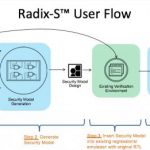
Hardware Roots of Trust (HRoTs) have become a popular mechanism to provide a foundational level of security in a cell-phone or IoT device or indeed any device that might appear to a hacker to be a juicy target. The concept is simple. In order to offer credible levels of security, any level in the stack has to be able to trust that levels… Read More
Tag: assertions
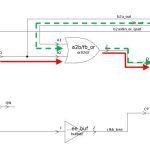
Up front phases improve CDC analysis
Many tools find clock domain crossings (CDCs) in FPGA designs. Some don’t find the right ones since they don’t comprehend things like in-house synchronizer constructs. Some find too many based on misunderstanding intent, inaccurate constraints, and other factors that lead to noise.… Read More
Michael Sanie Plays the Synopsys Verification Variations
I met Michael Sanie last week. He is in charge of verification marketing at Synopsys. I know him well since he worked for me at both VLSI Technology and Cadence. In fact his first job out of college was to take over support of VLSIextract (our circuit extractor), which I had written. But we are getting ahead.
Michael was born in Iran and… Read More
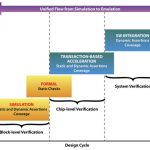
Assertions verifying blocks to systems at Broadcom
Speaking from experience, it is very difficult to get an OEM customer to talk about how they actually use standards and vendor products. A new white paper co-authored by Broadcom lends insight into how a variety of technologies combine in a flow from IP block simulation verification with assertions to complete SoC emulation with… Read More
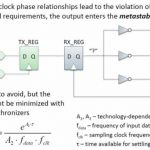
The never-ending quest to kill metastability
The difficulty of an engineering problem can be gauged by two things:
1) The number of attempts to generate a solution.
2) The degree of hyperbole used to describe the effectiveness of the latest solution.
The problem many folks in the EDA industry are after right now is clock domain crossings (CDCs) and the resulting metastability… Read More