Key Takeaways
- Secure-IC presented AI-powered cybersecurity with a focus on the Securyzr™ Intrusion Detection System (IDS) during the IP-SoC Silicon Valley 24 event.
- The Securyzr™ IDS features include threat detection, analysis, response, and lifecycle management, leveraging both rule-based and AI methodologies.
- The system is hardware agnostic and can easily integrate with security components like the Securyzr ISE, making it suitable for various applications.

Design & Reuse held its IP-SoC Silicon Valley 24 event on April 25th, 2024, at the Hyatt Regency Santa Clara. The agenda was packed with many relevant and compelling presentations from companies large and small. I attended one presentation on security that stood out for me. Secure-IC presented “AI-powered cybersecurity: Securyzr™ Intrusion Detection System (IDS)”. The presentation discussed a comprehensive approach to system security that includes both hardware and software. The addition of AI makes it even more potent. Security is a growing issue in our industry, and we need more focus on the problem. I’ll review one example of this needed focus as Secure-IC presents AI-powered cybersecurity.
Presentation Overview

Yathiendra Vunnam gave the presentation. He is a Field Application Engineer at Secure-IC. This allows him to participate in Secure-IC’s development in the United States in various verticals such as automotive, semiconductor, defense, space, and IoT. He holds an MS degree in Cybersecurity from Georgia Institute of Technology, so security is something he has a passion for.
His presentation began with a description of the problem and the mission of Secure-IC:
IoT devices being interconnected, each and every object could be a threat for the whole network. Therefore, the security of the objects or the devices with their lifecycle management is key, and so is their data. To ensure the integrity of this data, the whole system must be secured and managed. Trusted devices enable trusted data.
Secure-IC partners with its clients to provide them with the best end-to-end cybersecurity solutions for embedded systems and connected objects, from Chip to Cloud
The “punch line” of this statement in the presentation is the graphic at the top of this post. Sercure-IC is a unique company that provides a wide array of security solutions. You can get a feeling for the breadth of the company’s impact here.
Intrusion Detection
Next, Yathiendra discussed Secure-IC’s Securyzr™ intrusion detection system (IDS). The goal of this technology is to maintain trust throughout the whole device lifecycle. Features of this technology include:
- Threat Detection: Monitors CPU and memory activity, network traffic (CAN bus, Ethernet) and more
- Threat Analysis: Rule-based or AI methodology to discriminate alerts and eliminate false positives
- Threat Response: Immediate local threat response based on pre-defined rules and leveraging edge AI computing
- Life Cycle Management: The acquired data from IDS are sent to the Securyzr Server in the cloud, facilitating device life cycle management for the entire fleet of devices
- Securyzr iSSP Integration: IDS can be employed in the monitoring service of iSSP, providing a comprehensive solution for fleet-wide security management.
Next, Yathiendra discussed the Intrusion Detection System (IDS), which is a pure software solution that offers:
- Answer to new cybersecurity regulations
- Real-time monitoring of cybersecurity threats on a fleet of edge devices with alarms
- Cloud-based dashboards
- Cloud-based fleet data aggregation and processing for global updates based on rich data sets edge processing for fast mitigation
- Minimal cost of implementation and integration in existing hardware solutions
- Integration with Securyzr Server services
- Leveraging of Secure-IC Securyzr integrated Secure Elements features
Next, AI-powered cybersecurity was discussed. This technology was summarized as follows:
Data collection
- Collecting information coming from host CPU (buses, sensors, and security components such as the integrated secure element Securyzr iSE which may be included in the system SoC)
Threat Detection
- Real-time anomaly detection on advanced techniques using rule-based & AI/ML methodology with the reduced rates of FN/FP (false negative / false positive)
- Novelty detection (with nominal behavior)
- In case Secure-IC Digital Sensors are implemented in the SoC, AI ML-based SW smart monitor is used to analyze the answers from these sensors and reach a conclusion on the detected threat
Threat Response
- Immediate threat response based on pre-defined alert detection
- Based on full software AI with model stored in the host for fast simple response
- More complex situations may be managed by software AI module at the server side
Automotive Use Case
Yathiendra then described an automotive use case for the technology. He went into a lot of detail regarding where and how the technology is deployed. The diagram below summarizes how IDS is part of an end-to-end detection and response solution.
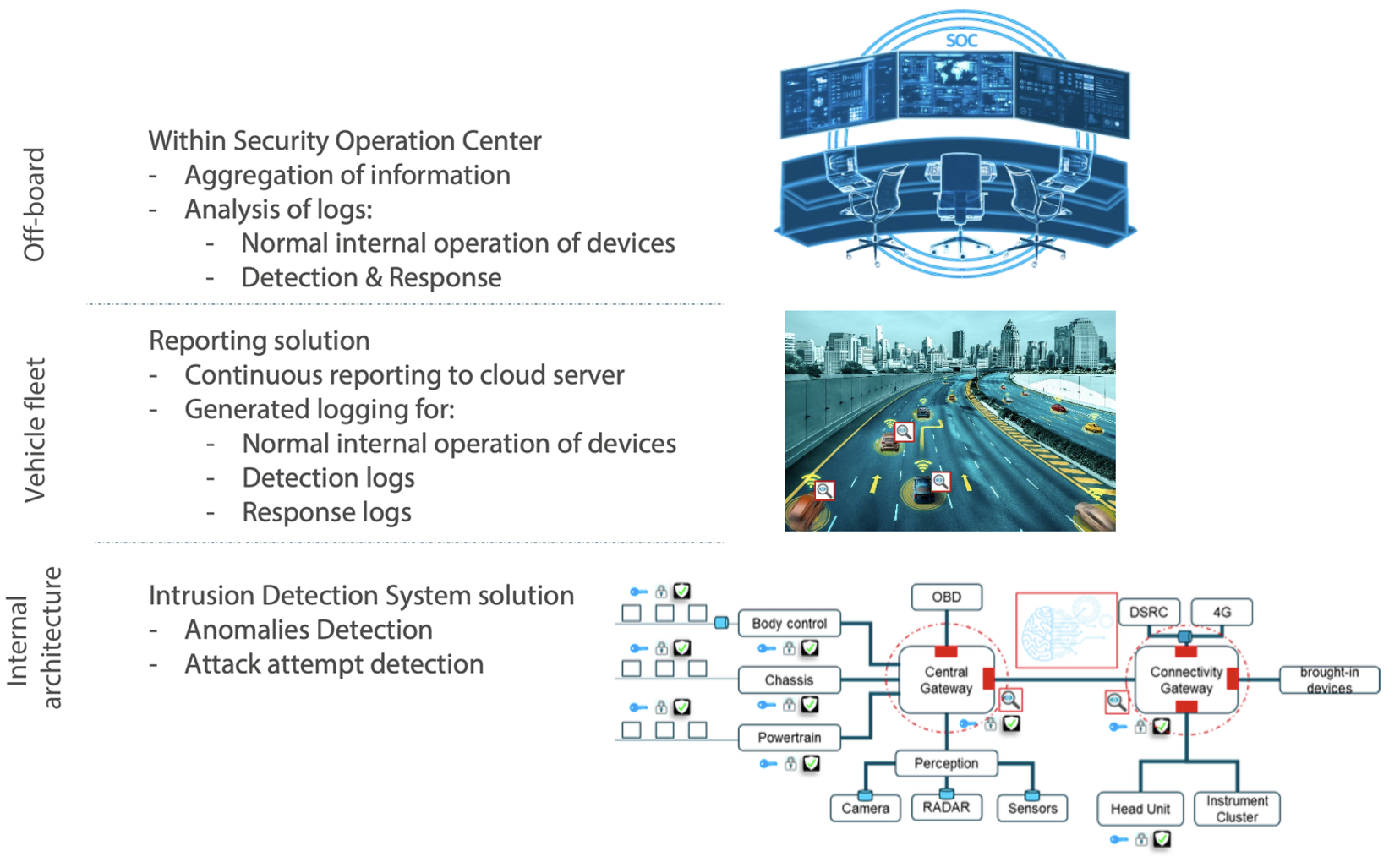
Final Thoughts and to Learn More
Yathiendra conclude his talk with the following points:
- Intrusion Detection System is included in an edge device and can monitor network buses, sensors,…
- The system verifies in real time whether each of your connected devices is attacked and sends information to your supervising infrastructure
- The system is hardware agnostic – it runs on a CPU with OS
- The system can easily interface with security component Securyzr ISE and take advantage of its features (sensors)
This was a very relevant and useful presentation on a holistic approach to security. You can learn more about the breadth of technology solutions offered by Secure-IC here. And that’s how Secure-IC presents AI-powered cybersecurity.
WEBINAR: Redefining Security – The challenges of implementing Post-Quantum Cryptography (PQC)
Also Read:
How Secure-IC is Making the Cyber World a Safer Place
2024 Outlook with Hassan Triqui CEO of Secure-IC
Rugged Security Solutions For Evolving Cybersecurity Threats
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.