Bluetooth has always been a popular communication protocol for short-range applications, but now anticipating BT5 it’s really moving into the big leagues as a significant option for IoT applications. The new standard combines ultra-low power with significantly higher range and higher performance. Ultra-low power is always… Read More
Tag: bernard murphy
This Apple Fell a Little Further from the Tree
Some companies are famously, even obsessively secretive about internal development. We never get to see discussion of areas they are working on (other than through patent filings) – we only see the polished and released product/service. Amazon is one such company but Apple must rank for many of us as the pre-eminent company in … Read More
Who Left the Lights On?
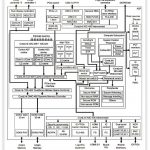
I attended a Mentor verification seminar earlier in the year at which Russ Klein presented a fascinating story about a real customer challenge in debugging a power problem in a design around an ARM cluster. Here’s the story in Russ’ own words. If you’re allergic to marketing stories, read it anyway. You might… Read More
Crowd-Sourcing Morality for Autonomous Cars
Questions are being raised on how autonomous vehicles should react in life-or-death situations. Most of these have been based on thought experiments, constructed from standard dilemmas in ethics such as what should happen if the driver of a car or an autonomous car is faced with either killing two pedestrians or killing the occupants… Read More
AI vs AI
You might think that one special advantage of AI systems is that they should be immune to attacks. After all, their methods are so complex and/or opaque that even we can’t understand how they work, so what hope would a hacker have in challenging these systems? But you would be mistaken. There’s nothing hackers like better than a challenge.… Read More
The Other Half of AI
I touched earlier on challenges that can appear in AI systems which operate as black-boxes, particularly in deep learning systems. Problems are limited when applied to simple recognition tasks, e.g. recognizing a speed limit posted on a sign. In these cases, the recognition task is (from a human viewpoint) simply choosing from… Read More
Renewable Energy is On a Roll
Since everything we build in this industry either runs on, stores or produces electricity, we should have a more than passing interest in how we get that power. A couple of organizations, confusingly named the IEA (International Energy Agency) and the EIA (Energy Information Administration – a US agency) provide lots of interesting… Read More
Building a Virtual Prototype
I wrote recently about how virtual prototypes (in the form of VDKs) can help embedded software teams practice continuous integration. Synopsys has just released a white paper detailing a practical approach to building a VDK, using the Juno ARM development platform (ADP) to illustrate. Just as a reminder, the point of a virtual… Read More
Enter the Cellular IoT
You could be forgiven for thinking that wireless in an IoT device must be Bluetooth-5 or Zigbee or Thread. After all, that’s what ARM has introduced as a part of their IoT solution and they have market weight that is difficult to dismiss. However those options aren’t the only game in town. There is already some level of (second… Read More
An End of Year View of Semi Consolidation
The last couple of years have been tumultuous for the semiconductor market. IC Insights just released a report showing just how much consolidation has concentrated market strength in a small number of companies. The report (which excludes fabs) shows that the 5 top companies – Intel, Samsung, Qualcomm, Broadcom and SK Hynix – … Read More