Part 2 examines the transformation of the interface protocols industry from a fragmented market of numerous specialized vendors to a more consolidated one dominated by a few major solutions providers as driven by the increasing complexity of modern protocols. It highlights the importance of rigorous validation of interface protocols and underscores the pivotal role of security in ensuring robust and reliable protocol design. It concludes by presenting an ideal roadmap for developing cutting-edge interface protocol solutions.
The Interface Protocol Landscape: Adoption, Security and Validation
Traditionally, interface protocols development followed a structured, sequential process that typically began with the formation of a consortium, followed by the creation of draft specifications. Once the specifications approached version 1.0, early adopters would begin implementation, and within a two-year timeframe, products would start to emerge.
Today, this timeline has been radically disrupted. Case in point, in early in 2024, Broadcom1 commented on their roadmap for switched for AI systems slated release in 2025, based on protocols that have not even seen the formation of a consortium. This represents a monumental shift, driven by market demands that far outpace the current capabilities of existing protocols. The pressure on the industry to keep up is unprecedented.
Evolving Approaches to Interface Protocol Adoption
The way protocols are adopted and verified has also undergone significant transformation. Designers are increasingly sourcing third-party IPs instead of building them in-house. For example, where designers previously developed PCI Gen4 protocols themselves, most now turn to external providers for PCI Gen6 solutions.
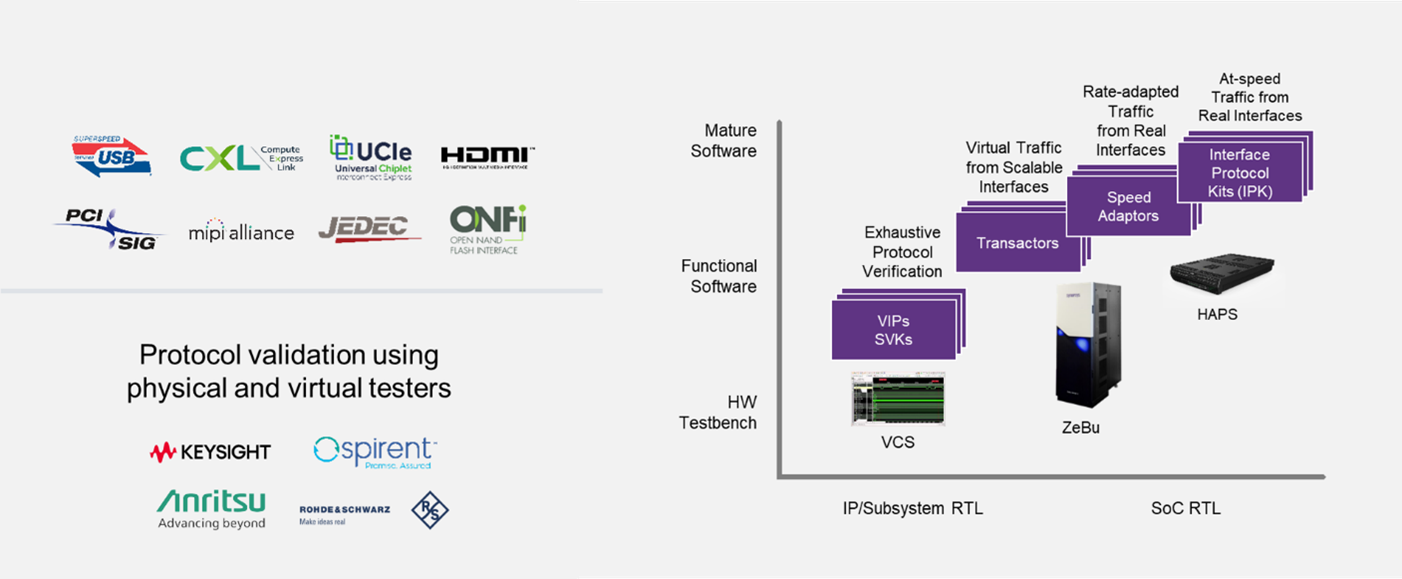
The adoption process itself has become much more streamlined. Historically, protocol implementation followed a prolonged step-by-step approach. Teams would start by using verification IP (VIP) of the required interface protocol for the functional verification in simulation, then evaluate its performance on emulation for few months, and eventually proceed to hardware implementation for prototyping or post-silicon testing. Now, all pre-silicon steps are compressed into a single quarter, reflecting the urgency and integration demanded by modern workflows.
In today’s project planning meetings, design teams expect a comprehensive roadmap from their IP providers right at the start of their interface protocol journey. Questions about VIP, virtual models in the form of transactors, and hardware implementations availability are no longer deferred—they arise simultaneously with the interface protocol decision. This shift marks a significant trend: designers are no longer solely focused on verifying protocols. Instead, they prioritize building a robust, fully integrated verification ecosystem centered around the interface. This approach ensures thorough validation while enabling a swift transition to software development, where real differentiation and value are created.
The Impact of Industry Consolidation
The interface protocol landscape is undergoing a paradigm shift. Market demands have accelerated the development timeline, compressing processes and driving designers to seek comprehensive, ready-to-integrate solutions. As a result, the industry is consolidating to meet these challenges. Supporting cutting-edge protocols requires immense expertise, resources, and investment—factors that only larger IP companies can consistently deliver.
Smaller IP vendors are finding it increasingly difficult to compete at the high end of the market. Many are merging, consolidating, or being acquired. While these smaller players may continue to find opportunities in mid-tier markets, high-end protocol development and support are rapidly becoming the domain of a few large, well-established companies.
The ability to adapt to this fast-evolving environment will determine who leads the future of protocol development and adoption.
Interface Protocol Security: Critical Imperative
In an increasingly interconnected world, security is essential to safeguarding data and systems against a wide array of threats. To achieve robust and reliable security, the foundation must begin at the hardware level, forming the bedrock of a comprehensive security framework.
The Layered Approach to Security
Security is best visualized as a series of interdependent layers, starting with a hardware root-of-trust and extending to encompass the system, application, software, and services. Hardware security serves as the cornerstone, providing a strong, reliable base to support and protect all subsequent layers. Any weakness in the security chain, regardless of where it occurs, can compromise the entire solution. Therefore, while hardware is the starting point, its design and implementation must be flawless to ensure the security of all operational phases.
The Hardware Root-of-Trust in SoC Designs
The hardware root-of-trust in System-on-Chip (SoC) designs represents a critical security mechanism built directly into the hardware. It establishes a trusted foundation for all secure operations within the system, enabling the verification of software integrity and safeguarding sensitive data. This embedded security ensures that the system can be trusted from the very beginning of its operation, acting as the first line of defense against potential breaches.
Security in Interface Protocols
In recent years, security considerations have become integral to interface protocol design. Modern interface protocols, including PCIe, CXL, UCIe, Display, and Memory, now feature comprehensive security hardware blocks embedded within their specifications encompassing the root-of-trust.
From the design perspective, the hardware root-of-trust is typically implemented as a Register Transfer Level (RTL) component. It integrates with the RTL describing the protocol controller, ensuring seamless operation and robust security. For example, the PCIe and CXL Protocols include security features such as Integrity and Data Encryption (IDE), designed to ensure data authenticity and confidentiality.
The hardware root-of-trust must undergo rigorous RTL-level verification and validation, similar to other hardware components.
Interface Protocol Verification and Validation
Modern interface protocols implement complex specifications with unique data integrity, throughput, latency and security requirements. For example:
- PCI Express (PCIe) demands high-bandwidth, low-latency communication for connecting GPUs and NVMe storage devices.
- Ethernet must ensure compliance with networking standards for interoperability.
- USB introduces complexities with hot-swapping and varying power requirements.
Each protocol requires rigorous validation to avoid costly errors in production silicon. Protocol malfunctions comprise a wide range of types from basic hardware failures that may lead to data corruption, deadlocks, reduced performance, etc., to design intent errors that may affect target specifications, rather challenging in post-silicon debug.
While hardware-description-language (HDL) simulation has traditionally been the cornerstone of SoC validation, providing high visibility into design behavior, it is increasingly limited by performance constraints. By running several orders of magnitude slower than real hardware it becomes impractical for validating the new generations of interface protocols.
These limitations necessitate a move towards vastly faster and extensively scalable validation solutions.
Hardware-Assisted Verification: The Optimal Approach.
Hardware-assisted verification platforms, including hardware emulators and FPGA prototypes, offer a compelling solution to address the challenges of SoC interface protocol validation. These platforms bridge the gap between pre-silicon and post-silicon validation, providing near-real-time performance with hardware accuracy unparalleled by software-based simulation. Key benefits include:
- Performance Acceleration: Emulation and prototyping platforms execute SoC designs orders of magnitude faster than HDL simulators, enabling comprehensive validation of high-speed protocols such as PCIe Gen 5 and Ethernet 400G by processing payloads of billions of verification cycles.
- Real-World Testing: Hardware-assisted platforms allow integration with real-world devices, providing a realistic environment for protocol validation.
- Early Bug Detection: By enabling early and iterative testing, hardware-assisted solutions help catch protocol violations and interoperability issues before they propagate into later stages of development.
- Scalability: These platforms can validate multiple protocols in the context of the entire SoC design, ensuring that complex interactions in heterogeneous SoCs are thoroughly tested.
Case Study: PCI Express Validation with Hardware-Assisted Platforms
For example, the validation of a PCIe Gen 5 interface in a modern SoC introduces challenges such as stringent signal integrity requirements and complex error recovery mechanisms. A hardware-assisted platform can simulate real-world scenarios, such as sudden link drops or varying traffic patterns, at full protocol speed. Debugging tools integrated into the platform can provide deep insights into packet-level transactions and protocol compliance, significantly accelerating the validation process.
Key considerations for a comprehensive interface protocol solution
Choosing the right partner for advanced interface protocols requires careful evaluation of several critical factors:
Active Participation in Industry Consortiums
The foundation of effective protocol development lies in active involvement with key industry consortiums. Leading providers play significant roles in these organizations, contributing to the creation and evolution of standards. Early participation—such as donating technology and collaborating closely with protocol developers—ensures that providers stay at the forefront of protocol formation and adoption. Leadership within these consortiums is a strong indicator of an innovative and forward-thinking IP provider.
Proven Performance: The Eye Diagram Speaks Volumes
Trust in a provider’s capabilities is built on a proven track record of silicon-verified IP. This requires thorough testing with industry-standard test equipment to ensure robust performance and reliability.
A critical benchmark is the eye diagram, which visually represents the ability of the IP to transmit data reliably at high speeds. Achieving a clean and well-measured eye diagram demonstrates superior analog performance and adherence to protocol standards. Beyond analog precision, a provider’s experience in implementing and verifying protocol functionality is crucial.
Leading vendors validate their designs through extensive testing, including numerous cycles of the digital controller and PHY test chips on prototyping systems, ensuring the interface operates seamlessly.
Verification Support Across the Lifecycle
Success in protocol development extends beyond design to encompass leadership in design verification, validation, certification, and compliance testing. High-quality solutions require robust support across the development lifecycle, from virtualization and simulation-based verification to hardware-accelerated testing with components such as transactors and speed adapters.
Advanced customers increasingly demand comprehensive verification ecosystems as part of the IP package. These solutions are no longer optional add-ons but integral components of the chip design process. Advanced verification solutions require large, specialized teams—resources that not all suppliers can provide.
Examples of Advanced Verification Solutions
- SoC Verification Kit (SVK), a ready-to-use package combining IP and VIP (Verification IP). It streamlines IP integration into SoC testbenches, reducing setup time and allowing design teams to focus on differentiation. Surveys show that teams spend up to 20% of verification cycles on initial setup and sanity testing. Often, IP design and validation teams work in silos, leading to duplicated effort and limited reuse of components. This inefficiency can consume approximately three person-months per IP, a considerable cost given the multiple complex IPs in modern systems. A state-of-the-art SVK can cut setup time by at least 50%, significantly accelerating time-to-market while reducing costs.
- IP Verification Kit (IPK), a package combining an FPGA prototype of the interface IP with a PHY interface card ready-to-use in system environments. It validates the interoperability of the IP with the rest of the SoC, ensuring it performs as intended in a real-world system prototype.
Summary
Design teams face the dual challenge of achieving differentiation in competitive, accelerated design cycles while pushing beyond the limits of existing interface standards. To meet these demands, they must partner with suppliers capable of aligning the development of advanced interface IP and verification solutions with project timelines.
Taking a holistic approach to verification is essential for maintaining SoC schedules and ensuring product success. Advanced tools like SVKs and IPKs provide measurable efficiency gains, helping teams reduce costs, accelerate time-to-market, and focus on innovation rather than repetitive verification tasks.
References
Also Read:
The Journey of Interface Protocols: The Evolution of Interface Protocols – Part 1 of 2
Share this post via:






TSMC Process Simplification for Advanced Nodes