Overview
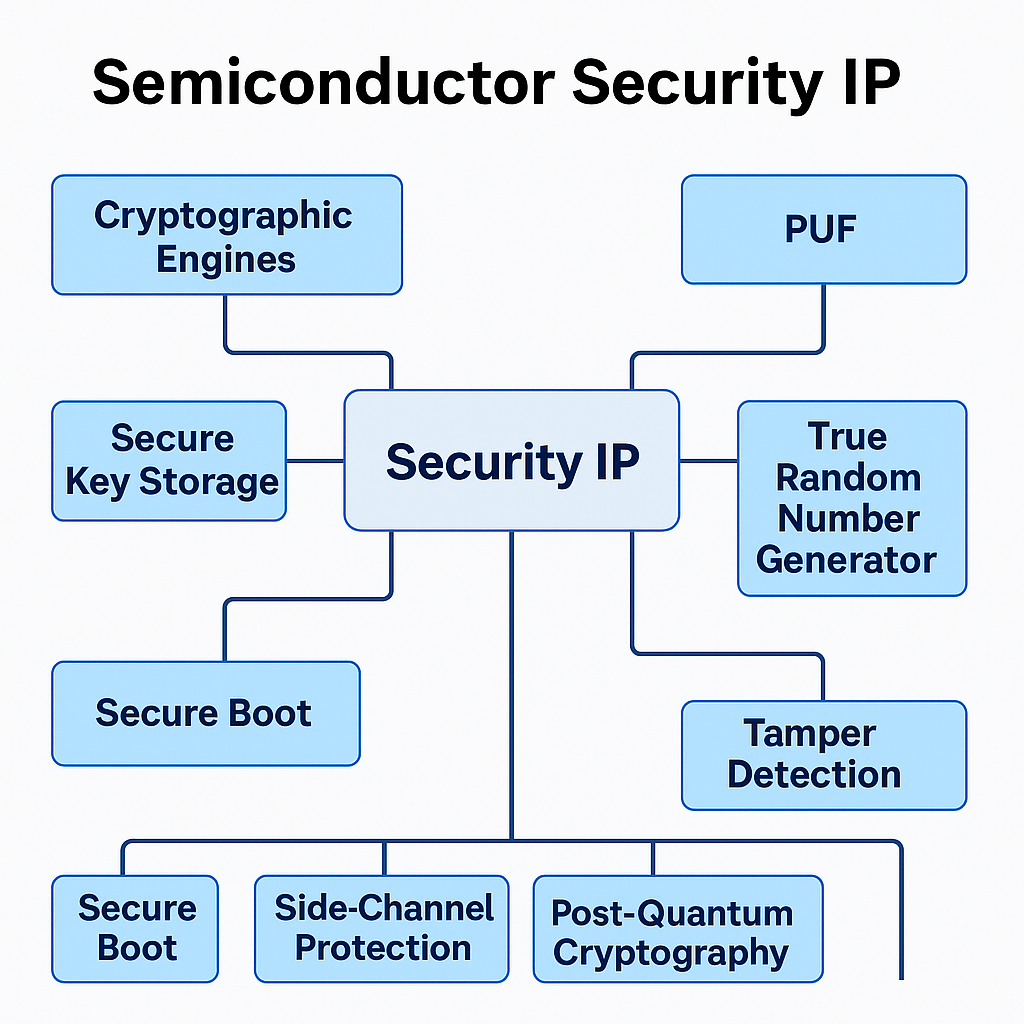
Semiconductor Security IP consists of hardware-based intellectual property blocks designed to protect chips and systems against unauthorized access, tampering, counterfeiting, side-channel attacks, and data breaches. These IPs are embedded into SoCs, ASICs, FPGAs, and secure microcontrollers to provide robust, low-power, and low-latency security features.
Security IP plays a vital role in sectors like automotive, mobile, defense, IoT, data centers, and finance, where hardware trust, confidentiality, and integrity are paramount.
🔐 Categories of Security IP
| Type | Function | Examples |
|---|---|---|
| Cryptographic Engines | Perform symmetric/asymmetric encryption and hashing | AES, SHA, RSA, ECC |
| True Random Number Generators (TRNGs) | Generate unpredictable values for cryptographic use | Thermal noise-based, jitter-based |
| PUF (Physically Unclonable Functions) | Silicon fingerprint for unique ID generation | SRAM PUF, RO PUF |
| Secure Boot | Validates firmware before execution | ROM-based roots of trust |
| Secure Key Storage | Isolates and encrypts keys within chip memory | E-fuse, OTP, battery-backed RAM |
| Side-Channel Attack Protection | Mitigates power/EM leakages | Differential Power Analysis (DPA) countermeasures |
| Tamper Detection IP | Detects voltage, frequency, or physical probing attacks | Active mesh, glitch detectors |
| Post-Quantum Cryptography IP | Quantum-resistant algorithms | Lattice-based, hash-based digital signatures |
| Secure Debug & JTAG Access | Prevents unauthorized device access during development | Lock/unlock sequences, challenge-response |
| Secure Element (SE) | Isolated processor/storage for payment, identity | Used in eSIM, biometric chips |
🧠 Key Functions
-
Authentication: Ensures that devices or users are genuine.
-
Confidentiality: Prevents data exposure through strong encryption.
-
Integrity: Detects unauthorized data tampering.
-
Non-repudiation: Guarantees that a transaction was performed and logged.
-
Secure Lifecycle Management: Supports provisioning, personalization, and revocation.
🏭 Major Security IP Vendors
| Vendor | Specialties |
|---|---|
| Rambus | Crypto cores, DPA-resistant IP, secure root-of-trust |
| Secure-IC | Embedded security subsystems, PUF, tamper detection |
| PQShield | Post-quantum cryptography IP cores |
| CryptoNext Security | Quantum-safe algorithms |
| eMemory / PUFsecurity | PUF-based hardware root-of-trust |
| Synopsys DesignWare | Security IP for SoCs and embedded devices |
| Cadence (Tensilica LX/Security Extensions) | Secure DSP and controller IP |
| Siemens EDA (Tessent Embedded Analytics) | Security monitors and access control |
| Imagination Technologies | Secure processing cores for GPU and AI workloads |
🔎 Use Cases by Industry
| Sector | Application |
|---|---|
| Automotive | Secure boot, OTA updates, EV charging, ADAS |
| IoT / Edge | Device identity, mutual authentication, encrypted data |
| Mobile | Trusted execution environments, fingerprint/biometric data protection |
| Data Centers | Hardware root of trust, encrypted storage, TPM functionality |
| Finance / eID | Secure elements in payment terminals, smart cards |
| Defense / Aerospace | Anti-tamper, secure communications, controlled access |
🧪 Certification & Compliance
| Standard | Purpose |
|---|---|
| FIPS 140-3 | Cryptographic module validation (NIST) |
| Common Criteria (EAL levels) | Secure system evaluations (ISO 15408) |
| SESIP / PSA Certified | Security assurance for IoT chips |
| ISO/SAE 21434 | Automotive cybersecurity |
| NIST PQC Standards | Post-quantum cryptography compliance |
Many security IP vendors offer certified or certifiable IP cores with extensive documentation and test vectors.
📈 Emerging Trends
| Trend | Description |
|---|---|
| Post-Quantum Cryptography (PQC) | IP cores implementing lattice-based cryptography (e.g., Kyber, Dilithium) |
| AI + Security | Integration of anomaly detection and adaptive cryptographic tuning |
| Secure Chiplets | Isolated security IP in chiplet designs (UCIe-compliant) |
| Zero Trust Architectures | Hardware-based enforcement of continuous authentication |
| Secure Boot in Open-Source Hardware | Growing need for trusted execution in RISC-V and FPGA platforms |
🛠️ Design Considerations
-
Side-channel resistance: Design techniques such as masking, dual-rail logic
-
Latency: Must support high-speed encryption (e.g., real-time video streaming)
-
Power: Optimized for low-energy edge and wearable devices
-
Area footprint: Scalable from microcontrollers to high-end SoCs
-
Lifecycle management: Secure provisioning and revocation post-silicon
🧬 Security IP Lifecycle
-
Design – Embedded during RTL stage or integrated as hard IP
-
Verification – Crypto validation, fault injection, formal proof
-
Provisioning – Keys and fuses written at test or post-fab
-
Operation – In-field secure execution, crypto ops
-
Revocation / Update – Key destruction, firmware update with anti-rollback













Advancing Automotive Memory: Development of an 8nm 128Mb Embedded STT-MRAM with Sub-ppm Reliability