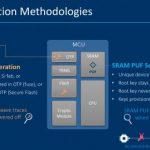
Designing for secure computation and communication has become a crucial requirement across all electronic products. It is necessary to identify potential attack surfaces and integrate design features to thwart attempts to obtain critical data and/or to access key intellectual property. Critical data spans a wide variety… Read More
Tag: iot security
IoT Devices Can Kill and What Chip Makers Need to Do Now
After the onslaught of IoT devices Christmas brought to the masses we really need to talk about security or lack thereof. Do me a favor and count how many IoT devices you have now? Our house IoT count is probably a bit higher than average due to my technology addiction but we are firmly in the double digits and the security breach stories… Read More
IoT Security Process Variation to the Rescue
Unique device identities are at the core of all computer security systems. Just as important is that each unique identity cannot be copied, because once copied they can be used illegitimately. Unique device IDs are used to ensure that communications are directed to the correct device. And they also provide the ability to encrypt… Read More
How many engineers does it take to get an IoT security certificate?
Spoiler alert, the answer is none!
Let me take you back to the beginning to explain that answer.
For the sake of this discussion, I will reduce a complex IoT solution to three fundamental blocks:
- IoT node
- IoT Gateway
- IoT Server
The IoT node is a sensor that converts analog, physical world context into digital data. The node has to have… Read More
Presto Engineering – Outsourced Secure Provisioning – Even Their Secrets Have Secrets
When I first heard about Presto Engineering I was enamored by a statement on their web site that claimed that one of their secured solutions included, “The ability to incorporate your secrets without knowing them”. If Mr. Spock would have been in the room his eyebrow would have certainly raised. Indeed, what does that statement … Read More
Intrinsix Fields Ultra-Low Power Security IP for the IoT Market
As the Internet-of-Things (IoT) market continues to grow, the industry is coming to grips with the need to secure their IoT systems across the entire spectrum of IoT devices (edge, gateway, and cloud). One need only look back to the 2016 distributed denial-of-service (DDoS) attacks that caused internet outages for major portions… Read More
Overcoming the Challenges of Creating Custom SoCs for IoT
As the Internet of Things (IoT) opportunities continues to expand, companies are working hard to bring System-on-Chip (SoC) solutions to market in the hopes of garnering market share and revenue. However, it’s not as easy as it may first seem. Companies are running into a series of issues that stand between them and capturing the… Read More
IoT and Blockchain Convergence
The Internet of Things (IoT) as a concept is fascinating and exciting, but one of the major challenging aspects of IoT is having a secure ecosystem encompassing all building blocks of IoT-architecture. Understanding the different building blocks of IoT, identifying the areas of vulnerability in each block and exploring technologies… Read More
IoT and a few of my favourite things
I was at the 27th Hewlett Packard Colloquium on Information Security at Royal Holloway, University of London this week and met Alan Stockey of RiskingIT.com. Alan told me about a little ditty he wrote on IoT security to the tune of “My Favourite Things” from the Sound of Music. Amused me and he’s allowed me to share… Read More
Predictions for the IOT in 2017
Although we are a far cry from Nostradamus, there are some fairly reliable predictions that can be made about 2017 and beyond.
The first bold prediction is that 2017 will see a bump in security, and a demand for skilled workers. Since there will be a growing demand for AI and the containers that are utilized to transmit information,… Read More