You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
WP_Term Object
(
[term_id] => 97
[name] => Security
[slug] => security
[term_group] => 0
[term_taxonomy_id] => 97
[taxonomy] => category
[description] =>
[parent] => 0
[count] => 335
[filter] => raw
[cat_ID] => 97
[category_count] => 335
[category_description] =>
[cat_name] => Security
[category_nicename] => security
[category_parent] => 0
[is_post] =>
)
Cryptocurrency fraud is aggressively on the rise and topped over $4 billion last year, according to the security tracking company Chainalysis.
This is especially shocking to those who thought they had found an incredible investment in the cryptocurrency world, yet were swindled out of everything. As part of these cryptocurrency… Read More
Cybersecurity will be hard pressed to take on the new challenges of bank managed digital currencies.
Banks are developing their own digital currencies. The introduction of Central Bank Digital Currencies (CBDC) is the beginning of an interesting trend that will change the cybersecurity dynamic for banking as it opens up an … Read More
The United States and allies’ national cyber response may soon be tested with the latest escalating conflict in the middle east. The U.S. conducted an airstrike that killed a revered Iranian general while in Iraq. This was in retaliation to a number of attacks against U.S. personnel and most recently the U.S. embassy in… Read More
It should be no surprise in the current climate that the US government is ramping up investment in microelectronics security, particularly with an eye on China and investments they are making in the same area. This has two major thrusts as I read it: to ensure trusted and assured microelectronics are being used in US defense systems… Read More
Seven major cryptocurrency exchanges were victimized in 2019, totaling over $160 million in financial theft. As predicted, cybercriminal hackers targeted crypto exchanges in 2019 and the trend will continue into 2020.
Crypto exchanges are relatively new, as compared to those in the traditional financial markets. It is
…
Read More
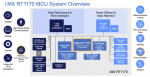
I first heard about NXP crossover MCUs at the 2017 TechCon. I got another update at this year’s TechCon, this time their progress on performance and capability in this family. They’ve been ramping performance – a lot – now to a gigahertz, based on a dual-core architecture, M7 and M4. They position this as between 2 and 9X faster than… Read More
On Wednesday, October 9, 2019, I had the pleasure of spending the day at ARM Techcon at the San Jose Convention Center. In the morning, in addition to getting some sneak peeks into the exhibitor area, I attended some of the morning keynote presentations, which focused on artificial intelligence (AI) and machine learning (ML) topics.… Read More
I mentioned some time ago (a DVCon or two ago) that Accellera had started working on a standard to quantify IP security. At the time I talked about some of the challenges in the task but nevertheless applauded the effort. You’ve got to start somewhere and some way to quantify this is better than none, as long as it doesn’t deliver misleading… Read More
Cybercriminals are luring in bitcoin holders with the promise of easy money if they become a mule to convert stolen assets into clean currency. The reality is these volunteers will just join the ranks of other victims. But that is not stopping people from joining up to replace other mules who have paid the price.
Criminals are selling… Read More
Drones attacked an oil processing facility last week and shut down half of all Saudi capacity, representing about 5% of the world’s daily oil production. We have seen how a botnet of compromised home appliances can take down a sizeable chunk of the internet, control structures of electricity and other critical infrastructures… Read More









Memory Matters: Signals from the 2025 NVM Survey