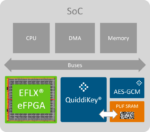
Semiconductor intellectual property (IP) plays a critical role in modern system-on-chip (SoC) designs. That’s not surprising given that modern SoCs are highly complex designs that leverage already proven building blocks such as processors, interfaces, foundational IP, on-chip bus fabrics, security IP, and others. This… Read More
Tag: intrinsic id
Synopsys SNUG Silicon Valley Conference 2024: Powering Innovation in the Era of Pervasive Intelligence
After the leadership transition at the top, Synopsys had just a little more than two months before the company’s flagship event, the Synopsys User Group (SNUG) conference. The Synopsys user community and entire ecosystem were waiting to hear new CEO Sassine Ghazi’s keynote to learn where the company is going and its strategic … Read More
Podcast EP131: Intrinsic ID – Implementing Security Across the Electronics Ecosystem
Dan is joined by Pim Tuyls, CEO of Intrinsic ID. Pim founded the company in 2008 as a spinout from Philips Research. With more than 20 years of experience in semiconductors and security, Pim is widely recognized for his work in the field of SRAM PUF and security for embedded applications. He speaks at technical conferences and has… Read More
WEBINAR: Taking eFPGA Security to the Next Level
We have written about eFPGA and for six years now and security even longer so it is natural to combine these two very important topics. Last month we covered the partnership between Flex Logix and Intrinsic ID, and the related white paper. Both companies are SemiWiki partners, so we were able to provide more depth and color:
In the … Read More
Flex Logix Partners With Intrinsic ID To Secure eFPGA Platform
While the ASIC market has always had its advantages over alternate solutions, it has faced boom and bust cycles typically driven by high NRE development costs and time to market lead times. During the same time, the FPGA market has been consistently bringing out more and more advanced products with each new generation. With very… Read More
Security Requirements for IoT Devices
Designing for secure computation and communication has become a crucial requirement across all electronic products. It is necessary to identify potential attack surfaces and integrate design features to thwart attempts to obtain critical data and/or to access key intellectual property. Critical data spans a wide variety… Read More
WEBINAR: How to add a NIST-Certified Random Number Generator to any IoT device?
In the first half of 2021, the number of attacks on IoT devices more than doubled to 1.5 billion attacks in just six months. These attacks target some typical weaknesses, such as the use of weak passwords, lack of regular patches and updates, insecure interfaces, and insufficient data protection. However, researchers from Bishop… Read More
Using PUFs for Random Number Generation
In our daily lives, few of us if any, would want randomness to play any role. We look for predictability in order to plan our lives. But reality is that random numbers have been playing a role in our lives for a long time. The more conspicuous use cases of random numbers are with key fobs, and nowadays mobile phones. And then there are a … Read More
Quantum Computing and Threats to Secure Communication
There is never a dearth of new terms, discoveries and inventions in the technological world. And sometimes existing terms get reinvigorated. And debates ensue. The debaters argue about the plusses and minuses and make some predictions. Such is the case with “Quantum Computing.” I recently watched and listened to a webinar that… Read More
Podcast EP20: How to Secure Any Chip. Any Time. Any Place
Dan is joined by Pim Tuyls, founder and CEO of Intrinsic ID. Pim provides background on what a physically unclonable function (PUF) is and how Intrinsic ID developed the technology around SRAMs that are found on virtually all chips. Pim discusses the multiple applications for SRAM PUFs and how they are implemented. He concludes… Read More