The never ending appetite for higher bandwidths, faster data interfaces and lower latencies are bringing about changes in how data is processed at data centers. The expansion of cloud to the network edge has introduced broad use of artificial intelligence (AI) techniques for extracting meaning from data. Cloud supercomputing has resulted in innovative data accelerators and compute architectures within data centers. At the same time, threats are coming from many directions and in many forms. The threat entry could be in the internet communications infrastructure in the form of DoS, BotNet, Ransomware, Spyware, etc. Or it could be via cloud API vulnerabilities and account hijacking. All these threats could be broadly classified into communications attacks, software attacks, invasive hardware attacks and non-invasive hardware attacks.
The combination of the above two trends has increased the need for enhanced data security and data privacy within data centers. The challenge data centers face is how to maintain data security without compromising on throughput and latencies. At the end of the day, it all comes down to enabling security at the chip/SoC level.
Dana Neustadter, Sr. Manager, Product Marketing for Security IP at Synopsys was responsible for presenting at IP-SoC Silicon Valley 2022 last month. Her presentation focused on challenges and ways of protecting data in motion and at rest at data centers. She discusses the trends that are driving heightened requirements and presents SoC solutions for ensuring security of various high-speed interfaces. This post is a synthesis of her presentation. You can download her presentation slides from here.
Requirements for Effective Security Solutions
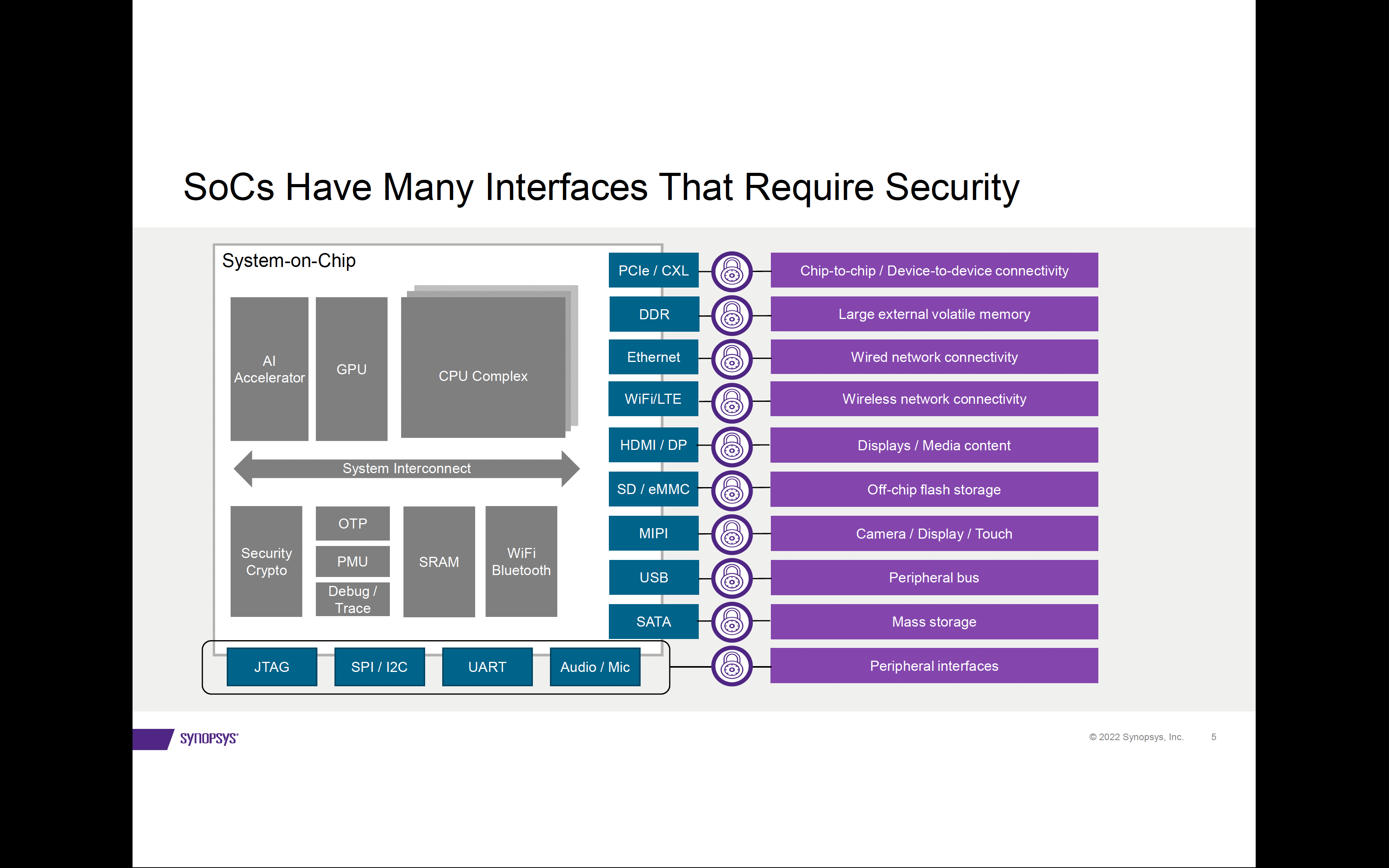
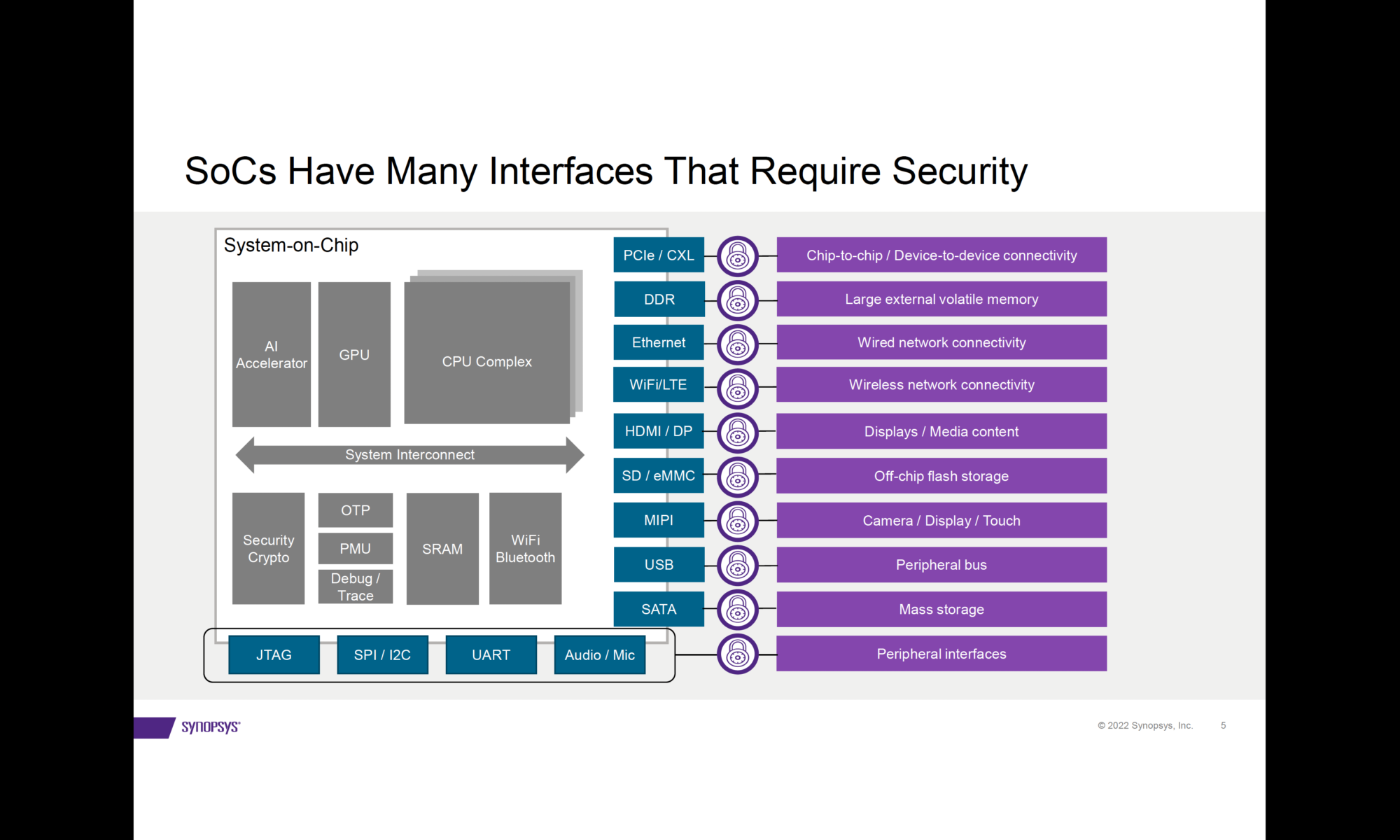
SoCs incorporate a number of different high-speed interfaces to move data between systems, memories, storage, and peripheral devices. Effective security mechanisms need to protect both data-in-motion as well as data-at-rest. This involves
- Authentication and Key Management for implementing
– Identification & Authentication
– Key generation
– Key distribution
– Control
- Integrity and Data Encryption between endpoints for ensuring
– Confidentiality
– Integrity
There are of course challenges when it comes to the implementation of these security mechanisms. How to add security on the data path while maintaining high throughput at low latencies? How to securely identify the data path endpoints without adding a large processing overhead? How to establish a trusted zone for managing and handling keys without adding to silicon area?
Key Aspects of Delivering Effective Security Solutions
There are upcoming standards for building trusted virtual machines at the application core/logic level for handling data paths from PCIe and CXL interfaces. These standards are being driven respectively by PCI-SIG and CXL Consortiums.
Meanwhile the areas of authentication and key management and integrity and data encryption are well defined and driven by existing standards.
- Authentication, attestation, measurement, and key exchange are implemented by the following standards.
-DMTF: Security protocol and Data Module (SPDM), Management Component Transport Protocol (MCTP)
-PCI-SIG: Component Measurement and Authentication (CMA), Data Object Exchange (DOE), Trusted Execution Environment I/O (TEE-I/O)
- The integrity and data encryption (IDE) component that addresses the confidentiality, integrity and replay protection is based on the AES-GCM crypto algorithm and is defined by PCIe 5.0/6.0 and CXL 2.0/3.0 standards.
Synopsys’ Security IP Offerings
Synopsys offers a comprehensive set of IP offerings to enable security against data tampering and physical attacks. The following chart shows an example data center networking SoC showing various Synopsys Security IP to secure the data.
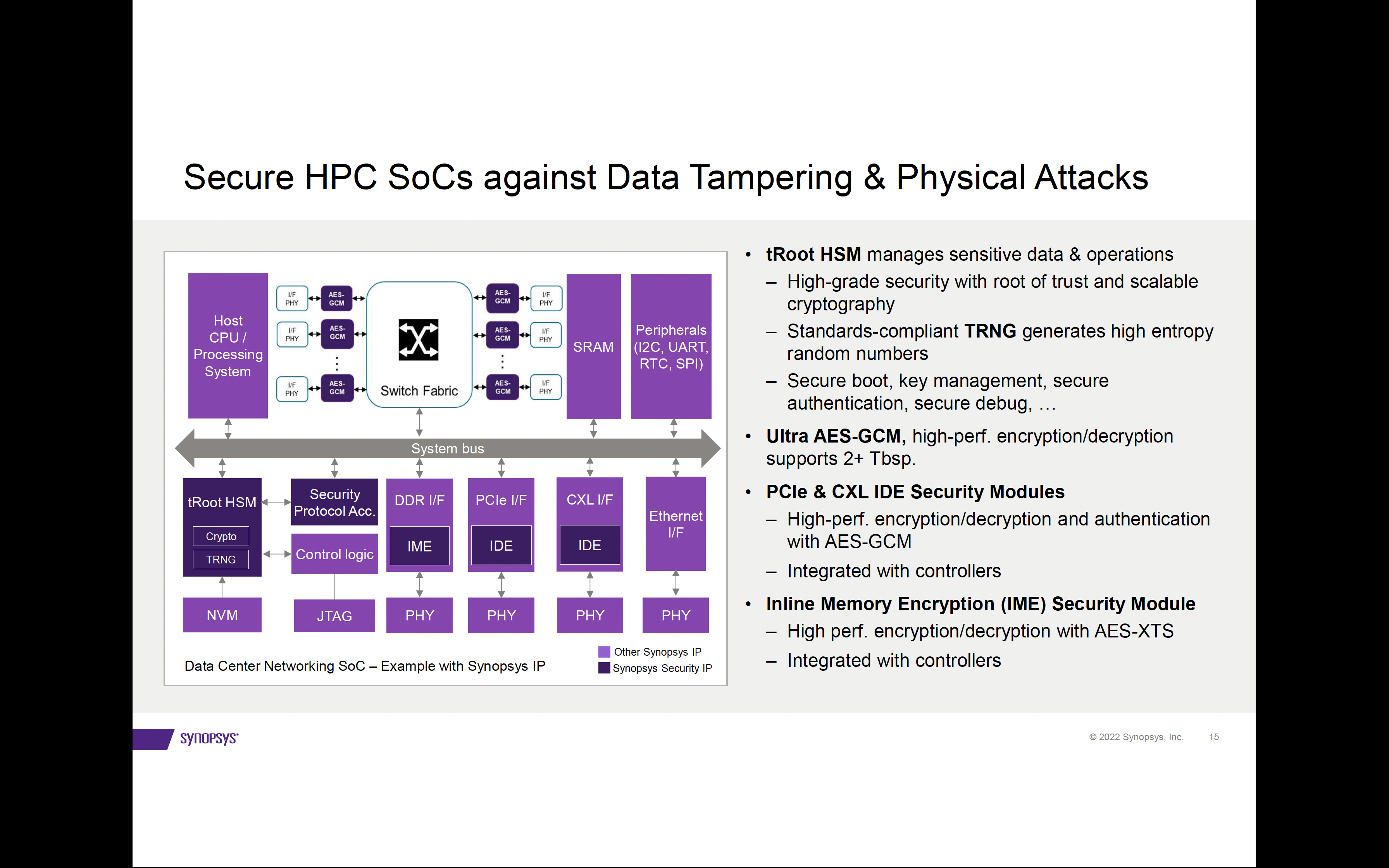
PCIe 5.0/ PCIe 6.0 IDE Security Modules
Integrity and Data Encryption (IDE) for PCIe is offered through a PCIe IDE Security Modules. There is a version available for PCIe 5.0 that supports all down speeds. And a separate version supporting the latest generation PCIe 6.0 and all down speeds. These modules work as plug-and-play with Synopsys PCIe controllers to match clock configurations, data bus widths, and lane configurations. The packet encryption, decryption and authentication are based on highly efficient AES-GCM crypto with very low latency. The modules are FIPS 140-3 certification ready.
CXL 2.0 IDE Security Module
As with the PCIe IDE security modules, the CXL security module is standards compliant and seamlessly integrates with Synopsys CXL controllers. All three protocols, CXL.io, CXL.cache, CXL.mem are supported, with latency as low as 0 cycles for .cache/.mem protocols in skid mode. This IP is also ready for FIPS 140-3 certification.
Inline Memory Encryption (IME) Security Module
This security module uses the AES-XTS algorithm with two sets of 128-bit or 256-bit keys, one for data encryption/decryption and another for tweak value calculation and is FIPS 140-3 certification ready. The memory encryption subsystem handles encryption, decryption, and management of tweaks and keys with very low latency. Other key features include full duplex support for read/write channels, efficient and protected key control and refresh, and a bypass mode.
Hardware Secure Module with Root of Trust
This security module provides a Trusted Execution Environment (TEE) to manage sensitive data and operations. It is the foundation for secure remote lifecycle management and service deployment. Key security features include a secure boot, secure authentication/debug and key management. Secure instruction and data controllers are included to provide external memory access protection and runtime tamper detection. Scalable cryptography options are available to accelerate encryption, authentication and public key operations.
Summary
Secure infrastructure is key to protecting data. Authentication and key management in the control plane and integrity and data encryption in the data plane are essential components of a complete security solution. Securing high-speed interfaces needs to be highly efficient with optimal latency. Synopsys provides complete solutions to secure SoCs, their data, and communications.
For more information, visit Synopsys Security Modules for Standard Interfaces
Also Read:
Bigger, Faster and Better AI: Synopsys NPUs
The Path Towards Automation of Analog Design
Design to Layout Collaboration Mixed Signal
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.