You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
Security has been a domain blessed with an abundance of methods to improve in various ways, not so much in methods to measure the effectiveness of those improvements. With the best will in the world, absent an agreed security measurement, all those improvement techniques still add up to “trust me, our baby monitor camera is really… Read More
It should be no surprise in the current climate that the US government is ramping up investment in microelectronics security, particularly with an eye on China and investments they are making in the same area. This has two major thrusts as I read it: to ensure trusted and assured microelectronics are being used in US defense systems… Read More
When it comes to security we’re all outraged at the manifest incompetence of whoever was most recently hacked, leaking personal account details for tens of millions of clients and everyone firmly believes that “they” ought to do better. Yet as a society there’s little evidence beyond our clickbait Pavlovian responses that we’re… Read More
Hardware Roots of Trust (HRoTs) have become a popular mechanism to provide a foundational level of security in a cell-phone or IoT device or indeed any device that might appear to a hacker to be a juicy target. The concept is simple. In order to offer credible levels of security, any level in the stack has to be able to trust that levels… Read More
One of the challenges in the RISC-V bid for world domination may be security. That may seem like a silly statement, given that security weaknesses are invariably a function of implementation and RISC-V doesn’t define implementation, only the instruction-set architecture (ISA). But bear with me. RISC-V success depends heavily… Read More
A root of trust, particularly a hardware root of trust, has become a central principle in well-architected design for security. The idea is that higher layers in the stack, from drivers and OS up to applications and the network, must trust lower layers. What does it help it to build great security into a layer if it can be undermined… Read More
You’ve heard about Meltdown and Spectre and you know they’re really bad security bugs (in different ways). If you’ve dug deeper, you know that these problems are related to the speculative execution common in modern processors, and if you dug deeper still you may have learned that underlying both problems are exploits called timing… Read More
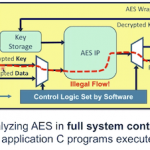
I first met Jason Oberg, CEO and one of the co-founders of Tortuga Logic, several years ago when I was still at Atrenta. At that time Jason and Jonny Valamehr (also a co-founder and the COO) were looking for partners. The timing wasn’t right, but we’ve stayed in touch, for my part because their area of focus (security) is hot and likely… Read More
We have become accustomed to the idea that safety expectations can’t be narrowed down to one thing you do in design. They pervade all aspects of design from overall process through analysis, redundancies in design, fault analytics and mitigation for faults and on-board monitors for reliability among other requirements and techniques.… Read More