Did you know that by 2020 90% of cars will be connected to Internet? Great, but today, there are already more than 100 car models affected with security flaws (Source: theguardian.com, 2015). That 320 apps are installed on average smartphone device? It would be a complete success, but 43% of Android devices allow installation of unverified apps (Source: Slideshare.net, 2015). Let’s talk about IoT, according with HP Fortify study made in 2014, 70% of most IoT devices contain serious security vulnerabilities. These statistics sounds like security is still considered by the system designers as a luxury option, like was for example the simulation of an electronic design in the 1980’s. Just before efficient and user-friendly simulators become to be used by most of the design team and EDA become a real market. The dissemination of connected cars and devices is exploding, but we are still in the early days of security IP systematic usage.
The demand for an always more connected world is pushing threats on the increase, the scenario are multiples. You may expect to suffer from theft & replacement of credentials, rogue devices connected to the internet, attacks to other devices connected to a network, happening at home or at your professional environment. In the industry, companies may be weakened by software and IP theft or tampering, cloning or snooping of sensitive data. To make it short, individuals and companies need to be protected when using connected systems or these systems need to integrate the most efficient security IP to protect users.
Elliptic has been completely focused on security since the company foundation and the acquisition by Synopsys has allowed furthering extending the security IP port-folio development.
Cryptography IP
Supporting the latest standards like AES, SHA-2, SHA-3, PKA or TRNG, these cryptographic algorithms can be implemented in HW or SW and highly configurable for optimal size or performance. For example, pipelined AES core variants scale to 100+ Gbps performance. Integrating security IP enable the development of customized IP subsystems or building blocks for security protocols accelerators.
Platform Security: tRoot
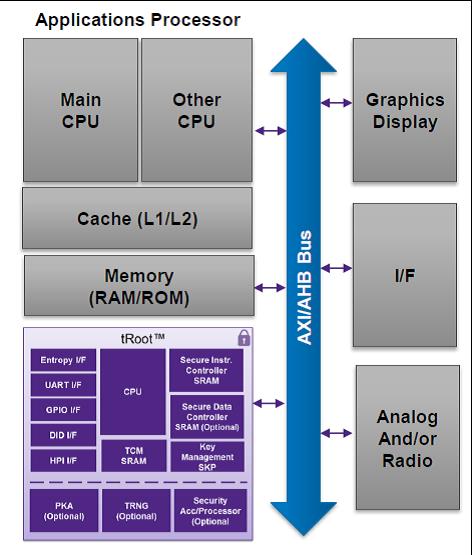
Synopsys tRoot is a secure hardware Root of Trust, an embedded security module providing chipsets with their unique identity that can’t be tampered with. tRoot is made of hardware plus firmware and provides safe environment to create, store and manage secrets critical for the system, like keys, certificates and other data. You can see a typical tRoot implementation in an application processor in the above picture.
Security Subsystems: Content Protection
Elliptic is providing HDCP 2.2 content protection IP for Miracast, HDMI and DisplayPort. This IP, certified both for Transmit and Receive, self-contain Root of Trust, supports firmware upgrade and can be easily configured for different high resolution uncompressed content.
HDCP 2.2 is WiFi certified Miracast solutions in production devices, protecting the link between Miracast devices. This IP solution is integrated with major Miracast/WiFi Display stacks.
We think that the security IP segment is just starting to grow, we may expect security IP to penetrate most of the connected applications. As an end user, I really hope security IP to become ubiquitous!
More about Synopsys security IP here
From Eric Esteve from IPNEST
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.