Anybody who’s ever read the iconic MAD magazine would be familiar with the wordless Spy vs Spy cartoon. First published in January, 1961, it features two agents involved in stereotypical and comical espionage activities. One is dressed in white, and the other in black, but they are otherwise identical. A parody of the political… Read More
Tag: cybersecurity
IoT Devices Can Kill and What Chip Makers Need to Do Now
After the onslaught of IoT devices Christmas brought to the masses we really need to talk about security or lack thereof. Do me a favor and count how many IoT devices you have now? Our house IoT count is probably a bit higher than average due to my technology addiction but we are firmly in the double digits and the security breach stories… Read More
Auto Cyber Security: From Ignorance to Compliance
Auto makers have long relied on security by obscurity to get away with not defining or adhering to proper cyber security hygiene. This rationalization had been embraced in the context of low levels of automotive hacking mainly carried out by enthusiasts or so-called “white hat” or ethical hackers.
A new report from Strategy Analytics,… Read More
When the Wrong Person Leads Cybersecurity
Succeeding at managing cybersecurity risks is tremendously difficult even for seasoned professionals. To make situations worse, poorly suited people are often chosen to lead security organizations, bringing about disastrous results. This has contributed to weaker risk postures for organizations and the rapid turnover… Read More
Technology Transformation for 2019
Digital technology continues to connect and enrich the lives of people all over the globe and is transforming the tools of everyday life, but there are risks accompanying the tremendous benefits. Entire markets are committed and reliant on digital tools. The entertainment, communications, socialization, and many others sectors… Read More
Connected Cars High Tech Low Demand
The latest reliability report from Consumer Reports which dumped on domestics and rained glory upon Asian imports highlighted a conundrum facing car makers. The more effort car makers put into innovation, the greater the risk of consumer confusion, system failure and lousy reliability scores.
The picture is even worse if one… Read More
ARM TechCon 2018 is Upon Us!
ARM TechCon is one of the most influential conferences in the semiconductor ecosystem without a doubt. This year ARM TechCon has moved from the Santa Clara Convention Center to the much larger convention center in San Jose. Last year the conference seemed to be busting at the seams so this move makes complete sense. A little less … Read More
Data Breach Laws 0-to-50 States in 16 Years
It has taken the U.S. 16 years to enact Data Breach laws in each state. California led the way, with the first, in 2002 to protect its citizens. Last in line was Alabama, which just signed their law in March 2018. There is no overarching consistent data breach law at the federal level. It is all handled independently by each state. This… Read More
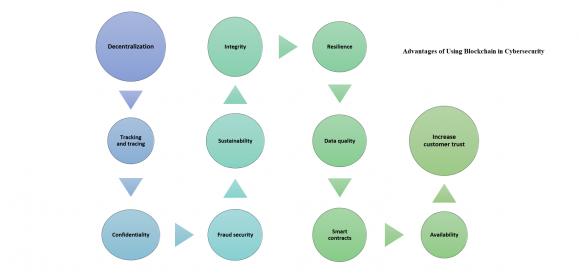
Second Line of Defense for Cybersecurity: Blockchain
In the first part we covered AI as the first line of defense for cybersecurity, the goal was to keep the cyber-criminals at bay, but in case they managed to get-in and infiltrate the network we need to initiate the second line of defense; #Blockchain. With the fact that cybercrime and cyber security attacks hardly seem to be out of the… Read More
First Line of Defense for Cybersecurity: AI
The year 2017 wasn’t a great year for cyber-security; we saw a large number of high-profile cyber attacks; including Uber, Deloitte, Equifax and the now infamous WannaCry ransomware attack, and 2018 started with a bang too with the hackingof Winter Olympics. The frightening truth about increasingly cyber-attacks is … Read More