You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
Jasper Goes to DVConby Paul McLellan on 02-02-2014 at 6:00 pmCategories: EDA
As usual, since they are firmly in the verification space, Jasper will have a number of things going on at DVCon 2014 which is March 3-6th at the Doubletree in San Jose. In the exhibition hall they are at booth #402.
Jasper will be happy to talk to you about anything, I’m sure, but the focus this year is on the JasperGold Security… Read More
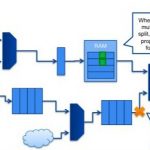
At the Jasper Users Group meeting in October Rajeev Ranjan presented on the JasperGold COV App which he described as the Swiss army knife for verification. It comes in many sizes and contains many useful tools.
The primary goal of COV is to provide coverage metrics:
- stimuli coverage: how restrictive is the design behavior under
…
Read More
Formal approaches and security are a perfect match since you really want to prove that there are no holes in your security, rather than just being fairly confident. At the recent Jasper User Group meeting, Victor Purri presented some case studies in security verification.
The Jasper Security Path Verification (SPV) App is used… Read More
At the Jasper Users’ Group, Alex Netterville of ARM presented about how ARM are using formal on an unannounced processor code-named Pelican. Don’t read the presentation trying to find out information about Pelican itself, there isn’t any. That wasn’t the topic. Alex has been using formal approaches… Read More
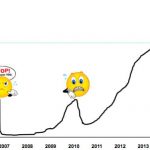
2.5x ROI vs simulation. 25% of bugs found for only 10% of the overall verification cost. 36% of bugs in a current CPU project. These impressive results for formal analysis are what ARM’s Laurent Arditi reported at JUG 2013 after painstaking recording of metrics over several production programs.
As you can see from the above graph,… Read More
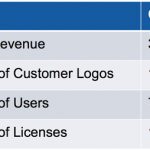
At the Jasper Users’ Group meeting, Kathryn presented the state of Jasper. The numbers are impressive. The company has grown at a CAGR of over 35% since 2007, which is 6 times faster than EDA as a whole. They have been profitable at 15-20% EBITDA for 14 consecutive quarters.
Jasper is focused on engaging deeply with a small number… Read More
When new restaurants open they sometimes have what is called a ‘soft opening’ where they open a few days earlier than the official opening night. They are less busy since nobody knows they are open yet, maybe the whole menu isn’t available and expectations may be lower. Of course, Broadway productions also often… Read More
Jasper: Negronis on tapby Paul McLellan on 08-22-2013 at 6:26 pmCategories: EDA
Did you know that Jasper’s Corner Tap in San Francisco serves Negronis on tap? It’s true. They also have Hanky Panky on tap, which is a Negroni with the Campari replaced with Fernet (which everyone pronounces as Frenet despite it being…well…wrong). And here’s another thing you probably didn’t… Read More
Well, Sweden is not noted for its carnivals, Brazil is not noted for it’s tall blonde blue-eyed women, Sweden’s climate is not great for growing sugar cane and Brazil’s isn’t great for reindeer. Both countries speak languages with odd-sounding vowels but they are not the same language. But, ding, Jasper… Read More
Kathryn Kranen, CEO of Jasper Design Automation, got to give her view of the future of EDA on the Thursday of DAC. For many years she has been on the EDAC board and is currently chair. When she first was on the board she talked to many of the stakeholders in the EDA ecosystem: EDA companies, IP companies, semiconductor companies, academics,… Read More