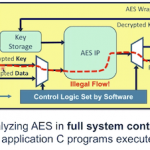
It should be no surprise in the current climate that the US government is ramping up investment in microelectronics security, particularly with an eye on China and investments they are making in the same area. This has two major thrusts as I read it: to ensure trusted and assured microelectronics are being used in US defense systems… Read More
Tag: radix-s
Digging Deeper in Hardware/Software Security
When it comes to security we’re all outraged at the manifest incompetence of whoever was most recently hacked, leaking personal account details for tens of millions of clients and everyone firmly believes that “they” ought to do better. Yet as a society there’s little evidence beyond our clickbait Pavlovian responses that we’re… Read More
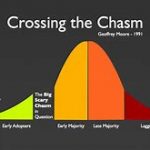
Tortuga Crosses a Chasm
I assume you know the Geoffrey Moore “crossing the chasm” concept, jumping from early stage enthusiasts trying your product because they’ll try anything new, to expanding to a mainstream and intrinsically more critical audience – a much tougher proposition. I’d argue there may be more than one of these transitions in the… Read More
Can I Trust my Hardware Root of Trust?
Hardware Roots of Trust (HRoTs) have become a popular mechanism to provide a foundational level of security in a cell-phone or IoT device or indeed any device that might appear to a hacker to be a juicy target. The concept is simple. In order to offer credible levels of security, any level in the stack has to be able to trust that levels… Read More