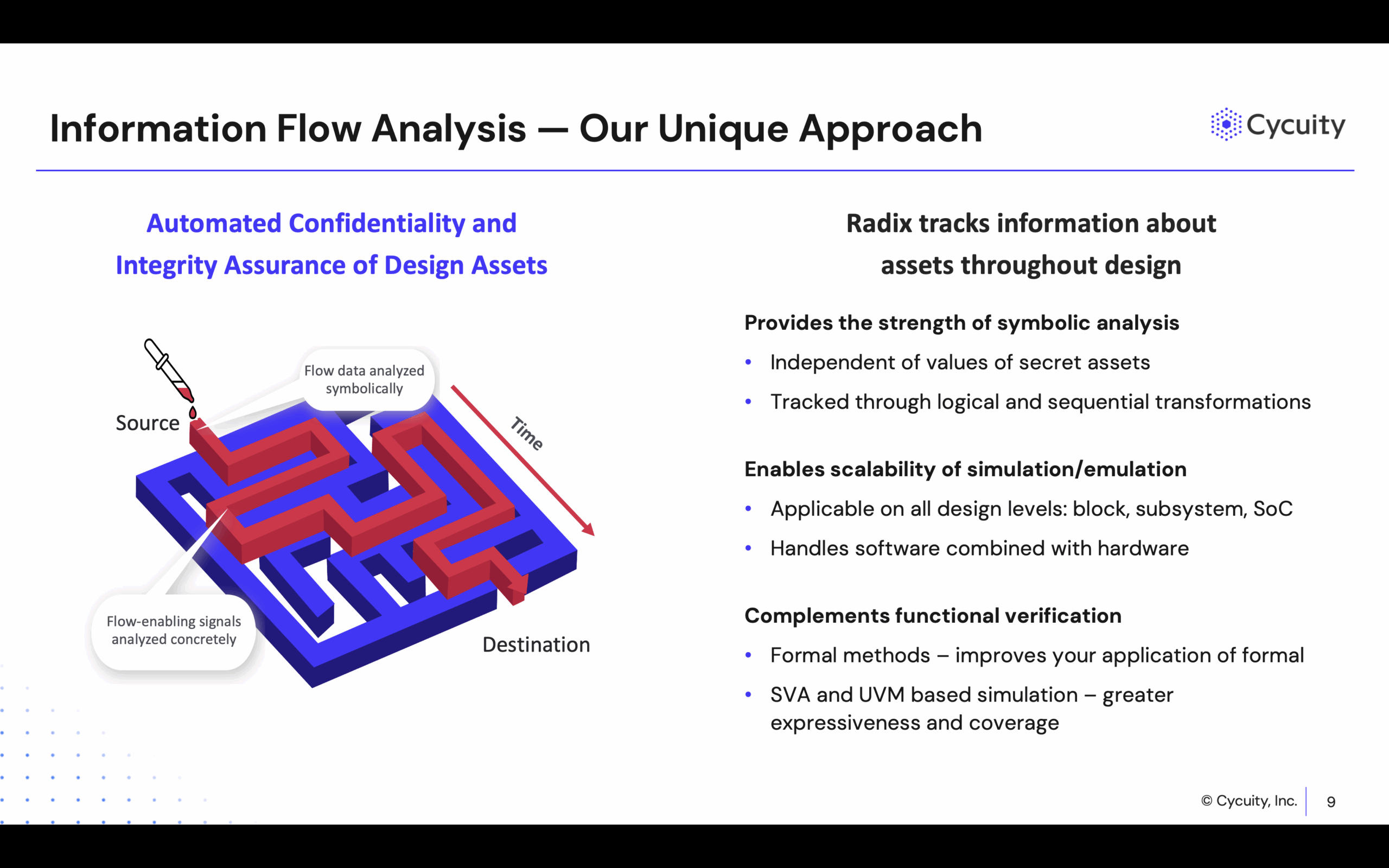
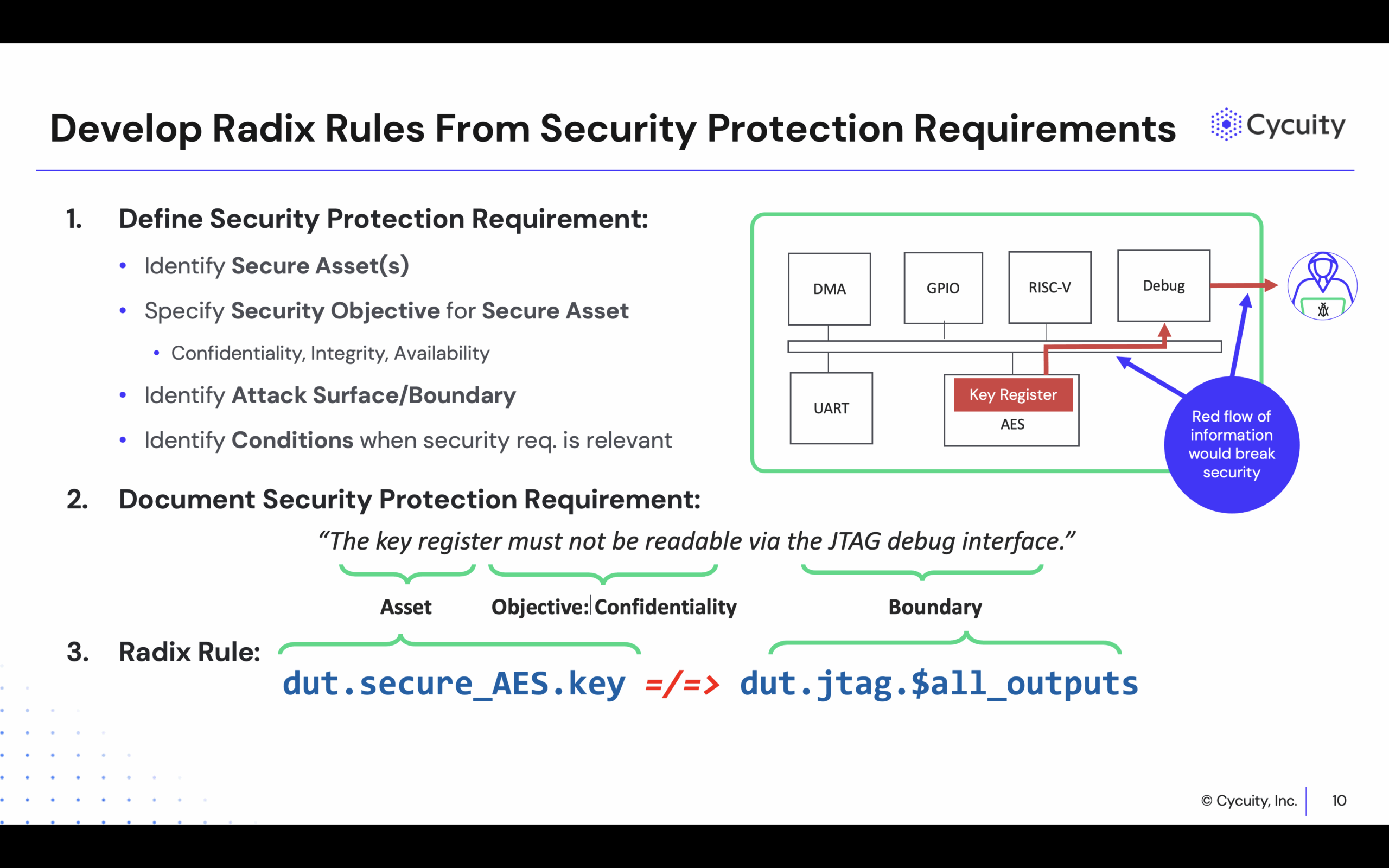
While Radix is well-aligned with RISC-V’s modular architecture, it is architecture-agnostic and effective across all processor architectures and custom silicon as well. It integrates easily into standard SoC development workflows, including simulation, emulation, and formal verification environments. It also supports firmware-in-the-loop analysis and aligns with industry standards like CWE—ensuring security is both proactive and measurable.
Mutual Benefit: MITRE and RISC-V
MITRE and RISC-V International benefit from each other through their shared commitment to openness, transparency, and community collaboration. RISC-V offers a flexible, open platform where MITRE’s security frameworks like CWE can be directly applied and validated. In turn, MITRE enhances RISC-V security by enabling a systematic, standard-based approach to identifying and mitigating hardware design flaws.
Summary
The CWE framework provides a practical, structured methodology to enhance RISC-V security—starting from known weaknesses, mapping them to protection goals, and verifying that those goals are met. Combined with tools like Radix from Cycuity, which enable scalable, architecture-agnostic vulnerability detection, the industry now has the means to address hardware security earlier and more effectively.
Learn more at Cycuity.
Also Read:
CEO Interview: Dr. Andreas Kuehlmann of Cycuity
Cycuity at the 2024 Design Automation Conference
Hardware Security in Medical Devices has not been a Priority — But it Should Be
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.