I have attended LETI conference last June and remember the paper presented by Alain Merle, their security guru. Alain said that smart cards are secured because up to 50% of the Silicon area is dedicated to security. When you design a SoC to address applications like smart metering, NFC payment or embedded SIM, you know in advance that these will require more protection, but your challenge is to define a competitive architecture.
The chip area may increase if you implement certain feature in H/W instead in S/W to improve the level of security, but if your architecture is smart enough, the chip area will not necessarily double. Synopsys is proposing a good illustration of this concept with the Trusted Execution Environments (TEE), allowing creating a secure perimeter in the SoC. If TEE is still unclear for you, take a look at the picture below, or, even more efficient, listen to thiswebinar “Balancing Advanced SoC Security Requirements with Constrained Area and Power Budgets”.
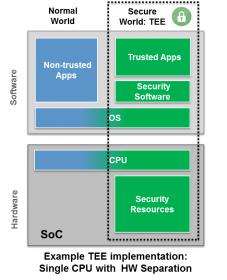
There’s different ways of implementing a trusted execution environment. A simple way would be using a physical separate module, or on a SoC, use a separate CPU. But a more efficient solution, instead of using a second CPU or even a separate module, is when the trusted and the normal computation can be combined on a single processor.
The designer can define a secure, isolated area of the processor to guarantee code and data protection for confidentiality and integrity where you can securely run software, trusted software. So, the environment basically guarantees confidentiality, integrity, and authenticity of the software running in that trusted execution environment. The designer can now separate the application in parts that are less security critical and parts that are more secure critical. For the less secure critical, you apply normal software engineering. For the highly secured or the highly secure critical part, you can do additional security hardening.
The memory is protected by using secure MPU with per region scrambling protects memory based on privilege levels based on privilege levels. Accesses to secure peripherals and system resources are restricted by using secure APEX or system bus signaling. In secure mode, the Trusted Execution Environment can’t be accessed from the peripherals.
Synopsys ARC processors are actually extendable processors as users can (at design time) add their own instructions, this is APEX technology: ARC processor extensions. Access to those extensions can be controlled making the extensions very secure by using SecureShield technology. SecureShield enables you to combine trusted and normal applications on a single processor, and resources can be shared.
ARC EM CPU pipeline has been designed to be tamper resistant as there is no store in the 3-stages pipeline. The CPU can detect tampering and software attacks, thanks to integrated watchdog timer detecting system failures and enable counter measures.
In fact, ARC-EM Enhanced Security Package interleaves protected processor pipeline registers and in-line instruction and data encryption ensure decrypted instructions are never stored or accessible, protecting algorithms from reverse engineering without impact to the timing of instructions. Sourcing both the processor IP and the security package to the same provider is the key for maximum protection allowing optimized implementation, reducing area and power consumption.
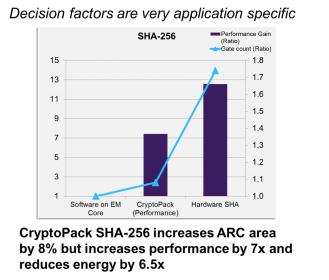
The Enhanced Security Package with SecureShield is a part of Synopsys’ comprehensive portfolio of security IP solutions, which also includes the CryptoPack option for ARC EM processors as well as the DesignWare Security IP solutions, which comprise a range of cryptography cores and software, protocol accelerators, root of trust, platform security and content protection IP. On top of these security hardware features, Synopsys provides content protection, platform security and cryptographic cores. The designer will benefit from common crypto algorithms such as AES, 3DES, ECC, SHA-256 or RSA.
During this webinar, Ruud Derwig, who started his career at Philips Corporate Research, worked as a Software Technology Competence Manager at MXP Semiconductors, and now Software and Systems Architect at Synopsys will tell you many, many things about security. You will learn about side channel analysis, the non-pervasive attacks using information leaked by an implementation, like simple power analysis (SPA) or differential power analysis (PPA), which can reveal secrets, like cryptographic keys. You will also learn how to use simulation based power analysis to implement counter measures against the power analysis for data dependency.
This webinar is essential as the description of the various threats is very precise, so you clearly understand how the security can be built by using the different solutions proposed by Synopsys. Instead of providing “one size fits all” type of solutions, Synopsys propose various techniques to implement the right level of security in respect with the applications, taking into account the specific power, performance and area requirements.
You can attend to a webinar replay here.
From Eric Esteve from IPNEST
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.