You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
Secure-IC at DAC 2025: Building Trust into Tomorrow’s Chips and Systems
As semiconductor innovation accelerates, the chiplet-based design paradigm is redefining the landscape of advanced electronic systems. At DAC 2025, Secure-IC (booth #1208) will present a comprehensive suite of technologies engineered to address the… Read More
Dan is joined by Michele Sartori – senior product manager at PQShield. Michele is a software engineer in Computer and Network Security, specializing in product management. He is a passionate tech team leader at the forefront of emerging technologies focused on achieving tangible results.
In this highly informative discussion,… Read More
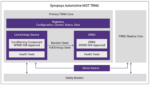
The security of a device or system depends mainly on being unable to infer or guess an alphanumeric code needed to gain access to it or its data, be that a password or an encryption key. In automotive applications, the security requirement goes one step further – an attacker may not gain access per se, but if they can compromise vehicle… Read More
Dr Ali El Kaafarani is the founder and CEO of PQShield, a British cybersecurity startup specialising in quantum-secure solutions. A University of Oxford spin-out, PQShield is pioneering the commercial roll-out of a new generation of cryptography that’s fit for the quantum challenge, yet integrates with companies’ legacy
…
Read More
There is never a dearth of new terms, discoveries and inventions in the technological world. And sometimes existing terms get reinvigorated. And debates ensue. The debaters argue about the plusses and minuses and make some predictions. Such is the case with “Quantum Computing.” I recently watched and listened to a webinar that… Read More
Cryptocurrency fraud is aggressively on the rise and topped over $4 billion last year, according to the security tracking company Chainalysis.
This is especially shocking to those who thought they had found an incredible investment in the cryptocurrency world, yet were swindled out of everything. As part of these cryptocurrency… Read More
Anybody who’s ever read the iconic MAD magazine would be familiar with the wordless Spy vs Spy cartoon. First published in January, 1961, it features two agents involved in stereotypical and comical espionage activities. One is dressed in white, and the other in black, but they are otherwise identical. A parody of the political… Read More
No doubt many who read this article have heard the expression “You can’t get there from here…” It’s most often attributed to New Englanders – primarily residents of Maine – to describe a route to a destination that is so circuitous and complex that one needn’t bother embarking on the journey.
In the context of the business world, the… Read More
I read with interest the US Chamber of Commerce’s assessment of the Made in China (MIC) 2025 plan to transform the world’s most populous nation into an Advanced Manufacturing leader. MIC 2025 covers 10 strategic industries that China identifies as critical to economic growth in the 21[SUP]st[/SUP] century, including next-gen… Read More
Things are going quite well in the Valley, ESPECIALLY if traffic is any indication. I still remember the BUST with the empty office buildings and light traffic, back in the early 2000’s…while I wish for traffic like that always, I certainly prefer the busy times, guess you cannot have it all. The more traffic, the more jobs; they invariably… Read More