By Dina Medhat
Three key takeaways
- 3D ICs require fundamentally new ESD verification strategies. Traditional 2D approaches cannot address the complexity and unique connections in stacked-die architectures.
- Classifying external and internal IOs is essential for robust and cost-efficient ESD protection. Proper differentiation enables optimized protection schemes, area savings, and reliable performance.
- Industry-proven automation tools, like Calibre 3DPERC, are essential to meet evolving ESD verification needs in heterogeneous 3D designs.
Why is ESD verification critical for 3D IC designs?
Electrostatic discharge (ESD) remains one of the most persistent threats to integrated circuits at every step of the lifecycle—from manufacturing through operation. ESD events release a sudden surge of electrical current, which can melt metal, break down junctions, or destroy oxides, leading to costly failures. Effective ESD protection is therefore not just good practice—it is essential for reliability and product lifetime.
How do ESD protection circuits prevent damage?
Successful ESD protection hinges on choosing robust circuit architectures and ensuring that physical implementation matches the design intent. IC designers introduce specific ESD protection schemes at both the schematic and layout stages. Before manufacturing, ESD protection rules are verified to confirm enough safeguards are in place—addressing topology requirements and confirming that interconnects can handle ESD events. Verification at this stage is fundamental to design reliability.
What’s different about ESD protection in 3D ICs?
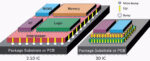
3D integration is revolutionizing IC design. In 2.5D architectures, dies sit side-by-side atop a silicon interposer. Micro-bumps (or Hybrid-bumps) connect each die to the interposer, and flip-chip bumps connect the interposer to the ball grid array (BGA) substrate. Full 3D integration stacks dies on top of each other, linked by through-silicon vias (TSVs). Designers often mix technologies and process nodes across dies, leveraging different vendor solutions for interposers, packaging and fabrication. Each integration method introduces unique benefits along with specific ESD challenges. Figure 1 demonstrates the main difference between 2.5D integration and 3D integration.
Why 3D ESD verification is more complex than 2D and 2.5D
Traditional 2D ESD verification considers all chip pads as interfaces to the outside world, and these demand robust protection against ESD events. In 3D designs, however, many pads serve only as internal die-to-die connections, not external IO interfaces (figure 2). This distinction is crucial:
- External IOs face ESD events from package pins and require comprehensive protection.
- Internal IOs are far less exposed and can use smaller, more efficient ESD devices—saving area and cost.
External IOs are connected to the package pins and face more ESD events than internal IOs. Similar to 2D designs, external IOs are affected by both human body model (HBM) and charged device model (CDM) ESD events. However, internal IOs are affected by far fewer HBM and CDM events. This difference means internal IOs can use smaller ESD protection circuits, which in turn translates into significant savings in die area and cost without sacrificing overall ESD protection robustness.
Furthermore, in 3D ICs, protection needs to be evaluated at the system level—not on a die-by-die basis. This opens the door for exploring the minimum ESD protection needed to avoid the failure of the final 3D product. ESD devices can span multiple dies or reside on a die with a different process node than the signal they protect. Complex connection topologies mean that power clamps, resistors and other ESD components may be shared, increasing verification complexity. There are many ways to optimize your preferred ESD methodology to reduce the final cost for manufacturing the 3D design, but at the cost of ESD verification complexity. Add the challenge of integrating multiple process nodes and vendors, and verification must become architecture-driven, not just foundry-specific.
So to summarize some of the key challenges for 3D ESD verification:
- Differentiating between ESD protection for external IOs versus internal IOs
- Handling CDM and HBM constraints for die-to-die connections
- Determining the minimum ESD protection needed to avoid failure of the final 3D IC product
- Accounting for different technology nodes / foundries for the dies & handling interfaces
- Determining how to source from multiple vendors and ensure consistent ESD protection
- Dealing with different ESD design methodologies
Automating ESD verification for 3D IC designs
Modern ESD verification tools, such as Calibre 3DPERC, address these new challenges head-on The recommended workflow combines die-level and assembly-level analysis. Using Calibre PERC, designers first verify the ESD robustness of each die and interposer. Calibre 3DPERC then performs system-level checks, identifying point-to-point (P2P), topology and geometrical violations across the assembled stack. This robust approach ensures that ESD reliability is maintained throughout heterogeneous 3D architectures (figure 3).
The bottom line on ESD verification for 3D IC
ESD protection is an essential element in IC design. 2D ESD verification is well-established, 3D architectures require a new mindset and advanced IP to address evolving threats. ESD devices can span multiple dies and need to be combined for correct evaluation. IO type (external vs internal) have different ESD requirements. Moreover, mixing different tech nodes from different foundries contributes to the 3D ESD verification challenges. Designers should consider adopting a newer automated ESD verification methodology to effectively and accurately address the challenges of ESD robustness in 3D designs. Ensuring accurate and consistent 3D ESD protection raises the reliability and product life of these products, ensuring they deliver the value and functionality the market demands.
Author
Dina Medhat is a principal technologist and technical lead for Calibre Design Solutions at Siemens EDA, a part of Siemens Digital Industries Software. She has held multiple product and technical marketing roles in Siemens EDA. She received her B.Sc., M.Sc., and Ph.D. degrees from Ain Shams University in Cairo, Egypt. She coauthored a book chapter in Reliability Characterisation of Electrical and Electronic Systems, (Jonathan Swingler, Editor—Elsevier, 2015). In addition to over 45 publications, she holds a U.S. patent. Her research interests include reliability verification, electrostatic discharge, emerging technologies, 3D integrated circuits, and physical verification.
Also Read:
Signal Integrity Verification Using SPICE and IBIS-AMI
Propelling DFT to New Levels of Coverage
AI-Driven DRC Productivity Optimization: Insights from Siemens EDA’s 2025 TSMC OIP Presentation