For decades, One-Time Programmable (OTP) memory has been viewed as a foundational element of hardware security. Because OTP can be written only once and cannot be modified afterward, it has traditionally been trusted to store cryptographic keys, secure boot code, device identity, and configuration data. Permanence was often… Read More
Tag: puf
Synopsys Design IP for Modern SoCs and Multi-Die Systems
Semiconductor intellectual property (IP) plays a critical role in modern system-on-chip (SoC) designs. That’s not surprising given that modern SoCs are highly complex designs that leverage already proven building blocks such as processors, interfaces, foundational IP, on-chip bus fabrics, security IP, and others. This… Read More
Synopsys SNUG Silicon Valley Conference 2024: Powering Innovation in the Era of Pervasive Intelligence
After the leadership transition at the top, Synopsys had just a little more than two months before the company’s flagship event, the Synopsys User Group (SNUG) conference. The Synopsys user community and entire ecosystem were waiting to hear new CEO Sassine Ghazi’s keynote to learn where the company is going and its strategic … Read More
How Do You Future-Proof Security?
If you are designing electronics to go into a satellite or a military drone, it better have a useful lifetime of 15-20 years or more. Ditto for the grid or other critical infrastructure, your car, medical devices, anything where we demand absolute reliability. Reliability also requires countermeasures against hacking by anyone… Read More
Enlisting Entropy to Generate Secure SoC Root Keys
Most methods of securing SOCs involve storing a root key that provides the basis of all derived keys and encryption of communication. The weakness with these methods is that even if the root key is stored in secure non-volatile memory, there are often methods to read the key. Once a key has been divulged the device can be cloned and … Read More
Using PUFs for Random Number Generation
In our daily lives, few of us if any, would want randomness to play any role. We look for predictability in order to plan our lives. But reality is that random numbers have been playing a role in our lives for a long time. The more conspicuous use cases of random numbers are with key fobs, and nowadays mobile phones. And then there are a … Read More
Quantum Computing and Threats to Secure Communication
There is never a dearth of new terms, discoveries and inventions in the technological world. And sometimes existing terms get reinvigorated. And debates ensue. The debaters argue about the plusses and minuses and make some predictions. Such is the case with “Quantum Computing.” I recently watched and listened to a webinar that… Read More
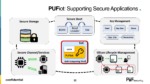
Upcoming Webinar: PUFiot, A NeoPUF-based Secure Co-Processor
Throughout history, people have sought after security as a basic right and expectation within a civilized society. Even as recent as a few centuries ago, things were very simple. Subjects looked to their rulers to provide security for their lives and assets. Assets were mostly hard assets such as jewelry, coins or real estate. … Read More
Quantum Tunneling for OTPs, PUFs: Higher security
I’ve had a number of enjoyable discussions with John East who ran Actel until it was acquired. (John and Actel devices also play an important role in my book, The Tell-Tale Entrepreneur.) This is relevant because Actel were well-known for their anti-fuse FPGAs. eMemory Technology, the subject of this blog, also produce an anti-fuse… Read More
The Best Way to Keep a Secret
Anyone knows that the best way to keep a secret is never to share it with anyone. Which works fine for your own most personal secrets, but it’s not very useful when you have to share with at least one other, such as in cyber-security. One such need, of enormous importance in the IoT, is authentication; are you who you claim to be? Seas of… Read More