Back in the day we had processors which consolidated computing power onto a chip, and out of these sprang (if you’ll excuse the Biblical imagery) microcontrollers (MCUs) in one direction and increasingly complex system-on-chip (SoC) processors in another direction. SoCs are used everywhere today, in smartphones, many IoT … Read More
CEVA and Local AI Smarts
When we first started talking about “smart”, as in smart cars, smart homes, smart cities and the like, our usage of “smart” was arguably over-generous. What we really meant was that these aspects of our daily lives were becoming more computerized and connected. Not to say those directions weren’t useful and exciting, but we weren’t… Read More
Protecting electronics around the world, SEMI insights
SEMI is a worldwide organization with local chapters like the one here in Oregon, where I attended a recent half-day presentation by several industry experts on the topic – Globalization, How it shapes the Semiconductor industry:
- Michael Chen, Director, Mentor – A Siemens Business
- John Brewer, CEO, Amorphyx
- Ed
Cybersecurity is (not only) about Technology
One of the biggest misconceptions is thinking cybersecurity is only about technology. When in fact, people and their behaviors, play a prominent role in almost every aspect of protecting digital assets. Without proper consideration for the human element, security strategies are destined to fail miserably.
In this Week’s Video… Read More
ARM Security Update for the IoT
Despite all the enthusiastic discussion about security in the IoT and a healthy market in providers of solutions for the same, it is difficult to believe that we are doing more than falling further behind an accelerating problem. Simon Segars echoed this in his keynote speech at ARM TechCon this year. The issue may not be so much in… Read More
Arm 2017 TechCon Keynote Simon Segar!
Now that the dust has settled with the Softbank acquisition I must say that Arm is truly a different company. There are now a lot of new faces from outside the semiconductor industry, which is a good thing, and a lot less stress from Wall Street which is an even better thing. Simon can now wear whatever he wants without the worry of lowering… Read More
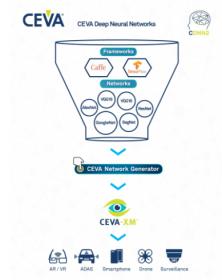
DSP-Based Neural Nets
You may be under the impression that anything to do with neural nets necessarily runs on a GPU. After all, NVIDIA dominates a lot of what we hear in this area, and rightly so. In neural net training, their solutions are well established. However, GPUs tend to consume a lot of power and are not necessarily optimal in inference performance… Read More
IoT Security Hardware Accelerators Go to the Edge
Last month I did an article about Intrinsix and their Ultra-Low Power Security IP for the Internet-of-Things (IoT). As a follow up to that article, I was told by one of my colleagues that the article didn’t make sense to him. The sticking point for him, and perhaps others (and that’s why I’m writing this article) is that he couldn’t … Read More
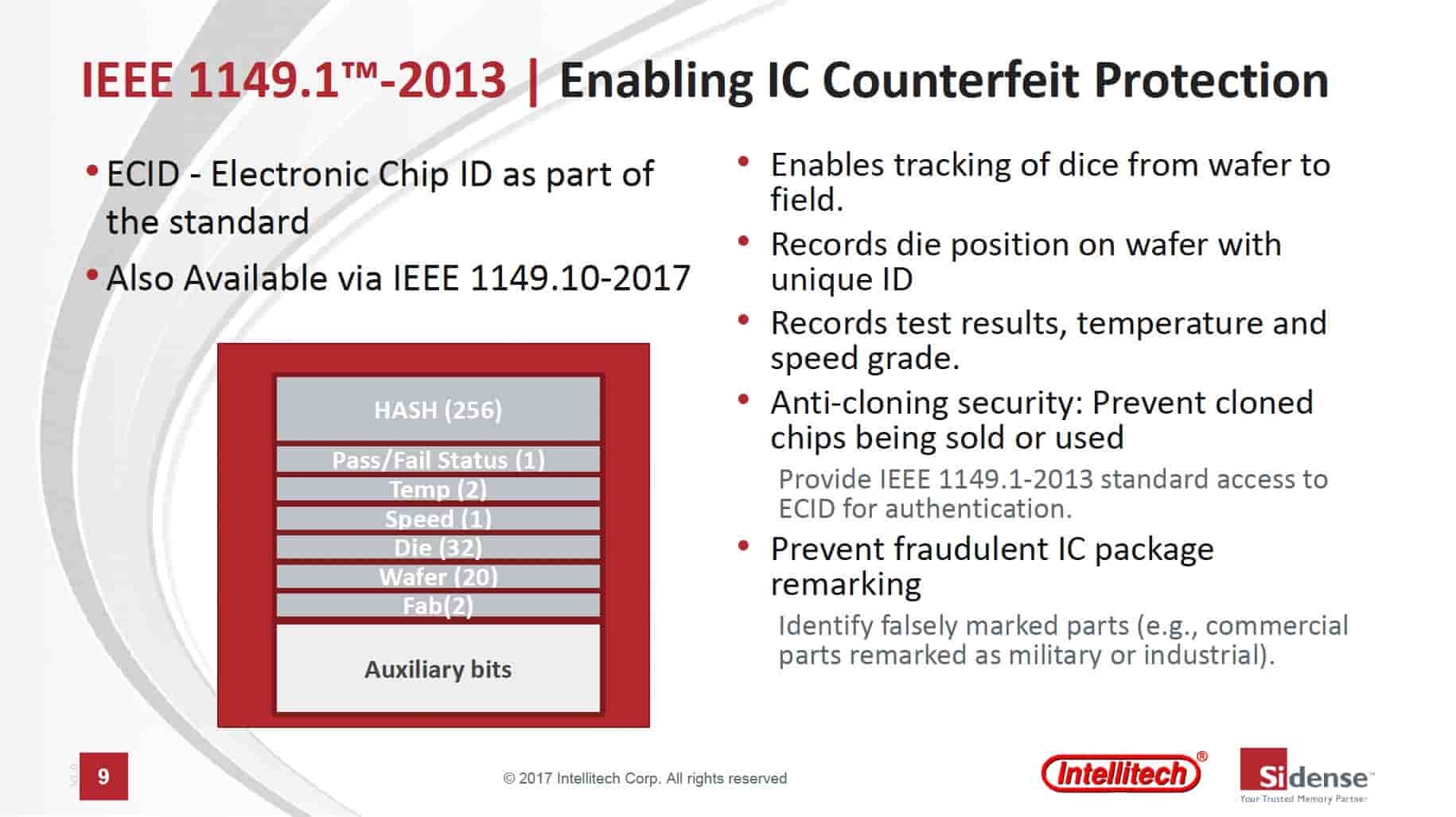
Implementing IEEE 1149.1-2013 to solve IC counterfeiting, security and quality issues
As chips for any design are fabricated, it turns out that no two are the exactly the same. This is both a blessing and a curse. Current silicon fabrication technology is amazingly good at controlling factors that affect chip to chip uniformity. Nevertheless, each chip has different characteristics. The most extreme case of happens… Read More
An IIot Gateway to the Cloud
A piece of learning we all seem to have gained from practical considerations of IoT infrastructure is that no, it doesn’t make sense to ship all the data from an IoT edge device to the cloud and let the cloud do all the computational heavy lifting. On the face of it that idea seemed good – all those edge devices could be super cheap (silicon… Read More









A Detailed History of Samsung Semiconductor