One of the challenges in the RISC-V bid for world domination may be security. That may seem like a silly statement, given that security weaknesses are invariably a function of implementation and RISC-V doesn’t define implementation, only the instruction-set architecture (ISA). But bear with me. RISC-V success depends heavily… Read More
Tag: side channel
Timing Channel Attacks are Your Problem Too
You’ve heard about Meltdown and Spectre and you know they’re really bad security bugs (in different ways). If you’ve dug deeper, you know that these problems are related to the speculative execution common in modern processors, and if you dug deeper still you may have learned that underlying both problems are exploits called timing… Read More
Meltdown, Spectre and Formal
Once again Oski delivered in their most recent Decoding Formal session, kicking off with a talk on the infamous Meltdown and Spectre bugs and possible relevance of formal methods in finding these and related problems. So far I haven’t invested much effort in understanding these beyond a hand-waving “cache and speculative execution”… Read More
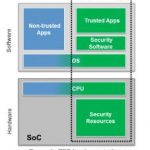
How to Secure a SoC while Keeping Area and Power Competitive?
I have attended LETI conference last June and remember the paper presented by Alain Merle, their security guru. Alain said that smart cards are secured because up to 50% of the Silicon area is dedicated to security. When you design a SoC to address applications like smart metering, NFC payment or embedded SIM, you know in advance … Read More